

16 Trending Cyber Security Seminar Topics for 2023

Cybersecurity is securing computer systems from unauthorized access, theft, damage, and other internet-based threats using modern technologies.
Also, it helps you maintain the confidentiality and integrity of the data so that the user’s privacy isn’t compromised.
We know, in this modern world where we need the internet in our daily lives, how important it is to know about cybersecurity and let others know, and the best way to let others know is through a seminar.
So, let’s discover 16 trending ybersecurity seminar topics.
16 Updated seminar presentation topics on cybersecurity
Let’s get to know the best seminar topics on cyber security, which will help you spread awareness about the topic.
1. The rise of ransomware: detection, prevention, and response strategies
Ransomware is one of the most dangerous malicious software mostly used by cybercriminals. These cyberweapons encrypt an organization’s data, and the criminal demands money from the company to receive the decryption key.
Possible topics you may include in your seminar presentation:
- Why the rate and the scale of ransomware attacks are increasing
- Types of ransomware
- Examples of high-profile ransomware attacks
- Role of using anti virus software to protect from ransomware attacks
- Ransomware detection and prevention strategies
2. Cybersecurity for small businesses: best practices and cost-effective solutions
Cybercriminals often target small businesses because of the less competent cybersecurity mechanism and an acute lack of data backup and protection knowledge.
Possible topics to cover in the seminar presentation:
- What are the primary cyber attack types that small businesses often face?
- Share recent examples of cyber attacks against small businesses
- How to implement a risk management framework?
- Role of cybersecurity training programs to spread awareness
- Introduction to cybersecurity regulations and standards such as GDPR and HIPAA
- Cybersecurity best practices for small businesses
3. Artificial intelligence in cybersecurity: opportunities and risks
Artificial intelligence is feeding data to a system and making it capable of doing a few things automatically without much human intervention.
It requires intense knowledge of computer science, programming, coding, etc. It is an ever-evolving field that has now started revolutionizing the cybersecurity field, also.
- The opportunities and threats of implementing AI in cybersecurity
- Introduction to deep learning and cyber security
- Examples of NLP applications in cybersecurity
- How AI is used in incident response, including automated incident analysis and response
- Explain how AI is changing the grand landscape of threats
Find the best seminar topics for computer science for final-year students .
4. The future of passwords: alternatives and innovations for secure authentication
Passwords are the oldest forms of securing a digital asset or a device. However, with the passing of time and the advent of cyber criminals, passwords have become easy to crack, insecure, and inconvenient.
Thus, there was a demand for alternative methods of securing a device. Face locks, iris scanners, and fingerprint sensors answered the demands.
Possible topics to cover in this seminar:
- Introduction to password-based authentication
- Explanation and examples of biometric authentication
- How Multi-Factor Authentication (MFA) words
- Explanation of zero-trust security (with examples)
- Role of continuous authentication and blockchain-based authentication
5. Cybersecurity and IoT: challenges and solutions
The Internet of Things (IoT) , better known as IoT, refers to the network of devices, vehicles, buildings, and anything with electro and software embedded to exchange data. IoT devices are increasing with changing times, and these devices are susceptible to cyber-attacks.
Sub-topics to cover in your seminar on cyber security and IoT:
- Introduction to cybersecurity threats and vulnerabilities faced by IoT devices
- Highlight common security challenges faced by IoT devices including lack of encryption.
- How to maintain the end-to-end security of these devices
- Emerging IoT security technologies
- Recommend cybersecurity leadership training programs to the audience
6. Ethical hacking: testing the security of your systems
Ethical hacking is a way of gaining authority over a computer by legal means. It is opposite to what people mean by regular hacking. Nevertheless, it is a practice that is prevalent in defence organizations all around the world, especially in the cybercrime branch.
You may include the following topics in the seminar:
- Introduction to ethical hacking and malicious hacking
- Highlight types of ethical hacking such as penetration testing, vulnerability scanning, etc.
- How ethical hacking works
- Web Application Security Project (OWASP) methodology
- Types of ethical hacking tools like network scanners, vulnerability scanners, etc.
7. Cybersecurity in the cloud: risks and strategies for protection
Data storage in the cloud is backing up data not in your hard drives but on the internet or in the servers and systems of some other company. Google Drive is an excellent example of cloud storage.
Nowadays, the cloud is a place for storage, computing, and other intellectual work.
- Companies based on cloud technologies
- Introduction to Cloud Service Provider (CSP) security
- Help companies assess the potential risks associated with the cloud environment
- How companies can presevnt cybersecurity issues
📌 Relevant pick for you: Cybersecurity advantages and disadvantages
8. The human factor in cybersecurity: addressing insider threats and social engineering
One of the weakest links when discussing cybersecurity is human negligence and human error, which leads to significant scale loss of revenue for a company due to data breaches and cyber-attacks. However, there are different ways employers can consider when training their employees about cybersecurity.
The employer can conduct a seminar to discuss a few points:
- How critical cybersecurity is for the company?
- Help people better understand the internet’s potential risks and threats
- Types of human-related security incidents such as insider threats, social engineering attacks, and phishing.
9. Cybercrime and law enforcement: cooperation and challenges
With the increasing number of cybercrime cases worldwide, the laws surrounding the correct use of the internet and giving justice to people and businesses who are victims of cyberattacks have become pretty tough.
However, every country has a vigilant cyber crime department that keeps a keen eye on the cybersecurity affairs of both attacks inside and outside the country.
Topics you may cover:
- What kind of cyber-attacks does the business face or may face in the future?
- Law enforcement in investigating cybercrime
- Introduction to government’s policies and laws for cybersecurity
- Best practices to prevent strategies for cybercrime
📌 Further resources on cyber security:
- What is cloning in cyber security?
- What is shimming in cyber security?
- Is cybersecurity hard to learn for a beginner?
- What is spooling in cyber security (with pros & cons)
- Handpicked cyber security training classes in Mumbai
10. Cryptography: The science behind data protection
Cryptography is the practice of encrypting data and then decrypting it. It is one of the most prominent cybersecurity domains and a fascinating subject.
Cryptography helps secure your data and prevents cybercriminals from catching your data midway, and even if the person gets the data, he won’t get any information because of the encryption.
Instead, the criminal will require a decryption key. Cryptography also helps in the production of the decryption key.
The seminar may cover topics:
- Introduction to cryptography and its application
- Explain encryption algorithms, decryption algorithms, and keys
- Explain techniques, such as symmetric-key cryptography, public-key cryptography, and hash functions
- Cryptographic Protocols and standards
11. Zero Trust Architecture: Reimagining network security
Zero Trust Architecture, or ZTA, is a security model that grants permission to no users and devices without proper authentication. As a result, it is a highly secure network and doesn’t allow malicious attacks.
As traditional perimeter-based security techniques are becoming obsolete with changing times, ZTA is the way to go. Thus, a seminar is crucial to make people:
- Aware of the technology
- Explain zero trust network access (ZTNA)
- Introduction to Zero Trust security and how it works
- Types of ZTA models and their benefits
- Best practices for implementing the ZTA
12. Biometric authentication: challenges and opportunities
Biometric authentication is not a technology for the future. It has been there for many years and constantly evolving, like fingerprinting, facial recognition, and iris scanner.
However, not only does the authentication model have numerous benefits but also many challenges.
Topics you may cover in your presentation:
- Potential vulnerabilities linked to biometric authentication
- Best practices for implementing biometric authentication
- Types and benefits of biometric authentication
- How do biometrics work for authentication?
13. Cyber insurance: understanding policies and coverage
Because of awareness, most people worldwide don’t know they can be insured against cyber threats. Cyber-attacks are rampant in this modern world, cyber-attacks are rampant, and their risks include potential losses. To reduce the damage and losses, a seminar is essential.
A seminar on cyber insurance can help people become:
- Advantages, disadvantages, and types of cyber insurance
- Explanation to network security
- Computer data loss and restoration
- Market and future trends in cyber insurance
14. Quantum computing and cryptography: what’s the future?
Quantum computing is a revolutionary technology that has taken the world by storm. It helps in faster processing, more power, and speed.
However, quantum computing may pose a challenge to cryptographic systems, and many people are unaware of it.
Topics to cover:
- Explanation of how quantum computing poses a threat to traditional cryptographic systems
- Introduction to quantum key distribution
- Challenges in building a practical quantum computer
- Google’s quantum supremacy claim
15. Incident response and recovery: best practices for managing cyber attacks
Incident response and recovery plans are significant for tackling sophisticated cyber-attacks. Moreover, different kinds of cyber-attacks pose different levels of danger for an organization. Thus, the company must keep itself prepared for such a disastrous event.
Some topics to cover in this seminar:
- Best practices for managing a cyber-attack
- Explanation of the incident recovery process
- Highlight different phases of cybersecurity implementation
- Security information and event management (SIEM) systems
📌Relevant article: Do you need math skills to become a cybersecurity expert?
16. Cybersecurity in healthcare: best practices and compliance requirements
Healthcare is one of the essential departments of any country. It is essential and confidential, which shouldn’t go out into the hands of the public. But what will happen if there is a data breach in the system? What should the owners of the hospital know about?
The computer systems of healthcare departments should have robust cybersecurity systems. A seminar can make people:
- Possible cybersecurity threats in the healthcare industry
- Cybersecurity in healthcare laws and regulations
- Types of cyber-attacks in healthcare such as web application errors, System intrusions, etc.
- Introduction to HIPAA security rule
- Explanation of access control and authentication strategies for healthcare
Final words
Seminars are a great way to spread awareness about a particular event or to market your brand and product. It instantly impacts a lot of people, and knowledgeable people are the ones who bring change to this world.
Cybersecurity is an evolving field, and the more people become aware of it, the faster it grows.
We hope you’ll like this list of seminar topics on cyber security and nail your next seminar presentation.
10Pie Editorial Team is a team of certified technical content writers and editors with experience in the technology field combined with expert insights . Learn more about our editorial process to ensure the quality and accuracy of the content published on our website.

10Pie is your go-to resource hub to start and grow your Tech Career.
Send us your queries at [email protected]
CAREER GUIDES
- Data Science
- Cyber Security
- Cloud Computing
- Artificial Intelligence
- Business Intelligence
- Contributors
- Tech Glossary
- Editorial Policy
- Tech Companies
- CGPA to percentage calculator
- Write for us
- Privacy policy
📈 Tech career paths
- AI career paths
- Python career paths
- DevOps career paths
- Data engineer career paths
- Data science career paths
- Software testing career paths
- Software engineer career paths
🏆 Tech courses
- Cloud computing courses in Pune
- Data analytics courses in Hyderabad
- Data science courses in Mangalore
- Cloud computing courses in Hyderabad
- Data analytics courses in Indore
- Data analytics courses in Mumbai
- Data analytics courses in Pune
📌 Featured articles
- AI seminar topics
- Which tech career is right for me?
- Will AI replace software engineers?
- Top data annotation companies
- Cyber security career roadmap
- How Tesla uses Artificial Intelligence
- Cloud computing seminar topics
© 2023 All rights reserved. All content is copyrighted, republication is prohibited.

- Conferences
- Last updated August 6, 2024
- In AI Origins & Evolution
Top 10 Popular PPT in Cybersecurity Topics On Slideshare

- Published on August 12, 2019
- by Ambika Choudhury

Securing networks and protecting data from breaching has become one of the crucial motives in an organisation. Cybercrime has eventually risen with the widespread use of emerging technologies and we have been witnessing data breaches and other hacks for a few years now. In this article, we list down 10 popular presentations on cybersecurity one must read on Slideshare.
1. Artificial Intelligence And Cybersecurity
This presentation was published in March 2019 by Olivier Busolini, a cybersecurity professional who also works with AI in cybersecurity. This presentation includes a basic introduction to AI, an overview of AI technologies, an overview of machine learning underlying technologies, basics of deep learning, introduction to red and blue AI, emerging usages of blue AI, difficulties faced during developing AI solutions and tips for cybersecurity strategy.
2. Cyber Crime And Security
This powerpoint presentation was published by Lipsita Behera, a software developer and it has gathered more than 350,000 views till now. In this PPT, you can understand the basics of cybersecurity such as how cybersecurity emerged, know about cyber threat evolution, types of cybercrime, how to take preventive measures in order to control the threats, learn various security reasons as well as methods.
3. Cybersecurity
This presentation has got more than one lakh viewers and more than 700 clipping. Here, the author introduces the basics of cybersecurity and what is the actual need of cybersecurity, what are the major security problems, different viruses and worms and its solutions, brief introduction of hackers and measures to prevent hacking, what are malware and steps to stop malware, what are trojan horses and safety measures to avoid trojans, password cracking and securing password, cybersecurity strategy in India and much more.
4| Combating cybersecurity Using Artificial Intelligence
Combating Cybersecurity using Artificial Intelligence was published in January this year by Inderjeet Singh, Director – Strategic Accounts. This presentation discusses the threats with AI and machine learning. Here, you can learn about the advanced behavioural attacks, applications of emerging technologies in cybersecurity, various malicious activities, including the future of AI and machine learning in cybersecurity.
5. Cyber Crime And Security
This powerpoint presentation was published by Aeman Khan, an automation test engineer and it has crossed over 410,000 views till now. Here, the writer discusses the basics of cybersecurity such as its introduction, history, the various categories of cybercrime, its types, how cybersecurity threatens national security, advantages of cybercrime and other safety tips to cybercrimes including cyber law in India.
6. Cybersecurity
This ppt is published by Bijay Bhandari, an engineer and project manager by profession. It has been viewed for over 210,000 times where the author discusses how to take action against cybercrime. You will know about the basics of cybersecurity and cybercrime, what constitutes cyber crimes, protection measures for cybercrime, advantages of cybersecurity and various safety measures.
7. Cyber Crime
This presentation has been viewed for over 294,000 times and it includes a basic introduction to cybercrime. You will get to know about the variants of cybercrime such as phishing, vishing, cyberstalking, cost of cybercrime in India, cyber laws, various ACTs including the preventive measures for such activities.
8. Overview Of Artificial Intelligence In cybersecurity
This presentation, an overview of artificial intelligence in cybersecurity was published in June 2019 by Olivier Busolini, a cybersecurity professional. Here, he talks about artificial imitation augmented intelligence, basic types of AI and machine learning, difficulties to develop AI solutions, challenges in machine learning, AI in cybersecurity, key flaws of cybersecurity, AI risk framework, basic introduction to defensive AI, adversarial AI as well as offensive AI and much more.
9 . Security Automation And Machine Learning
The security automation and machine learning ppt is published by Siemplify, a security platform in January this year and has got more than 100 viewers. It includes a basic introduction to cybersecurity and machine learning, types of machine learning techniques, security analysis for machine learning, threats on machine learning, machine learning for prevention, detection, incident response and SOC management.
10. The Role Of Big Data, AI And ML In Cyber Intelligence
The role of big data, AI and ML in cyber intelligence ppt was published by Aladdin Dandis, an information security manager who gives a brief introduction to cyber intelligence, raw threat data and threat intelligence, understanding AI and machine learning drivers, various kinds of cybersecurity options such as phishing, anti-malware, fraud detection, cyber intelligence framework and its challenges.
📣 Want to advertise in AIM? Book here
Ambika Choudhury
- AI cybercrime , AI cybersecurity threat , cybercrime , Cybersecurity , data breaching , learn cybersecurity , ppt on cyber security

Google believes one of the important factors of GenAI’s impact is democratising information and enabling everyone to succeed in the digital economy.

Top Editorial Picks
Karthik Narain Succeeds Paul Daugherty as Accenture’s New CTO Siddharth Jindal
OLMoE Achieves State-Of-The-Art Performance using Fewer Resources and MoE Sagar Sharma
AI Music Generator Model, FluxMusic To Bridge The Gap Between Language and Music Composition Tanisha Bhattacharjee
Groq Unveils LLaVA V1.5 7B, Faster than OpenAI GPT-4o Siddharth Jindal
Zerodha Co-founder Nikhil Kamath Unveils ‘Innovators Under 25’ to Support Young Tech and AI Entrepreneurs in India Vandana Nair
Subscribe to The Belamy: Our Weekly Newsletter
Biggest ai stories, delivered to your inbox every week., "> "> flagship events.
Discover how Cypher 2024 expands to the USA, bridging AI innovation gaps and tackling the challenges of enterprise AI adoption
© Analytics India Magazine Pvt Ltd & AIM Media House LLC 2024
- Terms of use
- Privacy Policy
Subscribe to Our Newsletter
The Belamy, our weekly Newsletter is a rage. Just enter your email below.
Subscribe to Our Youtube channel

105 Latest Cyber Security Research Topics in 2024
Home Blog Security 105 Latest Cyber Security Research Topics in 2024
The concept of cybersecurity refers to cracking the security mechanisms that break in dynamic environments. Implementing Cyber Security Project topics and cybersecurity thesis topics helps overcome attacks and take mitigation approaches to security risks and threats in real-time. Undoubtedly, it focuses on events injected into the system, data, and the whole network to attack/disturb it.
The network can be attacked in various ways, including Distributed DoS, Knowledge Disruptions, Computer Viruses / Worms, and many more. Cyber-attacks are still rising, and more are waiting to harm their targeted systems and networks. Detecting Intrusions in cybersecurity has become challenging due to their Intelligence Performance. Therefore, it may negatively affect data integrity, privacy, availability, and security.
This article aims to demonstrate the most current Cyber Security Research Topics for Projects and areas of research currently lacking. We will talk about cyber security research questions, cyber security topics for the project, latest research titles about cyber security.
List of Trending Cyber Security Research Topics in 2024
Digital technology has revolutionized how all businesses, large or small, work, and even governments manage their day-to-day activities, requiring organizations, corporations, and government agencies to utilize computerized systems. To protect data against online attacks or unauthorized access, cybersecurity is a priority. There are many Cyber Security Courses online where you can learn about these topics. With the rapid development of technology comes an equally rapid shift in Cyber Security Research Topics and cybersecurity trends, as data breaches, ransomware, and hacks become almost routine news items. In 2024, these will be the top cybersecurity trends .
A. Exciting Mobile Cyber Security Research Paper Topics
- The significance of continuous user authentication on mobile gadgets.
- The efficacy of different mobile security approaches.
- Detecting mobile phone hacking.
- Assessing the threat of using portable devices to access banking services.
- Cybersecurity and mobile applications.
- The vulnerabilities in wireless mobile data exchange.
- The rise of mobile malware.
- The evolution of Android malware.
- How to know you’ve been hacked on mobile.
- The impact of mobile gadgets on cybersecurity.
B. Top Computer and Software Security Topics to Research
- Learn algorithms for data encryption
- Concept of risk management security
- How to develop the best Internet security software
- What are Encrypting Viruses- How does it work?
- How does a Ransomware attack work?
- Scanning of malware on your PC
- Infiltrating a Mac OS X operating system
- What are the effects of RSA on network security ?
- How do encrypting viruses work?
- DDoS attacks on IoT devices
C. Trending Information Security Research Topics
- Why should people avoid sharing their details on Facebook?
- What is the importance of unified user profiles?
- Discuss Cookies and Privacy
- White hat and black hat hackers
- What are the most secure methods for ensuring data integrity?
- Talk about the implications of Wi-Fi hacking apps on mobile phones
- Analyze the data breaches in 2024
- Discuss digital piracy in 2024
- critical cyber-attack concepts
- Social engineering and its importance
D. Current Network Security Research Topics
- Data storage centralization
- Identify Malicious activity on a computer system.
- Firewall
- Importance of keeping updated Software
- wireless sensor network
- What are the effects of ad-hoc networks
- How can a company network be safe?
- What are Network segmentation and its applications?
- Discuss Data Loss Prevention systems
- Discuss various methods for establishing secure algorithms in a network.
- Talk about two-factor authentication
E. Best Data Security Research Topics
- Importance of backup and recovery
- Benefits of logging for applications
- Understand physical data security
- Importance of Cloud Security
- In computing, the relationship between privacy and data security
- Talk about data leaks in mobile apps
- Discuss the effects of a black hole on a network system.
F. Important Application Security Research Topics
- Detect Malicious Activity on Google Play Apps
- Dangers of XSS attacks on apps
- Discuss SQL injection attacks.
- Insecure Deserialization Effect
- Check Security protocols
G. Cybersecurity Law & Ethics Research Topics
- Strict cybersecurity laws in China
- Importance of the Cybersecurity Information Sharing Act.
- USA, UK, and other countries' cybersecurity laws
- Discuss The Pipeline Security Act in the United States
H. Recent Cyberbullying Topics
- Protecting your Online Identity and Reputation
- Online Safety
- Sexual Harassment and Sexual Bullying
- Dealing with Bullying
- Stress Center for Teens
I. Operational Security Topics
- Identify sensitive data
- Identify possible threats
- Analyze security threats and vulnerabilities
- Appraise the threat level and vulnerability risk
- Devise a plan to mitigate the threats
J. Cybercrime Topics for a Research Paper
- Crime Prevention.
- Criminal Specialization.
- Drug Courts.
- Criminal Courts.
- Criminal Justice Ethics.
- Capital Punishment.
- Community Corrections.
- Criminal Law.
Cyber Security Future Research Topics
- Developing more effective methods for detecting and responding to cyber attacks
- Investigating the role of social media in cyber security
- Examining the impact of cloud computing on cyber security
- Investigating the security implications of the Internet of Things
- Studying the effectiveness of current cyber security measures
- Identifying new cyber security threats and vulnerabilities
- Developing more effective cyber security policies
- Examining the ethical implications of cyber security
Cyber Security Topics For Research Paper
- Cyber security threats and vulnerabilities
- Cyber security incident response and management
- Cyber security risk management
- Cyber security awareness and training
- Cyber security controls and countermeasures
- Cyber security governance
- Cyber security standards
- Cyber security insurance
Top 5 Current Research Topics in Cybersecurity
Below are the latest 5 cybersecurity research topics. They are:
- Artificial Intelligence
- Digital Supply Chains
- Internet of Things
- State-Sponsored Attacks
- Working From Home
Research Area in Cyber Security
The field of cyber security is extensive and constantly evolving. Its research covers a wide range of subjects, including:
- Quantum & Space
- Data Privacy
- Criminology & Law
- AI & IoT Security
- RFID Security
- Authorization Infrastructure
- Digital Forensics
- Autonomous Security
- Social Influence on Social Networks
How to Choose the Best Research Topics in Cyber Security?
A good cybersecurity assignment heading is a skill that not everyone has, and unfortunately, not everyone has one. You might have your teacher provide you with the topics, or you might be asked to come up with your own. If you want more cyber security research topics, you can take references from Certified Ethical Hacker Certification, where you will get more hints on new topics. If you don't know where to start, here are some tips. Follow them to create compelling cybersecurity assignment topics.
1. Brainstorm
In order to select the most appropriate heading for your cybersecurity assignment, you first need to brainstorm ideas. What specific matter do you wish to explore? In this case, come up with relevant topics about the subject and select those relevant to your issue when you use our list of topics. You can also go to cyber security-oriented websites to get some ideas. Using any blog post on the internet can prove helpful if you intend to write a research paper on security threats in 2024. Creating a brainstorming list with all the keywords and cybersecurity concepts you wish to discuss is another great way to start. Once that's done, pick the topics you feel most comfortable handling. Keep in mind to stay away from common topics as much as possible.
2. Understanding the Background
In order to write a cybersecurity assignment, you need to identify two or three research paper topics. Obtain the necessary resources and review them to gain background information on your heading. This will also allow you to learn new terminologies that can be used in your title to enhance it.
3. Write a Single Topic
Make sure the subject of your cybersecurity research paper doesn't fall into either extreme. Make sure the title is neither too narrow nor too broad. Topics on either extreme will be challenging to research and write about.
4. Be Flexible
There is no rule to say that the title you choose is permanent. It is perfectly okay to change your research paper topic along the way. For example, if you find another topic on this list to better suit your research paper, consider swapping it out.
The Layout of Cybersecurity Research Guidance
It is undeniable that usability is one of cybersecurity's most important social issues today. Increasingly, security features have become standard components of our digital environment, which pervade our lives and require both novices and experts to use them. Supported by confidentiality, integrity, and availability concerns, security features have become essential components of our digital environment.
In order to make security features easily accessible to a wider population, these functions need to be highly usable. This is especially true in this context because poor usability typically translates into the inadequate application of cybersecurity tools and functionality, resulting in their limited effectiveness.
Cyber Security Research Topic Writing Tips from Expert
Additionally, a well-planned action plan and a set of useful tools are essential for delving into Cyber Security research topics. Not only do these topics present a vast realm of knowledge and potential innovation, but they also have paramount importance in today's digital age. Addressing the challenges and nuances of these research areas will contribute significantly to the global cybersecurity landscape, ensuring safer digital environments for all. It's crucial to approach these topics with diligence and an open mind to uncover groundbreaking insights.
- Before you begin writing your research paper, make sure you understand the assignment.
- Your Research Paper Should Have an Engaging Topic
- Find reputable sources by doing a little research
- Precisely state your thesis on cybersecurity
- A rough outline should be developed
- Finish your paper by writing a draft
- Make sure that your bibliography is formatted correctly and cites your sources.
Discover the Power of ITIL 4 Foundation - Unleash the Potential of Your Business with this Cost-Effective Solution. Boost Efficiency, Streamline Processes, and Stay Ahead of the Competition. Learn More!
Studies in the literature have identified and recommended guidelines and recommendations for addressing security usability problems to provide highly usable security. The purpose of such papers is to consolidate existing design guidelines and define an initial core list that can be used for future reference in the field of Cyber Security Research Topics.
The researcher takes advantage of the opportunity to provide an up-to-date analysis of cybersecurity usability issues and evaluation techniques applied so far. As a result of this research paper, researchers and practitioners interested in cybersecurity systems who value human and social design elements are likely to find it useful. You can find KnowledgeHut’s Cyber Security courses online and take maximum advantage of them.
Frequently Asked Questions (FAQs)
Businesses and individuals are changing how they handle cybersecurity as technology changes rapidly - from cloud-based services to new IoT devices.
Ideally, you should have read many papers and know their structure, what information they contain, and so on if you want to write something of interest to others.
Inmates having the right to work, transportation of concealed weapons, rape and violence in prison, verdicts on plea agreements, rehab versus reform, and how reliable are eyewitnesses?
The field of cyber security is extensive and constantly evolving. Its research covers various subjects, including Quantum & Space, Data Privacy, Criminology & Law, and AI & IoT Security.

Mrinal Prakash
I am a B.Tech Student who blogs about various topics on cyber security and is specialized in web application security
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Cyber Security Batches & Dates
| Name | Date | Fee | Know more |
|---|
Latest Topics in Cybersecurity | From Opportunity to Threat
Astrid Tran • 25 January, 2024 • 6 min read
What are the most pressing topics in Cybersecurity today?
In today's technologically advanced era, where we heavily rely on a digital ecosystem, the necessity to ensure robust cybersecurity measures is of critical significance. Cyber threats vary in nature, with a growing number of malicious actors constantly seeking to exploit vulnerabilities in our interconnected systems.
In this article, we delve into the most critical and latest topics in cybersecurity, aiming to educate and raise awareness about safeguarding sensitive data and maintaining digital privacy.
Table of Contents
Understanding the cybersecurity landscape.
- Cybercrime and Cyberattacks
- Data Breaches and Data Privacy
- Cloud Security
- IoT Security
- AI and ML in Cybersecurity
- Social Engineering Attacks
- The Role of Employees in Cybersecurity
Key Takeaways
The cybersecurity landscape constantly evolves, adapting to new threats and challenges. It is vital for businesses, individuals, and organizations to stay informed and proactive in their cybersecurity practices. By examining important aspects within the realm of cybersecurity, we can effectively counter risks and fortify our digital defenses.
#1. Cybercrime and Cyberattacks
It is one of the most important topics in cybersecurity. The rise of cybercrime has become a menace affecting businesses, governments, and individuals alike. Cybercriminals employ various tactics, such as malware, phishing, ransomware, and social engineering, to compromise systems and steal sensitive data.
The financial impact of cybercrime on business is staggering, with estimates suggesting that it will cost the global economy a staggering $10.5 trillion annually by 2025, according to Cybersecurity Ventures.

#2. Data Breaches and Data Privacy
Topics in Cybersecurity also cover Data breaches and privacy. In collecting data from customers, many companies promise strong data privacy. But the whole story is different. Data breaches happen, meaning much critical information is exposed, including personal identities, financial records, and intellectual property to unauthorized parties. And the question is, are all customers informed about it?
With a growing number of companies storing vast amounts of data, there is an urgent need to ensure strong actions to prevent confidential information from leaking. It comes along with Data privacy statistics from IBM Security reveal the severity of the situation; in 2020, the average cost of a data breach reached $3.86 million.
#3. Cloud Security
The adoption of cloud technologies has revolutionized the way businesses store and access data. However, this shift brings unique cybersecurity risks and interesting cybersecurity topics. Pandemics have promoted the golden era of remote working, it is possible for employees to work from anywhere at any time on any device. And more efforts are made to verify the identities of employees. Additionally, businesses are engaging with customers and partners in the cloud. This causes great concern about cloud security.
By 2025, it is predicted that 90% of organizations worldwide will utilize cloud services, necessitating robust cloud security measures, Gartner reported. Organizations must diligently address cloud security concerns, including data confidentiality, securing cloud infrastructure, and preventing unauthorized access. There is a trend of shared responsibility model , where the CSP is responsible for protecting its infrastructure while the cloud user is on the hook for protecting the data, applications, and access in their cloud environments.
#4. IoT Security
Main Topics in Cybersecurity? The rapid proliferation of Internet of Things (IoT) devices introduces a whole new set of cybersecurity challenges. With everyday objects now connected to the internet, vulnerabilities in IoT ecosystems open doors for cybercriminals to exploit.
In 2020, it estimated there are an average of 10 connected devices in every U.S. household. This research paper defined complex IoT environments as an interconnected web of at least 10 IoT devices. Although diversity provides users with a wide array of device options, it is also a contributing factor to the fragmentation of the IoT and comes with numerous security issues. For instance, malicious actors can target smart home devices, medical equipment, or even critical infrastructure. Ensuring stringent IoT security measures will be pivotal in preventing potential breaches.
#5. AI and ML in Cybersecurity
AI (Artificial Intelligence) and ML (Machine Learning) have transformed various industries significantly, including cybersecurity. Leveraging these technologies, cybersecurity professionals can detect patterns, anomalies, and potential threats with greater efficiency.
With the increasing utilization of machine learning (ML) algorithms in cybersecurity systems and cyber operations, we've observed the emergence of the following trends at the intersection of AI and cybersecurity:
- AI-informed defensive strategies show the potential to become the best cybersecurity measures against hacking operations.
- Explainable AI (XAI) models are making cybersecurity applications more secure.
- The democratization of AI inputs is lowering barriers to entry in automating cybersecurity practices.
There are the fears of AI replacing human expertise in cybersecurity, however, AI and ML systems can also be vulnerable to exploitation, requiring continuous monitoring and retraining to stay one step ahead of cybercriminals.
#6. Social Engineering Attacks
Social Engineering Attacks are among the interesting topics in cybersecurity that individuals encounter frequently. With the rise of sophisticated social engineering techniques, cybercriminals often exploit human inclination and trust. Through psychological manipulation, it deceives users into making security mistakes or giving away sensitive information. For example, phishing emails, phone scams, and impersonation attempts coerce unsuspecting individuals into divulging sensitive information.
Educating users about social engineering tactics and raising awareness is crucial to combat this pervasive threat. The most significant step is to calm down and ask for help from experts whenever you receive any emails or phones or warnings about the leaking information that requires you to send your password and credit cards.
#7. The Role of Employees in Cybersecurity
Hot topics in cybersecurity also mention the importance of employees in preventing cybercrimes. Despite the advancements in technology, human errors remain one of the most significant contributors to successful cyber attacks. Cybercriminals often exploit employees' lack of awareness or adherence to established cybersecurity protocols. The most common mistake is weak password setting which is easily exploited by cybercriminals.
Organizations need to invest in robust cybersecurity training programs to educate employees on recognizing potential threats, implementing strong password practices , public devices using, and understanding the importance of keeping software and devices up to date. Encouraging a culture of cybersecurity within organizations can significantly mitigate risks stemming from human errors.

Topics in cybersecurity are diverse and ever-evolving, highlighting the need for proactive measures to safeguard our digital lives. By prioritizing robust cybersecurity practices, organizations and individuals can mitigate risks, protect sensitive information, and prevent potential damages caused by cyber threats.
💡Stay vigilant, educate yourself and your teams, and continuously adapt to the dynamic cybersecurity landscape to preserve the integrity of our digital ecosystems. Prepare an engaging and interactive presentation with Ahaslides . We ensure your data privacy and security.

Astrid Tran
I've got my rhythm with words
Tips to Engage with Polls & Trivia
More from AhaSlides


- Security Awareness Training

14 Security Awareness Topics (Updated for 2024 to Include AI)

Parker Byrd
The prevalence of cyber-attacks has prompted many companies to invest in security awareness training programs . Security awareness training is a perfect way to prepare employees for the many types of attacks that can occur and how they should respond to them. A company's network, data, physical assets, and reputation are all at risk when an employee falls victim to one attack or another. Every company must invest in this type of program or else it will be unprepared for the future.
This blog post will examine some of the most common security awareness training topics, including phishing scams, social engineering, ransomware, and more. Educating your employees on these cyber security awareness topics will help your company stay secure, reduce human error, avoid data breaches, and become an overall security aware workforce.
14 Important Security Awareness Training Topics:
Physical Security
Mobile security, social engineering, working remotely, removable media, social media, safe web browsing, incident reporting.
- Artificial Intelligence
What Should Your Security Awareness Training Program Include?
Your Security Awareness Training program should be a combination of education, testing, and employee engagement.
Whether you're an IT administrator or the Chief Information Officer, you should be regularly engaging with your employees about security awareness. If you're simply sending phishing simulations and emails notifying employees of the training they need to complete, you risk creating more "security tension" than security awareness.
As far as the training itself, security awareness training is most effective when it's done in the form of video, interactive elements, and knowledge checks. If you're doing employee security awareness training regularly, you should also keep it short. Employees can learn a lot in 8-10 minutes if the training content is effective.
Finally, as with any solid cyber security awareness training campaigns, phishing simulations are a great way to identify ongoing risk in your company.
Security Awareness Training Topics to Cover

Phishing is a type of security threat that involves impersonating a trusted party in order to steal information. It is commonly portrayed as an email, either sent through the internet or over a company's intranet. It is also one of the most common cyber security awareness training topics.
Security awareness training for phishing involves teaching users how to recognize red flags in suspicious emails so they can avoid potentially giving away sensitive data and other security incidents.
Common phishing email red flags include misspellings in the email address, a sense of urgency to act on the request, and strange email addresses.
Phishing awareness training is a critical part of any security awareness program because it can be hard for users to identify when something is suspicious if they are not familiar with how attackers attempt to trick them into giving up sensitive data.
Ransomware is a security threat that encrypts files in a user's computer, then asks for money to un-encrypt them. This attack is typically paired with phishing emails, which are then emailed out and usually ask users to click on links within the phishing email.
Ransomware can come in many forms. Most commonly, it is hosted as malicious software on websites that users visit with their computers or smartphones. It locks up their files and the hackers demand a ransom to unlock them. It also comes in the form of phishing attacks that contain links or attachments that are designed to download a type of malicious software on a user's computer, which can then lock up their files and display a message demanding payment for release.
Ransomware has been around since 1989, but it wasn't until 2009 when bitcoin entered the scene and gave hackers an anonymous way to collect money that it gained popularity. Today, the WannaCry attack is estimated to have affected more than 200,000 computers worldwide.
To prevent ransomware attacks, employees should be trained to follow basic best practices, including:
- Don't open suspicious files or links.
- Keep software updated (especially operating systems and browsers)
- Use multi-factor authentication for all online accounts (Google accounts, online banking, social media platforms).
- Use a unique, secure password.
- If a computer is infected, disconnect it from the network immediately.
- Back up data regularly and encrypt files to prevent them from falling into hackers' hands.

Malware is a type of software that is designed to cause damage to a computer. It can be destructive or it can be used simply for information gathering, but it is always considered a security risk.
Types of malware include :
This is software that tracks the user's activity and sends the information to another computer without their knowledge. A lot of times, spyware companies will also add viruses or other malware to the computers they are tracking.
Ransomware.
Ransomware is malware that will encrypt a user's data and then demand payment for restoring access to the data.
Cryptocurrency mining malware.
This type of malware infects computers and then uses their processing power to mine cryptocurrencies, such as Bitcoin, without the owner's knowledge or permission.
Trojan horses.
Trojan horses are programs that appear harmless but actually contain malware. If a user installs the program, then the malware is installed without their knowledge.
Persistent spyware/malware.
Persistent spyware/malware follows a user using tracking software to monitor everything that they do on their computer or mobile device and sends that information back to whoever programmed it.
Employees should know how malware works and also be aware of what kind of files they are downloading on their computers. Employees should also have anti virus software on their computer.
Passwords keep our accounts secure, but they can also make it easy for hackers to gain access. With so many different passwords to remember, it's difficult for users to keep track of their security information and stay ahead. Password security awareness training teaches employees how they can create secure passwords that are more resistant to attacks from hackers.
Here are some tips to share for good password habits:
- Use a unique password for every account.
- Use a strong password.
- Avoid obvious passwords like your birthday, social security number, or other sensitive information.
- Limit the number of personal details you share on social media sites. This might make it easier for someone to guess your password or security questions.
- Use a combination of letters, numbers, and symbols. A little creativity also helps!
- Use multi-factor authentication.

Sometimes, in our quest to lock down our networks and avoid malware and viruses, it’s easy to forget about the physical world around us that can pose security threats Physical security flaws can put your personal information and your companies' sensitive data at risk just as much as a cyber attack.
It’s pretty common to assume that a data breach only comes from something like malware, ransomware, or a phishing email. However, to a hacker, it really doesn’t matter how they get your info. For that reason, it's important to communicate these lessons to your employees for physical security:
Tailgating is a real security issue that happens more often than we think. Sure, we all want to be kind and helpful but unless someone can show proof that they should be inside your office, the best solution is to say kindly “I’m sorry, I just can not let you in.”. Employees may run the risk of seeming unkind but it is better to be safe than sorry.
Likewise, leaving your device open and unattended invites would-be thieves to take what they want and go. Encourage employees to lock their devices and use solid passwords
Another physical security threat is open, written-down passwords and other sensitive information on sticky notes. Employees should find other ways to remember complex passwords like a password manager.
And finally, always be on guard when it comes to "shoulder surfing". You never know who is trying to steal your information. Always be aware of your surroundings before putting in sensitive information into your devices. While it may seem unlikely, even people you’ve worked with for years may be interested in your password.

The threat of mobile devices being hacked is becoming more and more common. As people's lives become more dependent on their smartphones, employers have to worry about the security surrounding these devices.
Whether it be a technical device or a handheld one, it is important for the employer to make sure that the information obtained through these mobile devices are protected from hacking.
There are also potential privacy issues of BYOD (bring your own device) and how it relates to data protection and corporate policies
BYOD has become a popular trend in the workplace environment due to a preference of personal devices, cost savings, and ease of use. However, it also has its potential security risks when employees sometimes bypass business data protection protocols in the name of convenience.
To keep mobile devices secure, employees should use strong passwords, refrain from using public Wi-Fi networks, and avoid downloading applications that are not secure.

In its simplest form, a social engineer is someone who uses their knowledge of human psychology to convince others to give up sensitive and confidential information or perform tasks they otherwise would not do.
The goal of a social engineering attacks is to get the user to fork over some sort of access token (passwords, pins, etc) or sensitive data by using social engineering tactics such as authority level, fear, greed or friendship.
The attacker might simply ask for a password to gain access, or try other tactics like asking victims to provide passwords that are then used later on in attacks against the company network.
Vishing is a form of phishing where the attackers use a phone call to accomplish their malicious goals. Using social engineers tactics like authority level, fear, greed or friendship the attacker might simply ask for a password to gain access like they would do in a phishing attempt.
Additionally, SMiSHing is a form of phishing where the attacker uses Short Message Service (SMS) messaging to gain access to personal or confidential information. Attackers might trick you into installing spyware or performing harmful actions by sending a text message with a link that looks like an urgent notification from your bank or service provider.
To prevent vishing attacks, employees should learn to identify the signs of a phone phishing attack. Some of these include requests for passwords, banking information, account login details or other personal information. A good reminder is to slow down and take a deep breath when someone is pressuring you for information over the phone.
When it comes to reporting suspicious activity, if an employee is unsure about the validity of a request they should seek out more information or advice from someone who has experience in security.
In most cases, if there is any doubt, do not reveal information. Instead, seek for confirmation and guidance from your supervisor or IT department.

Working remotely doesn’t mean you are safe from Cyber Attacks. In fact, 91% of companies have reported an increase in cyber attacks in the past year due to more employees working from home. The move to remote work for many has made this one of the most important security awareness training topics.
While working from home, employees need to become more aware of the potential risks of a cyber attack. Here are some of the best ways to stay safe while working from home.
Update all apps and software you use.
While those little app updates may seem annoying they all have a purpose. With each update the companies typically include a security update. The best way to keep your software and apps safe is to update them as soon as possible.
Practice good password habits.
As you probably understand by now, password safety is a security awareness topic that also applies to basically any other topic. Same idea here. Use strong passwords.
Keep devices locked.
Even if you're at home, it’s always a good idea to keep your devices locked just in case. While it may be tempting to allow your family members to use your work device, the safest option is to keep your device locked and only used for work.
Beware of phishing attacks.
Phishing emails have skyrocketed in the past year, and with employees working remotely, it's even easier for cyber criminals to trick them. Follow the same tips from the phishing awareness training here.
This is a short but important topic as it covers some cyber security threats where people are not fully aware of the risks. Removable media such as USB drives or CDs/DVDs can be very risky, especially if they are loaded with viruses or malware.
Teach employees that if they find a USB drive or a piece of removable media, they should not plug it into any computer, and report it to their supervisor. Employees should also be reminded that the data on a removable media device is potentially hazardous and it should be treated as if it contained malware whether or not its actually infected with malware.

Social media sites, such as Facebook and Twitter, are also sources of vulnerabilities. Employees should be trained to understand the risks involved in posting private or sensitive information on social media accounts — particularly if those accounts can be accessed using a public Wi-Fi connection or through mobile devices.
While using the internet, employees can be exposed to threats and vulnerabilities — particularly if they are using Wi-Fi networks in hotels, airports, coffee shops or other public areas. Security training should ensure that employees understand the risks involved in connecting to an unfamiliar wireless network.
Sometimes accidents happen. Employees click on phishing emails or notice suspicious behavior. In all cases, it is important to know what actions employees should take if they believe there is an issue. Identifying problems early can stop cyber security breaches before they happen.
Communicate to your employees what types of incidents should be reported, who to report them to, and how they should communicate.
If you do not have a policy already in place at your company regarding reporting security incidents, now is the time to create one.
Check out guidelines from NIST for more information on creating policies and procedures around incident response (NIST SP 800-61).
Artificial Intelligence (AI)
While the use artificial intelligence (AI) has become increasingly prevalent, so have the dangers that come along with it. Educating employees on the dangers associated with AI and how to safely navigate these tools, can empower teams to handle these complex risks effectively.
Launch effective Security Awareness Training to your employees.
With Hook Security , you can easily launch, measure and automate security awareness campaigns that help you create a security aware culture.
Get a 7-day Free Trial today and see how easy it is to get started.

Sign up for our newsletter
Get Free Exclusive Training Content in your inbox every month
More from the Blog
%20(1).png)
Why Hook Security Signed the Truth in Cyber Pledge
Hook Minute: A Fun Daily Security Challenge from Hook Security!
.png)
Introducing Hook Security’s New Deepfake Awareness Training Course
Never miss a post..
- Phishing Simulator
- Psychological Security
- Done For You
- Our Approach
- Training Preview
- Partner Program
- Partner Portal
- Case Studies
- Hook Heroes
- Knowledge Base
- Phishing Test
- Phishing Examples
- Security Awareness Guide
- Security Awareness Training Topics

We create security awareness training that employees love.
Cyber security topics for presentation
Cybersecurity safeguards sensitive data, preserves trust, and defends against evolving cyber threats in our digital world.
- Rising Threat: Ransomware attacks have seen a dramatic increase in recent years, with cybercriminals targeting individuals, businesses, and even government organizations. These attacks involve encrypting the victim's data and demanding a ransom for decryption.
- Impact on Organizations: The impact of ransomware attacks can be devastating. They can result in data loss, financial losses, damage to reputation, and even legal consequences.

- Challenging Perimeter-Based Approaches: Zero Trust challenges the traditional approach of trusting entities within a network by default. Instead, it promotes the concept that trust is never assumed, and strict access controls and continuous verification are essential.
- Continuous Verification: Zero Trust requires ongoing authentication and authorization, even for users and devices within the corporate network, reducing the risk of insider threats.

- Tactics Used by Cybercriminals: Social engineering attacks, such as phishing, rely on manipulation and deception to trick individuals into divulging sensitive information or taking harmful actions. Attackers often impersonate trusted entities or create urgency to deceive victims.
- Recognizing and Counteracting: Educating individuals and employees about the common signs of phishing attacks and social engineering tactics is essential. Implementing email filtering, multi-factor authentication (MFA), and security awareness training can greatly reduce the risk of falling victim to these attacks.

Create PPT using AI
Just Enter Topic, Youtube URL, PDF, or Text to get a beautiful PPT in seconds. Use the bulb for AI suggestions.
character count: 0 / 6000 (we can fetch data from google)
upload pdf, docx, .png
less than 2 min
Sanskar Tiwari
Founder at MagicSlides
How to add correct answers to Google Forms
22 February 2024
How to convert a PDF to Google Slides
15 February 2024
How to see who responded on google forms
13 February 2024
How to get notifications from google forms
How to do voice overs on google slides
How to see Google Forms you filled out
9 February 2024
How to add a link to a picture in Google Slides
How to change theme color in Google Slides
7 February 2024
How to insert PDF into Google Slides
6 February 2024
Stunning presentations in seconds with AI
Install MagicSlides app now and start creating beautiful presentations. It's free!
Get AI-Generated Presentations Ready in Seconds
Free AI PPT Tools

10 must-include security awareness training topics for your 2023 awareness program

12 April 2023
Ah, don’t you love living in the world of cyber threats? Where traditional security measures won’t be enough to keep your organization safe. Lovely here, isn’t it?
Why didn’t we all go with our five-year-old self’s career aspirations and go into donut testing?
For what it’s worth, we think you’re nothing short of a hero. With cyber threats evolving and increasing in frequency every day, the threat to organizations is, well, prett-ay daunting. And you’re reading this because you care.
It’s people like you who make us want to get up in the morning.
Anyway, back to the topic in hand. You know it’s important to equip your people with the knowledge and skills they need to stay secure. In fact, it’s more important than it’s ever been.
And you want to make sure your training program actually reflects what’s going on out there, right?
And you’ve got questions. Things like:
What should cybersecurity awareness training courses in 2023 cover?
Why is staying up to date with the latest threats important in cybersecurity?
Why should everyone understand how social engineering works?
Well, good news. We’re about to take a look at the 10 key cybersecurity topics that you can’t afford to miss from your cybersecurity awareness training courses in 2023.
This short read is the perfect starting point—the warm-up, if you will. And our 2023 security awareness predictions report is the ultimate headliner.
You’ll scream, you’ll cry, you’ll hold your lighter aloft.*
*Results may vary.
Ready? Here they come.
1. Threat intelligence
Staying on top of the latest threats is critical to keep your organization safe. 70% of cybersecurity professionals surveyed for our predictions report said they plan to invest more in threat intelligence in the coming years.
Threat intelligence is a powerful tool that helps organizations to anticipate, detect, and respond to cyber threats. Cybercriminals are always coming up with new ways to breach organizations, so it’s essential that people are trained to identify potential threats and take appropriate action.
Threat intelligence training should cover the latest trends in cybercrime, including new attack methods, malware, and ransomware . The training should also give people the tools and techniques to spot cyber threats.
With the right threat intelligence training, you’ll position people where they should be — as an integral part of an organization’s security infrastructure.

2. Social engineering
Cybercriminals love social engineering almost as much as they love making your life a misery.
It’s a favorite tactic because of how well it works. When they need to trick people into revealing sensitive information or causing major headaches for organizations, it’s the go-to technique.
And one thing you need to take into account is how these tactics are becoming increasingly sophisticated—and difficult to detect.
So, give your people the best chance. Show them how to recognize and resist social engineering attacks . They should know how to spot suspicious messages, emails, or calls.
This training should also cover the different types of social engineering attacks, like phishing, pretexting, baiting, and tailgating.
And remember, people need to know how to report a social engineering attack and who to contact if they suspect they’ve been targeted.
3. Password management
Passwords are the first line of defense against unauthorized access to sensitive data. And that means password management is an essential part of any worthwhile cybersecurity program.
Do your people know how to create strong passwords? Do they understand the importance of not sharing passwords? Do they know how to manage passwords securely?
Password management training should cover the use of password managers, multi-factor authentication, and best practices for creating strong passwords.
And, vitally, the training should emphasize the importance of changing passwords regularly —and why we don’t reuse old passwords across different accounts.

4. Phishing awareness
So, yes, phishing attacks are very common. And because of your job role, maybe you never stop thinking about them. In fact, maybe you even dream about them.
But how sure are you that others in your organization would spot a cybercriminal trawling for sensitive information?
It’s essential to train people on how to spot phishing emails and what to do if they receive one. Training should cover different types of phishing, like spear-phishing and whaling, and how to report a phishing email.
And they’ll need to know how to verify the authenticity of an email before clicking on any links or downloading any attachments.
5. Malware protection
Malware is a royal pain . It’s designed that way. And people need to know about it to stop it damaging or disrupting computer systems.
Training on viruses, worms, Trojan horses, and spyware will help equip people to recognize and avoid it, how to report it if they encounter it, and how to protect against it.
People need to appreciate that updates and security patches help prevent malware from taking hold. And vitally, the reasons we don’t just download any old file from any old place on the internet.
6. Mobile device security
Mobile devices are becoming increasingly popular targets for cyber criminals.
So, people need to know how to secure them properly.
They’ll need to know best practices for using mobile devices securely. That includes how to protect sensitive information stored on them, how to use strong passwords, and how to avoid risky behaviors like using public Wi-Fi networks .
It’s also important to have a plan in place for lost or stolen devices. Would someone know what to do if their device is lost or stolen? Could they remotely wipe data if they needed to? Would they know how to report the loss?

7. Cloud security
Cloud computing is ever more our go-to for storing and accessing data. But do your people know how to use it safely?
They need to understand the risks that come with cloud computing and how to handle them like pros.
So your training program will need to cover how to use cloud services securely. That’ll include how to protect login credentials, how to avoid sharing sensitive data in public cloud environments, and how to use encryption to protect data in transit and at rest.
8. Data protection
The goal behind so much security behavior is of course safeguarding the data we hold.
People should be trained thoroughly on this critical topic. To keep your organization safe they need to feel confident in how to handle sensitive data, including how to securely transfer it and how to store it safely.
Oh — and they should learn about best practices for using strong passwords, encrypting sensitive data, and backing up data to prevent data loss in case of a cyber attack.
9. Incident response
Much training covers how to avoid successful attacks … and it stops there.
Do people outside of your team know how to respond to a cybersecurity incident? This is a vital topic. You need to cover how to recognize and report security incidents, including who to contact and what information to provide.
People should also be trained on how to limit damage and restore normal operations as quickly as possible.
Sure, having a well-documented incident response plan in place can help to reduce the impact of an incident. But people should be trained on how to follow that plan, in case of a breach or attack.

10. Continuous learning
Cyber threats are constantly evolving.
Just like a TikTok feed, it’s never ending.
So, it’s important that people stay up-to-date with the latest news and best practices.
Cybersecurity awareness training should be just as constant. But instead of recycling the same old same old, it should throw out regular updates and refresher courses to keep everyone engaged and informed.
A culture of continuous learning and improvement sounds ever so grand, doesn’t it? But it’s exactly what you need to create a more security-conscious organization.
A strong cybersecurity culture is guaranteed to bring down the risk of cyber attacks and breaches.
We promise that by empowering people with the knowledge and skills they need to stay safe online, you can create a stronger security posture and better protect themselves against cyber threats.
Before we end the lesson. . .
So, where are we at?
Cybersecurity threats are constantly evolving (and increasing in frequency). And traditional security measures are no longer sufficient to protect organizations from those threats.
Still, there’s no getting away from it: Education is a crucial part of maintaining a secure organization.
Your 2023 cybersecurity training needs to cover these topics. Otherwise, instead of training, you might as well just put Frozen on, and have an office singalong. At least you can go down singing.
But instead, we’re going to suggest you serve up an all-bases cybersecurity training program.
You’ll ensure that your people are not only knowledgeable but confident too in protecting themselves and the organization against cyber threats.
Ready to take your cybersecurity awareness training to the next level in 2023? You’ll want to take a look at the valuable insights in our 2023 security awareness predictions report !

Cybersecurity topics FAQs
Individuals and organizations should be aware of common cybersecurity threats like malware, phishing attacks, data breaches, ransomware , and social engineering schemes. Staying informed about these threats is crucial for cybersecurity awareness.
To enhance cybersecurity awareness, utilize a human risk management platform that includes regular cybersecurity training sessions for employees, shares real-world examples of cyber threats, and fosters a culture of security awareness where everyone plays a role in protecting data.
Employee training is vital for cybersecurity awareness as it educates staff about potential threats, how to recognize them, and the best practices for safe online behavior. Informed employees are a crucial line of defense against cyberattacks.
Cybersecurity Awareness Month offers an excellent opportunity to delve into various essential topics. For more details and resources on these topics, you can read 47 creative ideas blog .

Do one more thing right today. Subscribe to the Behave newsletter
You may also like

7 cybersecurity lessons from the 1950s
Aug 8, 2024
Expert's 7 1950s-inspired principles for cyber resilience Moving beyond train-the-user and buy-this-tech Today’s...

Interlinking GenAI and Human Cyber Risk
Jul 31, 2024
Generative artificial intelligence Generative artificial intelligence, or GenAI, is the term used to describe data-led...

Experts speak out: Four reasons your cyber risk strategy needs a reboot
Jul 24, 2024
Blind spots and biases: Experts get real at IMPACT 2024 USA Even seasoned practitioners mess up sometimes. We all do....

An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
https://www.nist.gov/itl/smallbusinesscyber/nist-cybersecurity-fundamentals-presentation
Small Business Cybersecurity Corner
Nist cybersecurity fundamentals presentation.
Download the Slides
Managing a small business is always challenging but keeping up with cybersecurity threats can be overwhelming. How do you learn about the latest threats? How do you educate your staff about best practices? NIST has prepared a training presentation (draft) that you can use to self-teach and help your team learn at the same time. Please download the slides so you can use them at your convenience.
Each slide includes speaker’s notes – so you will be able to understand and share the material and find links to resources to learn more. You can go through the materials as quickly or slowly as you need, knowing that the recommendations come from the Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST).
The material is in sections: Cybersecurity Basics; Cybersecurity Threats; Risk Management; Cybersecurity Framework; and Small Business Cybersecurity Resources. You and your team will become familiar with common threats like phishing and ransomware, understand steps you can take every day to prevent falling victim and steps to take to recover should trouble strike.
We welcome your feedback on this draft presentation and will incorporate improvements in the future.
Newly Launched - AI Presentation Maker

- Cyber Security
AI PPT Maker
Powerpoint Templates
Icon Bundle
Kpi Dashboard
Professional
Business Plans
Swot Analysis
Gantt Chart
Business Proposal
Marketing Plan
Project Management
Business Case
Business Model
Business PPT
Digital Marketing
- Digital Transformation
Human Resources
Product Management
- Artificial Intelligence
Company Profile
Acknowledgement PPT
PPT Presentation
Reports Brochures
One Page Pitch
Interview PPT
All Categories

Download Cyber Security PPT Presentation, Template & Slides
- Sub Categories
- 5G Technology
- Agile and Scrum
- Big Data Analytics
- Cloud Computing
- Cryptocurrency
- Data Analytics
- Green Energy
- Internet Of Things
- IT Certification
- Machine Learning
- Microprocessors
- Nanotechnology
- Robotic Process Automation
- Software Testing
- Technology Project Management
- Technology Quality Assurance
- Technology Stack
- Virtualization

EduDecks are professionally-created comprehensive decks that provide complete coverage of the subject under discussion. These are also innovatively-designed for a powerful learning experience and maximum retention

Ready to use PowerPoint sample assist you in saving both your time and effort. Luxury to add or remove content in the design. Transmute the PPT layout with industry information i.e. banner and icon. Flexible as can be adapted in JPEG or PDF documents. Text and font can be easily reformed as the presentation need. Presentation template design shown in both standard and widescreen slide

Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Cyber Security It Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the eighty one slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.

Presenting this set of slides with name - Data Governance Powerpoint Presentation Slides. This PPT deck displays twenty-five slides with in-depth research. We provide a ready to use deck with all sorts of relevant topics subtopics templates, charts and graphs, overviews, analysis templates. This template is compatible with Google Slides, which makes it accessible at once. Can be converted into various formats like PDF, JPG, and PNG. The slide is easily available in both 4:3 and 16:9 aspect ratio.
Enthrall your audience with this Enterprise Cyber Security Awareness Employees Training Complete Deck. Increase your presentation threshold by deploying this well crafted template. It acts as a great communication tool due to its well researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention grabber. Comprising fifty four slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.

Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Privacy IT Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the sixty five slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.

Presenting our Cyber Security for Organization Proposal PowerPoint Presentation Slides. This is a completely adaptable PPT slide that allows you to add images, charts, icons, tables, and animation effects according to your requirements. Create and edit your text in this 100% customizable slide. It is also available in widescreen. You can change the orientation of any element in your presentation according to your liking. The slide is available in both 4:3 and 16:9 aspect ratio. These PPT slides are also compatible with Google slides.

This complete deck can be used to present to your team. It has PPT slides on various topics highlighting all the core areas of your business needs. This complete deck focuses on How To Present Cyber Security To Senior Management Complete Deck and has professionally designed templates with suitable visuals and appropriate content. This deck consists of total of fifty five slides. All the slides are completely customizable for your convenience. You can change the colour, text and font size of these templates. You can add or delete the content if needed. Get access to this professionally designed complete presentation by clicking the download button below.

Enthrall your audience with this Cloud Security IT Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well crafted template. It acts as a great communication tool due to its well researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention grabber. Comprising eighty nine slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.

SlideTeam introduces Cybersecurity Incident Management Powerpoint Presentation Slides. Build a visually-stunning presentation by downloading this deck of 55 professionally-designed PPT slides. Each PowerPoint template features 100% customizability. Personalize text, font, orientation, colors, patterns, background, and shapes as desired. Convert the file format from PPT to PDF, PNG, or JPG as and when necessary. This presentation works well with widescreen and standard resolutions. Use Google Slides for easy access.
Presenting this set of slides with name Global Cyber Security Or Critical Risk Dashboard. The topics discussed in these slides are Global, Cybersecurity, Overall Progression, Critical Risks Identified, Highlights. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Presenting our cyber security and phishing awareness training PowerPoint presentation slides. This PowerPoint design contains fifty slides in it which can be completely customized and edited. It is available for both standard as well as for widescreen formats. This PowerPoint template is compatible with all the presentation software like Microsoft Office, Google Slides, etc. It can be downloaded in varying formats like JPEG, PDF, PNG, etc. You can download this PPT layout by clicking on the button below.

Presenting our well-structured Analysis Of NIST Cyber Security Framework. The topics discussed in this slide are Identify, Protect, Detect, Respond, Recover. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.

SlideTeam brings Implementing Cybersecurity Management Framework Powerpoint Presentation Slides. There are 55 visually-gripping PowerPoint templates in this 100% editable deck. Customize font, text, patterns, shapes, colors, orientation, and background as required. Convert the PPT file format into PDF, PNG, and JPG according to your convenience. Use Google slides to view this presentation. It also works well with standard and widescreen resolutions.

Presenting IT security PowerPoint presentation slide. It covers total of 19 professionally designed PPT slides. Our PowerPoint experts have included all the necessary layouts, diagrams and templates to meet the needs of the customers. This content ready deck is completely customizable. Edit the color, text and icon as per your requirement. You can also add or delete the content from the presentation as per your need. You can easily download this presentation. They are high resolution PPT templates and are perfectly compatible with Google Slides.
Introducing our Key Components Of Cyber Security Framework set of slides. The topics discussed in these slides are Cyber Risk Reporting, Organizational Drivers, Enterprise Risk Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.

Presenting our cybersecurity awareness training PowerPoint presentation slides. This PowerPoint design contains fifty-one slides in it which can be completely customized and edited. It is available for both standard as well as for widescreen formats. This PowerPoint template is compatible with all the presentation software like Microsoft Office, Google Slides, etc. It can be downloaded in varying formats like JPEG, PDF, PNG, etc. You can download this PPT layout by clicking on the button below.

Enthrall your audience with this Cloud Security Model Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising eighty slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.

Ditch the Dull templates and opt for our engaging Identity And Access Management Proposal Powerpoint Presentation Slides deck to attract your audience. Our visually striking design effortlessly combines creativity with functionality, ensuring your content shines through. Compatible with Microsoft versions and Google Slides, it offers seamless integration of presentation. Save time and effort with our pre-designed PPT layout, while still having the freedom to customize fonts, colors, and everything you ask for. With the ability to download in various formats like JPG, JPEG, and PNG, sharing your slides has never been easier. From boardroom meetings to client pitches, this deck can be the secret weapon to leaving a lasting impression.

Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Case Competition Overcome The Challenge Of Cyber Security In Healthcare Complete Deck is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the fourty nine slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.

Presenting computer security PowerPoint presentation slides. This deck comprises of 17 slides. Each slide is well crafted and designed by our PowerPoint experts. This PPT presentation is thoroughly researched by the experts and every slide consists of an appropriate content. All slides are customizable. You can add or delete the content as per your need. Not just this, you can also make the required changes in the charts and graphs. Download this professionally designed computer security presentation to save yourself from cybercrime.

If you require a professional template with great design, then this Security Controls Management Cyberattacks Organization Infrastructure Investments is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twelve slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.

This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of fifty six slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the color, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.

Deliver an informational PPT on various topics by using this Phishing Attacks And Strategies To Mitigate Them Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with one hundred one slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.

Deliver an informational PPT on various topics by using this Ethical Hacking IT Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with eighty seven slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.
Keep your audience glued to their seats with professionally designed PPT slides. This deck comprises of total of twelve slides. It has PPT templates with creative visuals and well researched content. Not just this, our PowerPoint professionals have crafted this deck with appropriate diagrams, layouts, icons, graphs, charts and more. This content ready presentation deck is fully editable. Just click the DOWNLOAD button below. Change the colour, text and font size. You can also modify the content as per your need. Get access to this well crafted complete deck presentation and leave your audience stunned.
Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this SASE IT Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the eighty slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.

Presenting How To Handle Cybersecurity Risk Powerpoint Presentation Slides. This complete PPT deck is composed of 55 visually-stunning templates. Build a presentation faster using our 100% customizable PowerPoint slideshow. Edit text, font, colors, orientation, shapes, background, and patterns however you choose. Change the file format into PDF, PNG, or JPG as and when convenient. This presentation works well with standard and widescreen resolutions. Use Google Slides for a quick view.

Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Firewall Implementation For Cyber Security Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the seventy one slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.

If you require a professional template with great design, then this Cyber Threat Powerpoint PPT Template Bundles is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twenty three slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.

Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts,this Information Technology Security Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the eighty one slides are editable and modifiable,so feel free to adjust them to your business setting. The font,color,and other components also come in an editable format making this PPT design the best choice for your next presentation. So,download now.

This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of seventy eighjt slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the color, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.

Engage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Cybersecurity Organizational Network Protection Measures is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With twelve slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.

Enthrall your audience with this SASE Security Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising eighty slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.

Introducing cyber threat and security management PowerPoint slide. Well researched PPT template design with completely reform able styles, images, tables, graphs, context, sizes etc. Relevant for IT business professionals such as managers, executives, and researchers etc. Genuine and admissible PPT Image with pliant options to add the company name, brand, or emblem. Adequately compatible with all operating software and all Google Slides.
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver an outstanding presentation on the topic using this Corporate Data Security Awareness Organization Cyber Security Dashboard Ppt Powerpoint Guidelines. Dispense information and present a thorough explanation of Executives, License Consumption, Operating Systems using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.

Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Data Security IT Powerpoint Powerpoint Presentation is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the eighty slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.

This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of seventy nine slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the color, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.
Presenting this set of slides with name Advantages Of Cyber Security. This is a six stage process. The stages in this process are Valuable Information Protection, Risk Mitigation, Recovery Time Is Improved, Evade Loss Of Crucial Data, Privacy Of Customer And Employee Is Ensured. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Enthrall your audience with this Quantum Computing IT Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well crafted template. It acts as a great communication tool due to its well researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention grabber. Comprising eighty four slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
Presenting this set of slides with name Various Kinds Of Attacks In Cyber Security. This is a seven stage process. The stages in this process are Web Based Attack, Phishing, Botnets, Malicious Codes, Spam, Malware. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Enterprise Security Operations Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the fifty five slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.

Enthrall your audience with this Enterprise Governance Of Information Technology EGIT Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising seventy eight slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
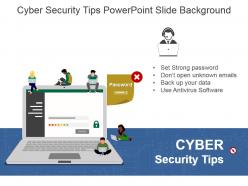
Presenting cyber security tips powerpoint slide background. This is a cyber security tips powerpoint slide background. This is a one stage process. The stages in this process are set strong password, don?t open unknown emails, back up your data, use antivirus software, cyber security tips.
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Present the topic in a bit more detail with this Cyber Security IT Dashboard For Threat Tracking In Cyber Security Ppt Powerpoint Tutorials. Use it as a tool for discussion and navigation on Monthly Threat Status, Threats By Owners, Risk By Threats, Current Risk Status, Threats Based On Role, Threat Report. This template is free to edit as deemed fit for your organization. Therefore download it now.

Deliver a credible and compelling presentation by deploying this Information Security Governance Information Planning Stakeholders Framework. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The twelve slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Information Security Governance Information Planning Stakeholders Framework PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver an outstanding presentation on the topic using this Organization Cyber Security Dashboard Cyber Security Phishing Awareness Training Ppt Pictures. Dispense information and present a thorough explanation of Organization Cyber Security Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.

Presenting our readily available Organization Cyber Protection Proposal PowerPoint Presentation Slides for your bidding needs. This is a completely adaptable PPT theme that lets you add images, charts, icons, and tables according to your need. The template is available in both 4:3 and 16:9 aspect ratios. It can be downloaded in PDF, JPG, and PNG formats. So download and captivate your audience.

This complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Data Privacy Compliance Awareness Planning Strategy Assessment Methodology Framework and has templates with professional background images and relevant content. This deck consists of total of twelve slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the colour, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.

This complete deck can be used to present to your team. It has PPT slides on various topics highlighting all the core areas of your business needs. This complete deck focuses on Data Security Powerpoint Presentation Slides and has professionally designed templates with suitable visuals and appropriate content. This deck consists of total of twenty two slides. All the slides are completely customizable for your convenience. You can change the colour, text and font size of these templates. You can add or delete the content if needed. Get access to this professionally designed complete presentation by clicking the download button below.

This complete deck can be used to present to your team. It has PPT slides on various topics highlighting all the core areas of your business needs. This complete deck focuses on Technology Security Process Framework Assessment Management Awareness and has professionally designed templates with suitable visuals and appropriate content. This deck consists of total of twelve slides. All the slides are completely customizable for your convenience. You can change the colour, text and font size of these templates. You can add or delete the content if needed. Get access to this professionally designed complete presentation by clicking the download button below.

Presenting this set of slides with name Key Statistics Of Cyber Security In Small Businesses. The topics discussed in these slides are Business, Manufacturers, Cost Of Data, Ransomware, Identity Theft. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
This slide Covers the Graphical Representation Analysis of Cyber Security. Data covered in this dashboard snapshot includes Threats, Threats per month, Average threat per day with top 10 threat by sub class and class name. This is a Cyber Security Dashboard Snapshot For Security Operations Powerpoint Template drafted with a diverse set of graphics, that can be reformulated and edited as per your needs and requirements. Just download it in your system and make use of it in PowerPoint or Google Slides, depending upon your presentation preferences.

Introducing a Visual PPT on Many Types Frauds. Every slide in this PowerPoint is meticulously designed by our Presentation Experts. Modify the content as you see fit. Moreover, the PowerPoint Template is suitable for screens and monitors of all dimensions, and even works seamlessly with Google Slides. Download the PPT, make necessary changes, and present with confidence.
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Present the topic in a bit more detail with this Organization Cyber Security Dashboard Implementing Security Awareness Program Ppt Clipart. Use it as a tool for discussion and navigation on Organization Cyber Security Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.

Engage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Information Security Risk Management Powerpoint Ppt Template Bundles is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With sixteen slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver an outstanding presentation on the topic using this Cybersecurity Awareness Training Organization Cyber Security Dashboard Ppt Model Graphics. Dispense information and present a thorough explanation of Executives, License Consumption, Operating Systems using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.

Engage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Cybersecurity Risk Measures Services Compliance Probability Customers Financial is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With twelve slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.

Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this IT Security Operations Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the fifty nine slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.

Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Managing Cyber Risk In A Digital Age Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the fifty six slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
Item 1 to 60 of 559 total items
- You're currently reading page 1

Ratings and Reviews
by Dan Marshall
June 9, 2021
by Donovan Cunningham
June 10, 2021
by Craig Moreno
March 9, 2022
by Del Holmes
by Courtney Griffin
by Edgar George
June 23, 2021
by Chong Richardson
June 22, 2021
by Coleman Henderson
by James Lee
January 2, 2023
Items 1 to 10 of 254 total

- Data Science

Top Cybersecurity Presentations

Today, organizations are affected by cyberattacks like malware, phishing, man-in-the-middle attack, SQL injection attacks, and more. Due to such attacks, organizations’ systems, programs, and networks are damaged. Therefore, to avoid cyberattacks, organizations follow specific cybersecurity methods. If you are looking for an overview of cybersecurity and its practices, this article will help you with some of the best cybersecurity presentations.
Top Presentations on Cybersecurity
Listed below are some essential and primarily used cybersecurity presentations.
- Artificial Intelligence and Cybersecurity
Olivier Busolini published Artificial Intelligence and Cybersecurity presentation in March 2019, he is a cybersecurity professional working with AI in cybersecurity. This presentation provides a basic introduction to AI, an overview of AI technologies, machine learning technologies, basics of deep learning, difficulties faced during building AI solutions, and tips for cybersecurity strategy.
This presentation also includes an introduction to red and blue AI technologies and a list of organizations that are using AI to follow cybersecurity practices to secure their information. Therefore, with AI and Cybersecurity presentations, learners can get a brief idea of cybersecurity solutions.
Link to the PPT: Artificial Intelligence and Cybersecurity
2. AI and the impact on Cybersecurity
Published in October 2019, the AI and impact on Cybersecurity presentation by Graham Mann cover the explanation of what AI is and its impact on cybersecurity. The presentation includes content like the importance of AI, cloud computing, machine learning algorithms, and blockchain. It also consists of statistics on cyberattacks in 2018, cyber targets in 2019, and AI-assisted cyberattacks.
With the AI and its impact on Cybersecurity presentation, you will know the potential of AI technology and its impact on cyberattacks and cybersecurity practices. This presentation also briefs you about AI and the laws associated with it.
Link to the PPT: AI and the impact on Cybersecurity
3. How can AI help in Cybersecurity
This presentation was published by Priyanshu Ratnakar, who is the Founder, Director, and CEO of Protocol X, in March 2021. It provides a brief idea of AI in cybersecurity and is suitable for every person who wants to learn how AI can help in cybersecurity. The presentation consists of topics like the basics of AI, machine learning and deep learning, AI in real-life, the effects of AI in cybersecurity, and how hackers use AI technology to attack computer systems.
Link to the PPT: How AI can help in Cybersecurity
4. IT fundamentals of Cybersecurity
Tanishk Jharwal, a Student at Swami Keshvanand Institute of Technology Management and Gramothan (SKIT) published the IT fundamentals of Cybersecurity presentation. This presentation highlights cybersecurity in four parts:
- Introduction to cybersecurity tools and cyberattacks
- Cybersecurity roles, processes, and operating system security
- Network security and database
- Cybersecurity compliance, framework, and system administration
The presentation also includes contents such as categories of cybercrime, a list of security tools, safety tips for cybercrime, and the advantages of cybersecurity. It explains cyber crimes like hacking, phishing, spam emails, denial of service, spyware, adware, malware, and ransomware.
Link to the PPT: IT fundamentals on Cybersecurity
5. Cybersecurity 101
Wiam Younes, Carnegie Mellon University, published the cybersecurity 101 presentation. The PPT includes an introduction to cybersecurity, security threats and risks in computer systems, security measures in cybersecurity, safely managing your passwords, managing your email accounts, and securing your computer systems.
The Cybersecurity 101 presentation teaches you to protect the data you are handling and provides guidelines for protecting yourself from cyber attacks. It offers different policies and procedures for protecting your network and system.
With this cybersecurity ppt, you can identify cybercrime-related theft, including credit card fraud, financial identity theft, government identity theft, mortgage fraud, and license plate number identity theft. This ppt also guides you through different practices to protect yourself from identity theft.
Link to the PPT: Cybersecurity 101
6. Cybersecurity Introduction
The Cybersecurity Introduction is a presentation from the students of Mohawk College in Hamilton, Canada. This presentation provides you with the basics of cybersecurity, its definitions, principles, and about cyber threats. It also guides you through different sources of cyber threats, classifications of cyber threats, unstructured cyber threats, structured cyber threats, and highly structured cyber threats.
With this presentation, you can also learn about cyber attacks, their types, and the impacts of cyber threats. This presentation will also give you a brief idea about malicious code and its types. The Cybersecurity Introduction PPT highlights the vulnerabilities of your computer system in cybercrime.
Link to the PPT: Cybersecurity Introduction
7. Study of Emerging Trends and Challenges of Cybersecurity
Published in January 2022, the Study of Emerging Trends and Challenges of Cybersecurity presentation by Ritvik Kumar provides an overview of emerging trends and challenges in cybersecurity. The presentation consists of content such as the basics of cybersecurity and cybercrime, trends in changing cybersecurity, cybersecurity techniques, cyber ethics, and the roles of social media in cybersecurity.
This presentation also highlights the cybersecurity incidents reported to Cyber999 in Malaysia between January 2012 and 2013. Cyber999 is a cybersecurity center operated by Malaysia Computer Emergency Response Team (MyCERT) to report incidents related to cyberbullying or cyberattacks.
Link to the PPT: Study of Emerging Trends and Challenges of Cybersecurity
8. Cyberattacks and IT Security in 2025
The Cyberattacks and IT Security in 2025 presentation is drafted by RadarServices, the European market leader for managed security services. RadarServices interviewed designated IT security experts in Europe and Asia and shared their views in this presentation concerning the development of cyberattacks and security technologies till 2025.
The presentation provides an overview of the questions like the type of cyberattacks that will be estimated in 2025, what are the biggest challenges for IT security technologies today and which will be there in 2025, and in which areas of IT security organizations need to invest to be viable in 2025.
The presentation highlights the dangers of cyberattacks that will likely happen in 2025. It also briefs you on security technologies companies need to use to prevent cyberattacks’ dangers.
Link to the PPT: Cyberattacks and It Security in 2025
9. Cybersecurity in Society
The Cybersecurity in Society presentation by Rubal Agarwal was published in August 2018. This presentation provides an overview of cybercrime, its types, and its stages. It also provides you with the importance of cybersecurity and safety tips for cybercrime.
He also presented cyber crimes such as hacking, child pornography, phishing, denial of service attacks, cyber terrorism, virus spreading, and software piracy. It highlighted the statistics of the number of cybercrime cases in India in January 2015. The presentation also consists of the effects of cybercrime in India. The PPT also includes the top 10 security assessment tools to identify vulnerabilities in cyber security.
Link to the PPT: Cybersecurity in Society
10. Cybersecurity
The Cybersecurity presentation was published in October 2021 by Vinod Sencha. The presentation contains the importance of cybersecurity, cybersecurity domains, the CIA (Confidentiality, Integrity, and Availability) Triad, and threats and vulnerabilities in cybersecurity. It also highlights the concepts like phishing and its statics and examples, malware, viruses, bombs, Trojans, Worms, email worms, denial of service attacks, and ransomware.
Vinod Sencha focuses on the Covid-19 cyber threats in the presentation. He also briefs you about society’s types of cybercriminals, virus detection, cybersecurity and privacy, and footprinting.
Link to the PPT: Cybersecurity
Subscribe to our newsletter
Subscribe and never miss out on such trending AI-related articles.
Join our WhatsApp Channel and Discord Server to be a part of an engaging community.

RELATED ARTICLES
What is enterprise data management, what is a data structure , building high-quality datasets with llms, leave a reply cancel reply.
Save my name, email, and website in this browser for the next time I comment.
Most Popular

Analytics Drift strives to keep you updated with the latest technologies such as Artificial Intelligence, Data Science, Machine Learning, and Deep Learning. We are on a mission to build the largest data science community in the world by serving you with engaging content on our platform.
Contact us: [email protected]
Copyright © 2024 Analytics Drift Private Limited.

Schedule a demo
Schedule a cab demo, download the the state of security awareness training, download the phishing simulation playbook.

14 Cybersecurity Awareness Topics You Need to Cover
You might be surprised to discover that merely running cybersecurity awareness training programs for your staff is insufficient to foster a robust culture of awareness in your organization. Paying attention to the details of how the training works and the precise topics covered is what sets apart the most security-aware businesses.
With the cyber threat landscape evolving swiftly, training programs that stay the same over time become outdated quickly. Who had even heard of a double supply chain attack before 2023? The math is simple: a recent survey reported that over 80% of leaders say their company has a security awareness and training program, but over 50% believe their employees lack cyber awareness. Clearly, there are issues and shortfalls in the subjects covered by these programs.
Here are fourteen pertinent cybersecurity awareness topics your training program must cover to be effective.
Why Cybersecurity Awareness Training is Critical Today
In addition to the growing number and sophistication of cyber threats, many attacks target users directly, and many cyber mishaps stem from a lack of security awareness. The right cybersecurity awareness training is vital because a comprehensive, up-to-date program helps change employees from being a weak link to a human firewall that can identify and avoid many cyber attacks and breaches.
Most corporate leaders believe greater employee cybersecurity awareness would help reduce cyber attacks. Security awareness training offers an organization invaluable benefits, including:
- Educating your employees about an evolving threat landscape
- Helping them recognize the value of the data they handle and applying the best practices to protect it
- Mitigating financial losses
- Ensuring your employees understand their roles and responsibilities in compliance with regulations such as GDPR, HIPAA, and the Digital Operational Resilience Act (DORA)
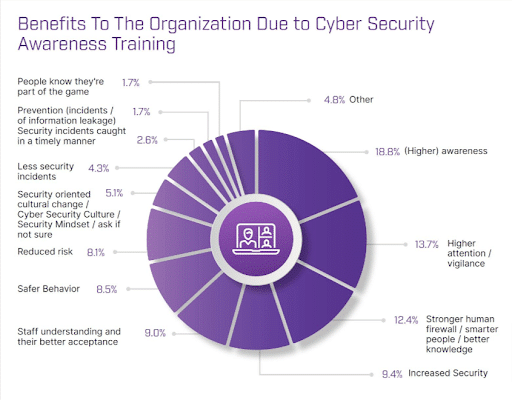
14 Cybersecurity Awareness Topics to Cover in Training
When choosing a training program, be sure that the following cybersecurity awareness topics are covered:
1. Phishing Awareness
Your employees need to know how to identify phishing attempts so they don’t get tricked by email scams that involve outsiders masquerading as trustworthy people or companies.
Points to teach in training modules include:
- Examine sender email addresses closely to check for any misspellings or slight deviations from the usual address.
- Scrutinizing URLs within emails before clicking on them.
- Look for phishing language signs, such as urgency, generic greetings, or poor spelling/grammar.
This topic should also cover fraudulent text messages ( smishing ) or phone calls (vishing) as other delivery methods for these scams. Include information about common phishing tactics, like fake job offers or mimicking legitimate organizations that recipients trust.
Pay attention to the growing problem of targeted spear phishing attacks focusing on specific individuals or roles within your company, such as impersonating a high-level executive or targeting finance teams.
The best way to train phishing awareness is through phishing simulations. CybeReady’s platform uses data-driven campaigns and adaptive training to help deliver phishing simulations that markedly improve the ability to identify and avoid phishing scams.
2. Password and Authentication Security
Convey to learners how solid and unique passwords combined with multi-factor authentication (MFA) significantly reduce the risk of unauthorized access to their accounts.
Even with billions of stolen credentials circulating on the dark web, hackers will struggle to get into an account protected by MFA because they’ll need to provide a second, distinct category of evidence beyond a password that proves their identity, such as biometrics or a one-time code sent to your employee’s phones.

Also, cover best practices for Single Sign-on (SSO) security to avoid account takeover (ATO) attacks targeting employees and customers.
3. Social Engineering Defense
Threat actors don’t limit themselves to traditional phishing scams when trying to dupe or manipulate people into revealing sensitive info, downloading malicious attachments, or clicking suspicious links. Practical training should run through the whole gamut of social engineering techniques that hackers could use, including pretexting, baiting, and tailgating.
Beyond understanding the many types of social engineering, teach employees how to verify identities and requests, especially in cases where those requests involve access to sensitive data or financial transactions.
4. Safe Internet Practices
Many cyber breaches stem from unsafe Internet practices. Ensure cybersecurity awareness training addresses best practices like trusting websites with secure HTTPS connections, not downloading files or software from untrusted sources, and being mindful of what information employees share on social media or networking platforms like LinkedIn.
Remind employees that many public Wi-Fi connections lack any security features, so encrypting the connection with a VPN is imperative if they must connect to those networks.
5. Email Security
Good email security awareness includes being cautious of attachments and links from unknown sources, using spam filters, and reporting suspicious emails. Also, teach employees about the risk of sharing sensitive information by email and the need for an encrypted connection.
6. Mobile Device Security
With the boundaries between personal and work life blurring, employees must understand how to securely use personal and company-provided mobile devices when accessing work-related information. This includes using the device’s basic security features, like setting a screen lock and promptly applying operating system security updates when notified.
Employees also need to Understand the risk of installing apps from unverified sources outside the usual app stores on these devices.
7. Data Protection and Privacy
Employees play a frontline role in safeguarding your company’s sensitive information. Awareness training should convey the importance of this function and help employees understand how to ensure data confidentiality, integrity, and availability.
Distinguish between different types of data to protect, such as Personal Identifiable Information (PII), Protected Health Information (PHI), and Intellectual Property (IP). Also, outline the legal consequences of data breaches. Round this training with secure practices like data minimization, encryption, and access control .
8. Malware and Ransomware
Awareness of malware and ransomware means knowing how malicious software can infect systems. The two most common ways are email attachments, and malicious or spoofed websites . Include other relevant topics like the danger of enabling Macros in Microsoft Excel or running executable files from unknown sources. Employees must also know what to do if they inadvertently install malware on their system.
9. Remote Working Security
With hybrid work now a mainstay option in many job roles, remote work security is more important than ever. A comprehensive approach includes tips on bolstering home Internet security by changing default router settings and updating firmware when available. Beyond the home Internet network, employees should know how to secure devices from theft or unauthorized access. Strong familiarity with your company’s remote work policy is also paramount.
10. Cloud Security
The average business now uses 371 SaaS apps, and the cloud revolution extends to cloud infrastructure and data storage. Employees who use any cloud service need to know about specific cloud security practices, such as:
- Only using vetted and approved apps.
- Sharing data securely.
- Using configuration management tools to avoid misconfigurations.
- Encrypting data before uploading it to cloud services.

11. Artificial Intelligence
The rapid proliferation of AI tools into many different roles creates opportunities, but it also comes with security concerns. Over 60% of knowledge workers use generative AI tools like ChatGPT in daily tasks.
AI cybersecurity awareness topics to teach employees include the danger of feeding confidential or sensitive data into these tools, and the use of generative AI by threat actors to create convincing phishing emails or other scams.
12. Physical Security
Somewhat surprisingly, physical security and cybersecurity are closely linked. Physical security lapses like letting strangers into the office, not disposing of printed sensitive info securely, or leaving workstations unlocked all pose cyber risks worth preventing.
Don’t forget that the boundaries between physical and digital security are blurring. IoT devices collect data from the physical world, and OT systems control physical processes. A security breach can have real-world consequences, so consider the best security practices for each if they apply to your business.
13. Incident Reporting Procedures
Any incident response plan should include procedures and steps to report security incidents. However, for this plan to be effective, your employees must know the exact steps they should take if they suspect a security incident. Your security awareness training needs to familiarize employees with whom to contact and what information to include if they need to report something suspicious.
14. Security Policies and Procedures
Lastly, include awareness training about your company’s specific security policies and procedures. These include regulatory requirements for the industry you operate in, acceptable use policies, how to classify and handle different types of data, and any policies about the use of personal devices for work reasons.
CybeReady: Proven Training with Up-to-Date Cybersecurity Awareness Topics
Ensuring that your team receives cybersecurity awareness training that covers a broad range of topics with the latest updates is essential to it being effective. But equally important is making sure that critical information is retained—and that comes down to how it’s taught.
CybeReady’s fully managed training solution leverages data to optimize the learning experience for every one of your employees. It takes a proven training approach to security awareness, with a continuous learning paradigm involving hands-on experience, a variety of training simulations, positive and short content, and immediate feedback—all designed for maximum engagement, retainment, and effectiveness.
Discover how CybeReady teaches the cybersecurity awareness topics you need by scheduling a free demo today.

Your Employees are Already Using GenAI. How Will You Communicate the Security Risks?
August 15,2024

Let the Games Begin! A Security Awareness Training (and a personal story) Inspired by the Olympic Spirit
May 19,2024

Jiu-Jitsu Principles in Security Awareness Training: A DevOps Engineer's Perspective
April 17,2024
Get the latest & greatest cybersecurity insights straight to your inbox:

Get the latest & greatest cybersecurity insights straight to your inbox:

- Take a Virtual Tour
- Security Awareness Bites
- Phishing Simulations
- Compliance Tool
- Elastic Security Program
- Banking Industry
- Education Industry
- Manufacturing Industry
- Pharmaceutical Industry
- Why CybeReady
- Partner Program
- CISO Toolkit
- HI-5 With A CISO
- Phishing Playbook
- Interactive Learning Kits
Copyright © 2024 – CybeReady
We will reach out to you shortly. In the meantime, please check out our complimentary CISO Tool Kit
We will reach out to you shortly. In the meantime, please check out our complimentary CISO Tool Kit , or visit Our Blog
Got any suggestions?
We want to hear from you! Send us a message and help improve Slidesgo
Top searches
Trending searches

suicide prevention
9 templates

27 templates

hispanic heritage month
21 templates

american history
85 templates

17 templates

109 templates
Cyber Security Roadmap
It seems that you like this template, cyber security roadmap presentation, premium google slides theme, powerpoint template, and canva presentation template.
In the rapidly evolving digital landscape, the importance of robust cyber security cannot be overemphasized. This Cyber Security Roadmap template for Google Slides and PowerPoint provides a roadmap to ensure the safety of your digital assets. Constructed with a cool, modern blue aesthetic, it instills both confidence and serenity. It showcases a range of factors from threat identification to mitigation measures. This visual timeline indicates the consequent actions and strategies in an easy-to-understand format. Gear up to protect and advance in your cyber journey with this powerful tool.
Features of this template
- 100% editable and easy to modify
- 35 different slides to impress your audience
- Contains easy-to-edit graphics such as graphs, maps, tables, timelines and mockups
- Includes 500+ icons and Flaticon’s extension for customizing your slides
- Designed to be used in Google Slides, Canva, and Microsoft PowerPoint
- 16:9 widescreen format suitable for all types of screens
- Includes information about fonts, colors, and credits of the resources used
What are the benefits of having a Premium account?
What Premium plans do you have?
What can I do to have unlimited downloads?
Don’t want to attribute Slidesgo?
Gain access to over 30000 templates & presentations with premium from 1.67€/month.
Are you already Premium? Log in

Register for free and start downloading now
Related posts on our blog.

How to Add, Duplicate, Move, Delete or Hide Slides in Google Slides
How to Change Layouts in PowerPoint
How to Change the Slide Size in Google Slides
Related presentations.
10 Cybersecurity Topics to Cover in 2024

As we navigate through the complex and ever-evolving digital landscape of 2024, the significance of cybersecurity has escalated dramatically. With advancements in technology moving at a breakneck pace, both individuals and organizations are confronted with multifaceted cybersecurity challenges. To navigate these challenges effectively, it is essential to understand and address the key cybersecurity topics of today. This article aims to delve into these topics, emphasizing the critical role of security awareness and proactive measures, alongside the pivotal importance of human risk management in mitigating these threats.
1. Social Engineering
Social engineering remains a significant threat within the cybersecurity domain, cleverly exploiting human psychology rather than relying solely on technical vulnerabilities to gain unauthorized access to systems, data, or personal information. Common tactics include phishing, pretexting, and baiting, with phishing being particularly nefarious due to its role in business email compromise (BEC) schemes. These attacks, often orchestrated by malicious actors, underscore the necessity for heightened awareness and critical scrutiny of unsolicited communications. To bolster protection against social engineering, it is crucial to educate employees on the importance of verifying sources and recognizing common phishing indicators, thereby reducing the attack surface available to attackers. Incorporating security awareness training on these topics can significantly enhance an organization's resilience against these forms of manipulation.
2. Ransomware
Ransomware continues to be a formidable threat in 2024, with malicious actors locking access to critical data or systems and demanding ransom for their release. This form of attack has seen a diversification in methods, including sophisticated phishing campaigns aimed at facilitating business email compromise. Preventative measures are essential for protection against ransomware threats, emphasizing the importance of regular data backups, timely security updates, and comprehensive phishing awareness programs to educate employees on the risks and mitigation strategies. Security awareness training topics should cover the nuances of ransomware attacks, equipping employees with the knowledge to identify and respond effectively to such threats.
3. Password Management
In the face of advanced cybersecurity threats, robust password management has become a cornerstone of digital protection. The limitations of traditional password strategies have paved the way for the adoption of password managers and the implementation of multi-factor authentication (MFA), enhancing access security. Promoting awareness around the creation and management of strong, unique passwords across different accounts, coupled with regular updates, is crucial for maintaining a secure digital environment. Educating users on the dangers of password reuse and the benefits of using advanced authentication methods can further secure digital identities against unauthorized access.
4. Mobile Security
The increasing reliance on mobile devices has expanded the attack surface for cyber threats, making mobile security a critical area of focus. Common threats include app-based risks, unsecured Wi-Fi connections, and the physical theft of devices. Recommendations for enhancing mobile device protection include the use of VPNs, commitment to regular software updates, and practicing secure app usage, all aimed at safeguarding access to sensitive information. Additionally, enforcing device encryption and secure lock-screen mechanisms can provide an extra layer of security against unauthorized access, especially in case of device loss or theft.
5. Cloud Security
The shift towards cloud services has introduced unique security challenges, particularly concerning data breaches and insecure APIs. Strategies for cloud environment protection emphasize the shared responsibility model, highlighting the importance of access management and the implementation of effective threat detection mechanisms. Regular security assessments and the adoption of robust encryption methods for data at rest and in transit are critical for safeguarding sensitive information stored in the cloud. Ensuring cloud security necessitates a comprehensive focus on protection measures, including regular security assessments and adherence to best practices for securing data access.
6. Data Privacy
The importance of data privacy has surged in 2024, with new regulations and increased consumer awareness driving the need for enhanced protection measures. Technologies such as encryption play a vital role in securing data, alongside practices like data masking. Implementing strict data handling and retention policies can also contribute to maintaining privacy and complying with regulatory requirements. Maintaining data privacy requires ongoing awareness efforts, regular privacy audits, and updates to privacy policies to ensure robust protection of sensitive information.
7. Remote Working
The rise of remote working has introduced new cybersecurity vulnerabilities, necessitating a focus on securing home networks and managing the use of personal devices for work purposes. Effective strategies for securing remote work environments include the use of secure connections, adoption of endpoint detection and response (EDR) tools, and the deployment of comprehensive training programs to increase employee awareness and resilience against cyber threats. Human Risk Management plays a crucial role in this context, emphasizing the need for ongoing security awareness training to address the evolving challenges of remote work. As remote work becomes increasingly prevalent, organizations must adapt their cybersecurity measures to protect sensitive data and mitigate the risks associated with remote access.
8. AI and Machine Learning
AI and machine learning have become integral to enhancing cybersecurity defenses, offering advanced capabilities in threat detection and automated security responses. However, these technologies also present potential vulnerabilities that require vigilant monitoring and management to prevent exploitation by malicious actors. The balance between leveraging AI for protection and addressing its inherent risks is crucial for maintaining a strong cybersecurity posture. As AI and machine learning technologies continue to evolve, organizations must remain vigilant in assessing their cybersecurity implications and implementing appropriate safeguards to protect against emerging threats.
9. Internet of Things
The proliferation of IoT devices has significantly increased the attack surface for cyber threats. Securing these devices involves strategies such as network segmentation, regular firmware updates, and strong authentication measures, underscoring the importance of comprehensive awareness and protection efforts to mitigate the risks associated with IoT environments. As IoT adoption continues to grow, organizations must prioritize IoT security measures to prevent unauthorized access and protect sensitive data from exploitation.
10. Human Risk Management
The role of human behavior in cybersecurity cannot be overstated, with strategies for reducing human error encompassing comprehensive security training and awareness programs. Cultivating a security-conscious culture within organizations is essential for enhancing overall protection and mitigating the risks posed by cyber threats. Security awareness training plays a pivotal role in human risk management, providing employees with the knowledge and skills to navigate the complex cybersecurity landscape effectively. Organizations must prioritize security awareness training topics that address human-centric vulnerabilities and promote a culture of cybersecurity awareness.
Step Forward in Cybersecurity with Living Security
In summary, navigating the cybersecurity landscape of 2024 demands a multifaceted approach, combining technological solutions with an emphasis on human risk management to address the myriad of challenges presented. By fostering awareness, implementing robust protection strategies, and focusing on critical areas such as access control, threat detection, and employee education, individuals and organizations can significantly enhance their security posture. Living Security stands ready to lead this journey, offering innovative solutions that seamlessly integrate into comprehensive cybersecurity strategies. Embrace the next step in cybersecurity with Living Security, and strengthen your defenses against the evolving digital threats of today and tomorrow.
- Artificial Intelligence
- Generative AI
- Business Operations
- IT Leadership
- Application Security
- Business Continuity
- Cloud Security
- Critical Infrastructure
- Identity and Access Management
- Network Security
- Physical Security
- Risk Management
- Security Infrastructure
- Vulnerabilities
- Software Development
- Enterprise Buyer’s Guides
- United States
- United Kingdom
- Newsletters
- Foundry Careers
- Terms of Service
- Privacy Policy
- Cookie Policy
- Member Preferences
- About AdChoices
- E-commerce Links
- Your California Privacy Rights
Our Network
- Computerworld
- Network World

The most important cybersecurity topics for business executives
Data privacy, current cyberthreats, and cybersecurity culture and training top the list, but are these the right priorities.

Industry rhetoric suggests that cybersecurity is an important topic in corporate boardrooms and C-suites, but according to a recent ESG survey, this is only partly true. While 58% of senior cybersecurity and business managers say that their organization’s C-level executives’ commitment and buy-in to cybersecurity is “very good,” the remaining 42% say that their organization’s C-level executives’ commitment and buy-in to cybersecurity is “adequate, fair, or poor.”
Not so good.
Survey respondents were also asked which cybersecurity topics were most important to the executive team. Here are the results and a bit of analysis:
- Data privacy. Data privacy topped the list at 35%, and this makes sense given regulations like GDPR and CCPA . In the past, data privacy was handled by legal teams, but with the onset and growth of regulations, CISOs have been asked to operationalize data privacy. In other words, security teams are responsible for things like data discovery, the introduction of new data security controls, and coordination around technologies for data deletion. GDPR also comes with the potential for hefty fines, so executives are paying close attention. Given that GDPR came out of the EU, it is not surprising that 39% of European organizations viewed data privacy as a high priority, compared to 33% of North American firms, according to ESG’s research.
- Current cyberthreats. Nearly one-third (32%) of business and cybersecurity executives believe that executives want to know about current cyberthreats, and it is worth noting that this research was conducted before the SolarWinds hack . To be clear, CEOs have no interest in details like indicators of compromise or MITRE ATT&CK framework tactics/techniques, but they do want details about what’s happening in general, what’s happening in their industry, whether their organization is vulnerable, and, if so, what’s needed for risk mitigation. Many CISOs I spoke to in this research project create cyberthreat reports proactively for executives and corporate boards—especially after a noteworthy publicly-disclosed data breach.
- Cybersecurity culture and training. This was a priority for 29% of organizations, but that doesn’t tell the whole story. As part of this research project, ESG created a scoring system that divided organizations into two categories: “Good security” organizations that emphasized cybersecurity within the business, and “good enough security” organizations that minimized their commitment to cybersecurity. Using this segmentation model, 39% of “good security” organizations prioritize cybersecurity culture and training, compared to 24% of “good enough security” firms. This difference is really a microcosm of cybersecurity today. “Good security” organizations are built with a cybersecurity culture as a foundation. Consequently, they are more secure down to the people and process levels. They also tend to accel in areas like business agility and IT resilience. “Good enough security” organizations still think of cybersecurity in terms of technology and compliance. They cover the basics—same as they did when PCI DSS was introduced in 2006.
While these were the top three priorities, it’s also worth examining others that were further down the list. For example, only 23% of organization said that, “alignment of security with key business initiatives” was an important topic for executives. Wow, really? This truly illustrates a cybersecurity disconnect at many organizations, but in this case, the blame really lives with IT and cybersecurity executives—only 19% of technologists said this was a business executive priority, compared to 29% of business executives. So, business managers want this information while technologists are somewhat oblivious to their needs. Cybersecurity ships passing in the night.
Similarly, only 21% of respondents believe that third-party risk management and/or vendor risk management was an important executive topic. Even before SolarWinds, there was Target , OPM , and the NotPetya -based attacks on Ukraine , Maersk , etc., so you’d think executives would want some guidance in this area.
Based upon my analysis of the data, it seems like many business and cybersecurity executives still haven’t figured out what’s most important and how to communicate effectively with one another. This gap leads them to focus on obvious and easy topics rather than the cybersecurity priorities that align with the business mission and objectives.
The research does indicate that some (about 33%) of organizations have figured things out, with cybersecurity truly integrated into the business. What are these firms doing? More on that soon.
Related content
The us offers a $2.5m bounty for the arrest of angler exploit kit co-distributor, ransomhub, play, akira: die gefährlichsten ransomware-banden, sellafield drohte it-gau: massive security-lücken in britischer atomanlage, microsoft onedrive und google drive als angriffsbasis: hacker verstecken sich in der cloud, from our editors straight to your inbox.

Jon Oltsik, is a former distinguished analyst and fellow at the Enterprise Strategy Group and the founder of its cybersecurity practice in 2003. Jon remains active in the cybersecurity community, writing, consulting, and working with CISOs, cybersecurity practitioners, threat intelligence analysts, and security technology vendors.
More from this author
5 best practices for running a successful threat-informed defense in cybersecurity, sometimes the cybersecurity tech industry is its own worst enemy, cybersecurity at a crossroads: time to shift to an architectural approach, microsoft’s mea culpa moment: how it should face up to the csrb’s critical report, esg/issa-studie: wie cisos den fachkräftemangel sehen, the cybersecurity skills shortage: a ciso perspective, improving cybersecurity culture: a priority in the year of the ciso, a tougher balancing act in 2024, the year of the ciso, show me more, ciso budget survey: modest increases in 2024.

White House brands BGP routing a ‘national security concern’ as it unveils reform roadmap

Palo Alto closes IBM QRadar SaaS buy, extends security partnership

CSO Executive Sessions: Guardians of the Games - How to keep the Olympics and other major events cyber safe

CSO Executive Session India with Dr Susil Kumar Meher, Head Health IT, AIIMS (New Delhi)

CSO Executive Session India with Charanjit Bhatia, Head of Cybersecurity, COE, Bata Brands

CSO Executive Sessions: Hong Kong Baptist University’s Allan Wong on security leadership

CSO Executive Sessions: EDOTCO’s Mohammad Firdaus Juhari on safeguarding critical infrastructure in the telecommunications industry


- Penetration Testing|The Ultimate Tool for Cyber Security Assessment
- Internal Network Penetration Testing| Are You Protected Against Internal Security Threats?
- Incident Response|Comprehensive Expert Help After a Security Incident
- Computer Forensics|Arm Your Legal Team with Digital Evidence
- Expert Witness Services|Build Your Case with Kevin's Expertise
- Security Awareness Training|Your Comprehensive Security Training Library
- Vulnerability Assessment|See Your System Through the Eyes of a Hacker
- Product Claims Testing|Get Unbiased Proof From the Best in the Business
- Red Team Operations|Evaluate Your Response to An Active Data Breach
- Social Engineering Strength Testing|Safeguarding Your Security From Human Manipulation
- The Art of Invisibility|The World's Most Famous Hacker Teaches You How to Be Safe in the Age of Big Brother and Big Data
- Ghost in the Wires|My Adventures as the World's Most Wanted Hacker: A New York Times Bestseller
- The Art of Intrusion|The Real Stories Behind the Exploits of Hackers, Intruders and Deceivers
- The Art of Deception|Controlling the Human Element of Security
- About Kevin|Whether you call him famous or infamous, Kevin Mitnick is one of a kind.
- Global Ghost Team|The Best of the Best In Cyber Security and Pentesting, Handpicked for Your Team
- Our Clients|Our Legacy of Extraordinary Services for Extraordinary Clients
- Testimonials & Reviews|Approved Quotes about Kevin's Live Hacking Appearances
- Press Archives|The Latest Cybersecurity Articles & News About Kevin Mitnick & Mitnick Security
- Media Kit|Bureau-Friendly Material For Your Website, E-mail and Print Needs
- FAQs|Explore answers to commonly-asked questions from fans, clients, colleagues and everyone in between.
- Blog|The latest news from Kevin Mitnick and the Global Ghost Team
- Virtual Events|Unsurpassed Experience in Successful Online Events and Trainings
- Lockpick Business Card|Learn More About the Card That Opens Doors Around the World
- Submit a Proposal|Contact Kevin’s Team With Your Proposal or Business Opportunity
- Join the Team|Do You Want to Work With Us?
Online Cyber Security Education and Training With Mitnick Security
It’s no surprise that the world’s “Most Famous Hacker” became a wildly entertaining virtual keynote speaker on all matters cyber security.
Kevin Mitnick’s flair for showmanship and detailed demonstrations made his live cyber security education events truly a thing of magic. Here we bring you a collection of Kevin’s teachings, how they came to be, and how they can help you and your team learn the essentials to cyber security.
Cyber Security Training: The Mitnick Difference
Kevin’s innovative ideas and expertise.
Kevin was one of the pioneers of social engineering and spent a large portion of his life innovating social engineering methodologies.
Growing up, Kevin was fascinated by the inner workings of telephone company switches and circuits. He was also a master of practical jokes; he once tweaked the house phone of a person he didn't like so that whenever the line was picked up, a recording requested a 25-cent deposit.
While Kevin never hacked with malicious intent, his actions did catch up to him in the 1980s, when he received prison time and counseling for computer addiction following his conviction for hacking into corporate computer systems. The same year he was released from prison, he was hired by a California college— one of his former hacking targets — for cybersecurity guidance. Kevin referred to this arrangement as “hire a hacker”. This arrangement was entirely unique to Kevin alone, a testament to his expertise and mastery of cybersecurity.
Kevin went on to create Mitnick Security Consulting, where he, alongside his team of elite security consultants — The Global Ghost Team™ — would deliver unmatched services, such as penetration testing , and offer organizations cyber security education live from the stage.
These cyber security training events created a lasting impact on how people and companies protect their most sensitive information and remediate being hacked.

Kevin’s Hybrid Approach to Teaching
As more and more employees continued to enjoy the convenience and safety of working from home, however, Kevin knew he needed to adapt his teachings. Kevin realized the opportunity lay in taking a hybrid learning approach; video conferences became commonplace, yet teams were still eager to learn about cyber security education and training. Even with live events back in swing, it was still difficult for dispersed remote workers to gather in the same room.
Kevin didn’t just take a hybrid approach; however, he knew he could expand his audience and help teams worldwide by adapting his most popular stage shows into engaging virtual webcasts and webinars. And boy, did his idea take off. That’s because Kevin was already an active remote speaker— as the face of the world’s most successful virtual cyber security training program, KnowBe4 — so the switch was a smooth one.
Kevin would go on to work with and train teams from some of the most renowned companies worldwide to harden their cybersecurity.
Who We've Worked With

Cyber Security Education and Training From Kevin Mitnick
Reviews & Testimonials for Kevin Mitnick

Kevin delivered a fantastic event for Lloyds Banking Group in July 2021. It was far from the normal, often stuffy or scripted, interviews that many organisations seem to undertake. The packed house of engineering, security, and colleagues from across the business really enjoyed the history, anecdotes, and insights. It clearly struck a chord with wide-ranging feedback indicating that it was the most successfully and engaging event of its kind that the group has ever run. Kevin’s team were fantastic and supporting at all stages, tangibly assisting in improving the value of the event. I look forward to working with Kevin and his team again in the near future and cannot recommend getting in touch to enlist their services most strongly.
- Chris Thompson - Engineering Lead and Head of Cloud Strategy in Insurance and Wealth - LLOYDS BANKING GROUP

We really loved the conversation and we're super happy with the execution. Our goal for virtual attendees was exceeded by 40% so we knocked it out of the park!
- Lisa Hoang - Program Marketing Manager, Public Sector - RED HAT

For one of the world’s biggest cyber celebrities, he was pretty darn down to earth, generous, easy to work with, and of course, knew his stuff!
- James Brodsky - Senior Director, Global Security Strategists - SPLUNK

Kevin did a great job holding the audience's attention for 75 virtual minutes :-) His points definitely resonated with the audience. His real-life examples and demonstrations made for a captivating and memorable experience.
- Ashley Barnes (Jones) - Conference Program Manager - INSTITUTE OF INTERNAL AUDITORS (IIA)

Kevin Mitnick and his team provided helpful promotional materials, valuable planning time, essential script and talking points, along with very engaging demonstrations. Mr. Mitnick and his team worked with our own cybersecurity experts to ensure that our presentation was not only entertaining and interesting but easily understood and relevant to our audience.
- Jennifer Duval, Lead Channel Manager - AT&T.

Kevin's participation in our speaker series was nothing short of amazing. The flow, topical subject matter, and engaging demos really hit the mark for our customers."
- Kevin Williams , Vice President of Identity and Data Protection - Thales.
Choose Mitnick Security for Cyber Security Education and Services
While we have many cyber security education resources just for you, we also offer several cyber security services designed to help companies just like yours!

- The Art of Invisibility
- Ghost in the Wires
- The Art of Intrusion
- The Art of Deception
- About Kevin
- Global Ghost Team
- Our Clients
- Testimonials/Reviews
- Press Archives
SECURITY SERVICES
- Penetration Testing
- Internal Network Penetration Testing
- Incident Response
- Computer Forensics
- Expert Witness Services
- Security Awareness Training
- Vulnerability Assessment
- Product Claims Testing
- Red Team Operations
- Social Engineering Strength
- Lockpick Business Card
- Virtual Webinar Recordings
SEARCH MITNICKSECURITY.COM
- Submit a Proposal
- Join The Team
Toll Free (USA & Canada) (855) 411-1166 Local and International (702) 940-9881
Security Services and Support: [email protected] Engagements and Media: [email protected]
Join Our Mailing List

© Copyright 2004 - 2024 Mitnick Security Consulting LLC. All rights Reserved. | Privacy Policy

COMMENTS
Struggling to find the next seminar topic on cybersecurity? In this guide, you'll find 16 trending seminar presentation topics on cybersecurity.
In this article, we list down 10 popular presentations on cybersecurity one must read on Slideshare. 1. Artificial Intelligence And Cybersecurity. This presentation was published in March 2019 by Olivier Busolini, a cybersecurity professional who also works with AI in cybersecurity. This presentation includes a basic introduction to AI, an ...
Looking for latest cyber security research topics of 2024? Here is a list of 105 research ideas along with the cyber security research areas, tips to choose the best topic from experts and more.
In this article, we delve into the most critical and latest topics in cybersecurity, aiming to educate and raise awareness about safeguarding sensitive data and maintaining digital privacy.
Template 3 Cyber Security Risk Management PPT Presentation Slides With the business world increasingly using the internet as a significant raw material in its processes, this presentation template details how to handle cybersecurity threats and secure digital assets.
This blog post will examine some of the most common security awareness training topics, including phishing scams, social engineering, ransomware, and more. Educating your employees on these cyber security awareness topics will help your company stay secure, reduce human error, avoid data breaches, and become an overall security aware workforce.
Cyber security topics for presentation Cybersecurity safeguards sensitive data, preserves trust, and defends against evolving cyber threats in our digital world.
Upgrade your cybersecurity in 2023 with our 10 key topics for a comprehensive security awareness training program. Empower your organization
NIST Cybersecurity Fundamentals Presentation Download the Slides Managing a small business is always challenging but keeping up with cybersecurity threats can be overwhelming. How do you learn about the latest threats? How do you educate your staff about best practices?
A collection of TED Talks (and more) on the topic of Cyber security.
Download Cyber Security PPT Presentation, Template & Slides. Cyber security is one of the most important aspects of online life. SlideTeam has created cyber security ppts that will give you that foundation so you can protect your business from data breaches, ransomware attacks, and other malicious activities. Without the proper knowledge of the ...
This presentation also includes an introduction to red and blue AI technologies and a list of organizations that are using AI to follow cybersecurity practices to secure their information. Therefore, with AI and Cybersecurity presentations, learners can get a brief idea of cybersecurity solutions.
Security leaders can refer to this quick guide on delivering a 15-minute cybersecurity presentation to the board.
Here are fourteen pertinent cybersecurity awareness topics your training program must cover to be effective. Learn more with CybeReady.
Delivering a concise and impactful five-minute cybersecurity presentation can be challenging, especially when addressing a large group of potential clients or partners. However, with a clear structure, focused content, and engaging delivery, you can captivate your audience and leave a lasting impression. Here's a step-by-step guide tailored for C-suite executives in the cybersecurity sector.
This Cyber Security Roadmap template for Google Slides and PowerPoint provides a roadmap to ensure the safety of your digital assets. Constructed with a cool, modern blue aesthetic, it instills both confidence and serenity. It showcases a range of factors from threat identification to mitigation measures. This visual timeline indicates the ...
The 15-Minute, 7-Slide Security Presentation for Your Board of Directors. Help the board understand why cybersecurity is critical to the business. When the request comes in to give a cybersecurity presentation to the board, security leaders should jump at the chance to educate the executives. However, a lengthy, in- depth presentation is more ...
Discover the 7 most important cyber safety topics you should learn about from the Norton blog. Click to read more.
SEC403: Secrets to Successful Cybersecurity Presentation. SEC403 shows you how to put together an effective security briefing, secure the interest and engagement of your audience, and confidently deliver presentations to a variety of groups. You will learn effective techniques to secure management approval for new security projects and tools ...
Explore key cybersecurity topics for 2024 including AI risks, evolving cyber laws, IoT security, and more. Stay informed and protect your digital world.
Data privacy, current cyberthreats, and cybersecurity culture and training top the list, but are these the right priorities?
It's no surprise that the world's "Most Famous Hacker" became a wildly entertaining virtual keynote speaker on all matters cyber security. Kevin Mitnick's flair for showmanship and detailed demonstrations made his live cyber security education events truly a thing of magic. Here we bring you a collection of Kevin's teachings, how ...