- Skip to main content
- Keyboard shortcuts for audio player

After Data Breach Exposes 530 Million, Facebook Says It Will Not Notify Users

Emma Bowman

The leaked data includes personal information from 533 million Facebook users in106 countries. Olivier Douliery/AFP via Getty Images hide caption
The leaked data includes personal information from 533 million Facebook users in106 countries.
Facebook decided not to notify over 530 million of its users whose personal data was lifted in a breach sometime before August 2019 and was recently made available in a public database. Facebook also has no plans to do so, a spokesperson said.
Phone numbers, full names, locations, some email addresses, and other details from user profiles were posted to an amateur hacking forum on Saturday, Business Insider reported last week.
The leaked data includes personal information from 533 million Facebook users in 106 countries.
In response to the reporting, Facebook said in a blog post on Tuesday that "malicious actors" had scraped the data by exploiting a vulnerability in a now-defunct feature on the platform that allowed users to find each other by phone number.

National Security
After a major hack, u.s. looks to fix a cyber 'blind spot'.
The social media company said it found and fixed the issue in August 2019 and its confident the same route can no longer be used to scrape that data.
"We don't currently have plans to notify users individually," a Facebook spokesman told NPR.
According to the spokesman, the company does not have complete confidence in knowing which users would need to be notified. He also said that in deciding whether to notify users, Facebook weighed the fact that the information was publicly available and that it was not an issue that users could fix themselves.
The information did not include financial information, health information or passwords, Facebook said, but the data leak still leaves users vulnerable, security experts say.
"Scammers can do an enormous amount with little information from us," says CyberScout founder Adam Levin, a cybersecurity expert and consumer protection advocate. In the case of this breach, he said, "It's serious when phone numbers are out there. The danger when you have phone numbers in particular is a universal identifier."
Phone numbers are increasingly used to connect people to their digital presence, including the use of two-factor authentication via text message and phone calls to verify one's identity.

FTC To Hold Facebook CEO Mark Zuckerberg Liable For Any Future Privacy Violations
The misuse of its user data is a familiar battle for Facebook, and its handling of user privacy has endured scrutiny.
In July 2019, months before patching up the aforementioned issue, Facebook reached a $5 billion settlement with the U.S. Federal Trade Commission for violating an agreement with the agency to protect user privacy.
To find out whether your personal information was leaked in the breach, you can check the data tracking tool, HaveIBeenPwnd . Its creator, Troy Hunt, updated the site with the latest data from the Facebook leak. Hunt said that 65% of the latest batch of data had already been added to the tracker from previous leaks.
Editor's note: Facebook is among NPR's financial supporters.
To revisit this article, visit My Profile, then View saved stories .
- The Big Story
- Newsletters
- Steven Levy's Plaintext Column
- WIRED Classics from the Archive
- WIRED Insider
- WIRED Consulting
Everything We Know About Facebook's Massive Security Breach

Facebook’s privacy problems severely escalated Friday when the social network disclosed that an unprecedented security issue, discovered September 25, impacted almost 50 million user accounts. Unlike the Cambridge Analytica scandal, in which a third-party company erroneously accessed data that a then-legitimate quiz app had siphoned up, this vulnerability allowed attackers to directly take over user accounts.
The bugs that enabled the attack have since been patched, according to Facebook. The company says that the attackers could see everything in a victim's profile, although it's still unclear if that includes private messages or if any of that data was misused. As part of that fix, Facebook automatically logged out 90 million Facebook users from their accounts Friday morning, accounting both for the 50 million that Facebook knows were affected, and an additional 40 million that potentially could have been. Later Friday, Facebook also confirmed that third-party sites that those users logged into with their Facebook accounts could also be affected .
Facebook says that affected users will see a message at the top of their News Feed about the issue when they log back into the social network. "Your privacy and security are important to us," the update reads. "We want to let you know about recent action we've taken to secure your account." The message is followed by a prompt to click and learn more details. If you were not logged out but want to take extra security precautions, you can check this page to see the places where your account is currently logged in, and log them out.
Facebook has yet to identify the hackers, or where they may have originated. “We may never know,” Guy Rosen, Facebook’s vice president of product, said on a call with reporters Friday. The company is now working with the Federal Bureau of Investigation to identify the attackers. A Taiwanese hacker named Chang Chi-yuan had earlier this week promised to live-stream the deletion of Mark Zuckerberg's Facebook account, but Rosen said Facebook was "not aware that that person was related to this attack."
“If the attacker exploited custom and isolated vulnerabilities, and the attack was a highly targeted one, there simply might be no suitable trace or intelligence allowing investigators to connect the dots,” says Lukasz Olejnik, a security and privacy researcher and member of the W3C Technical Architecture Group.
On the same call, Facebook CEO Mark Zuckerberg reiterated previous statements he has made about security being an “arms race.”
“This is a really serious security issue, and we’re taking it really seriously,” he said. “I’m glad that we found this, and we were able to fix the vulnerability and secure the accounts, but it definitely is an issue that it happened in the first place.”

The social network says its investigation into the breach began on September 16, when it saw an unusual spike in users accessing Facebook. On September 25, the company’s engineering team discovered that hackers appear to have exploited a series of bugs related to a Facebook feature that lets people see what their own profile looks like to someone else. The " View As " feature is designed to allow users to experience how their privacy settings look to another person.
The first bug prompted Facebook's video upload tool to mistakenly show up on the "View As" page. The second one caused the uploader to generate an access token—what allows you to remain logged into your Facebook account on a device, without having to sign in every time you visit—that had the same sign-in permissions as the Facebook mobile app. Finally, when the video uploader did appear in "View As" mode, it triggered an access code for whoever the hacker was searching for.
“This is a complex interaction of multiple bugs,” Rosen said, adding that the hackers likely required some level of sophistication.
That also explains Friday morning's logouts; they served to reset the access tokens of both those directly affected and any additional accounts “that have been subject to a View As look-up” in the last year, Rosen said. Facebook has temporarily turned off "View As," as it continues to investigate the issue.
“It’s easy to say that security testing should have caught this, but these types of security vulnerabilities can be extremely difficult to spot or catch since they rely on having to dynamically test the site itself as it’s running,” says David Kennedy, the CEO of the cybersecurity firm TrustedSec.
The vulnerability couldn’t have come at a worse time for Facebook, whose executives are still reeling from a series of scandals that unfolded in the wake of the 2016 US presidential election. A widespread Russian disinformation campaign leveraged the platform unnoticed, followed by revelations that third-party companies like Cambridge Analytica had collected user data without their knowledge.
The social network already faces multiple federal investigations into its privacy and data-sharing practices, including one probe by the Federal Trade Commission and another conducted by the Securities and Exchange Commission. Both have to do with its disclosures around Cambridge Analytica.
It also faces the specter of more aggressive regulation from Congress, on the heels of a series of occasionally contentious hearings about data privacy. After Facebook’s announcement Friday, Senator Mark Warner (D-Virginia), who serves as vice chairman of the Senate Intelligence Committee, called for a “full investigation” into the breach. “Today’s disclosure is a reminder about the dangers posed when a small number of companies like Facebook or the credit bureau Equifax are able to accumulate so much personal data about individual Americans without adequate security measures,” Warner said in a statement. “This is another sobering indicator that Congress needs to step up and take action to protect the privacy and security of social media users.”
Facebook may also face unprecedented scrutiny in Europe, where the new General Data Protection Regulation , or GDPR, requires companies to disclose a breach to a European agency within 72 hours of it occurring. In cases of high risk to users, the regulation also requires that they be notified directly. Facebook says it has notified the Irish Data Protection Commission about the issue.
This is the second security vulnerability that Facebook has disclosed in recent months. In June, the company announced it had discovered a bug that made up to 14 million people’s posts publicly viewable to anyone for days. This is the first time in Facebook’s history, though, that users’ entire accounts may have been compromised by outside hackers. Its response to this vulnerability—and the speed and comprehensiveness of the important disclosures ahead—will likely be of serious importance. Once again, all eyes are on Mark Zuckerberg.
Additional reporting by Lily Hay Newman.
- Everyone wants to go to the moon— logic be damned
- College Humor gives comedy subscription a serious effort
- Tips to get the most out of Screen Time controls on iOS 12
- Tech disrupted everything. Who's shaping the future ?
- An oral history of Apple's Infinite Loop
- Looking for more? Sign up for our daily newsletter and never miss our latest and greatest stories


A Retrospective on the 2015 Ashley Madison Breach
It’s been seven years since the online cheating site AshleyMadison.com was hacked and highly sensitive data about its users posted online. The leak led to the public shaming and extortion of many Ashley Madison users, and to at least two suicides. To date, little is publicly known about the perpetrators or the true motivation for the attack. But a recent review of Ashley Madison mentions across Russian cybercrime forums and far-right websites in the months leading up to the hack revealed some previously unreported details that may deserve further scrutiny.

As first reported by KrebsOnSecurity on July 19, 2015 , a group calling itself the “ Impact Team ” released data sampled from millions of users, as well as maps of internal company servers, employee network account information, company bank details and salary information.
The Impact Team said it decided to publish the information because ALM “profits on the pain of others,” and in response to a paid “full delete” service Ashley Madison parent firm Avid Life Media offered that allowed members to completely erase their profile information for a $19 fee .
According to the hackers, although the delete feature promised “removal of site usage history and personally identifiable information from the site,” users’ purchase details — including real name and address — weren’t actually scrubbed.
“Full Delete netted ALM $1.7mm in revenue in 2014. It’s also a complete lie,” the hacking group wrote. “Users almost always pay with credit card; their purchase details are not removed as promised, and include real name and address, which is of course the most important information the users want removed.”
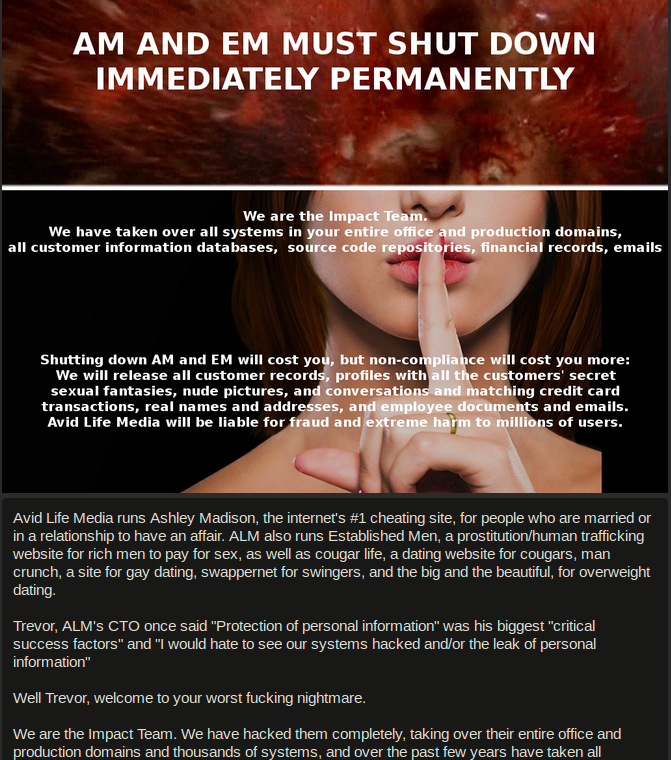
A snippet of the message left behind by the Impact Team.
The Impact Team said ALM had one month to take Ashley Madison offline, along with a sister property called Established Men. The hackers promised that if a month passed and the company did not capitulate, it would release “all customer records, including profiles with all the customers’ secret sexual fantasies and matching credit card transactions, real names and addresses, and employee documents and emails.”
Exactly 30 days later, on Aug. 18, 2015, the Impact Team posted a “Time’s up!” message online, along with links to 60 gigabytes of Ashley Madison user data.
AN URGE TO DESTROY ALM
One aspect of the Ashley Madison breach that’s always bothered me is how the perpetrators largely cast themselves as fighting a crooked company that broke their privacy promises, and how this narrative was sustained at least until the Impact Team decided to leak all of the stolen user account data in August 2015.
Granted, ALM had a lot to answer for. For starters, after the breach it became clear that a great many of the female Ashley Madison profiles were either bots or created once and never used again. Experts combing through the leaked user data determined that fewer than one percent of the female profiles on Ashley Madison had been used on a regular basis, and the rest were used just once — on the day they were created. On top of that, researchers found 84 percent of the profiles were male .
But the Impact Team had to know that ALM would never comply with their demands to dismantle Ashley Madison and Established Men. In 2014, ALM reported revenues of $115 million. There was little chance the company was going to shut down some of its biggest money machines.
Hence, it appears the Impact Team’s goal all along was to create prodigious amounts of drama and tension by announcing the hack of a major cheating website, and then letting that drama play out over the next few months as millions of exposed Ashley Madison users freaked out and became the targets of extortion attacks and public shaming .
Robert Graham , CEO of Errata Security, penned a blog post in 2015 concluding that the moral outrage professed by the Impact Team was pure posturing.
“They appear to be motivated by the immorality of adultery, but in all probability, their motivation is that #1 it’s fun and #2 because they can,” Graham wrote.
Per Thorsheim , a security researcher in Norway, told Wired at the time that he believed the Impact Team was motivated by an urge to destroy ALM with as much aggression as they could muster.
“It’s not just for the fun and ‘because we can,’ nor is it just what I would call ‘moralistic fundamentalism,'” Thorsheim told Wired . “Given that the company had been moving toward an IPO right before the hack went public, the timing of the data leaks was likely no coincidence.”
NEO-NAZIS TARGET ASHLEY MADISON CEO
As the seventh anniversary of the Ashley Madison hack rolled around, KrebsOnSecurity went back and looked for any mentions of Ashley Madison or ALM on cybercrime forums in the months leading up to the Impact Team’s initial announcement of the breach on July 19, 2015. There wasn’t much, except a Russian guy offering to sell payment and contact information on 32 million AshleyMadison users, and a bunch of Nazis upset about a successful Jewish CEO promoting adultery.
Cyber intelligence firm Intel 471 recorded a series of posts by a user with the handle “ Brutium ” on the Russian-language cybercrime forum Antichat between 2014 and 2016. Brutium routinely advertised the sale of large, hacked databases, and on Jan. 24, 2015, this user posted a thread offering to sell data on 32 million Ashley Madison users:
“Data from July 2015 Total ~32 Million contacts: full name; email; phone numbers; payment, etc.”
It’s unclear whether the postdated “July 2015” statement was a typo, or if Brutium updated that sales thread at some point. There is also no indication whether anyone purchased the information. Brutium’s profile has since been removed from the Antichat forum.
Flashpoint is a threat intelligence company in New York City that keeps tabs on hundreds of cybercrime forums, as well as extremist and hate websites. A search in Flashpoint for mentions of Ashley Madison or ALM prior to July 19, 2015 shows that in the six months leading up to the hack, Ashley Madison and its then-CEO Noel Biderman became a frequent subject of derision across multiple neo-Nazi websites.
On Jan. 14, 2015, a member of the neo-Nazi forum Stormfront posted a lively thread about Ashley Madison in the general discussion area titled, “Jewish owned dating website promoting adultery.”
On July 3, 2015, Andrew Anglin , the editor of the alt-right publication Daily Stormer , posted excerpts about Biderman from a story titled, “Jewish Hyper-Sexualization of Western Culture,” which referred to Biderman as the “Jewish King of Infidelity.”
On July 10, a mocking montage of Biderman photos with racist captions was posted to the extremist website Vanguard News Network , as part of a thread called “Jews normalize sexual perversion.”
“Biderman himself says he’s a happily married father of two and does not cheat,” reads the story posted by Anglin on the Daily Stormer. “In an interview with the ‘Current Affair’ program in Australia, he admitted that if he found out his own wife was accessing his cheater’s site, ‘I would be devastated.'”
The leaked AshleyMadison data included more than three years’ worth of emails stolen from Biderman . The hackers told Motherboard in 2015 they had 300 GB worth of employee emails, but that they saw no need to dump the inboxes of other company employees.
Several media outlets pounced on salacious exchanges in Biderman’s emails as proof he had carried on multiple affairs. Biderman resigned as CEO on Aug. 28, 2015. The last message in the archive of Biderman’s stolen emails was dated July 7, 2015 — almost two weeks before the Impact Team would announce their hack.
Biderman told KrebsOnSecurity on July 19, 2015 that the company believed the hacker was some type of insider.
“We’re on the doorstep of [confirming] who we believe is the culprit, and unfortunately that may have triggered this mass publication,” Biderman said. “I’ve got their profile right in front of me, all their work credentials. It was definitely a person here that was not an employee but certainly had touched our technical services.”
Certain language in the Impact Team’s manifesto seemed to support this theory, such as the line: “For a company whose main promise is secrecy, it’s like you didn’t even try, like you thought you had never pissed anyone off.”
But despite ALM offering a belated $500,000 reward for information leading to the arrest and conviction of those responsible, to this day no one has been charged in connection with the hack.
55 thoughts on “ A Retrospective on the 2015 Ashley Madison Breach ”
You’re the man Krebs. Keep up the great reporting.
agreed.. Senor Krebs is the man next to the Man. 85% fake profiles, just like twitter responses, facedump aka metaturd. How many other social media websites have fake accounts and are bs
I’m not seeing “85% of twitter is fake” except from Elong Musk’s titterbots…
Still can’t believe the number of real users that site had.. great reporting Brian, appreciate you.
Not that I’m pro nazi, but what the hell does that have to do with anything? I don’t guess you found any evidence of communists being upset with AM? Probably because they are okay with all the perversion. You seem to enjoy working your political angles into this stuff more and more. Can’t say I’m surprised.
Did you actually read the story before commenting, Jim? Not sure how you could come away with the conclusion that this story is somehow “political.”
The funny thing is that people are waving the word “political” around like a weapon because the USA is so polarised. They blindly rage without making any distinctions. It is entirely possible for a hack to be politically motivated and a reporter like you to simply report what their investigation found. The article would be about the hack and why the hack happened NOT about driving a political agenda. Knee jerk reactions without proper comprehension is pathetic.
“Knee jerk reactions without proper comprehension is pathetic.”
He loads the irony and cocks it, begins to clean the bore…
The mention of the DailyStormer seemed really out of left-field. You discussed a hack of the database and where it was leaked originally which makes sense. That was followed by seemingly unrelated hot-takes from a far-right site, it implies correlation between the two but rereading the article it’s not at all clear why.
It’s not clear why? Brian mentioned multiple times that discussion of AM, ALM, and its CEO picked up substantially in both cybercrime spaces and far right–and specifically Neo Nazi–in the months leading up to the hack. That is incredibly relevant, is it not?
Perhaps you should stop getting your undies in a bunch because Nazis were mentioned in a negative light.
“Not that I’m pro nazi, BUT”
Isn’t that a standard disclaimer for Steve Bannon and Alex Jones?
Good boy! Fight those Nazis from your mom’s basement
Incels, white chauvinists, and grown men living in their mom’s basement… are the ones most likely to be Trump supporters. Fighting Nazis should be done first online to stop the spread of hate speech and to prevent them from recruiting other young people. Shove them back into the shadows, back into the shameful corners of society, before they get too big and start goosestepping in the public square like they did in Charlottesville and the at the Capitol.
Definitely an important thing to preface everything you say with, if you’re NOT a nazi. xD
Jim Dewey has already shown he’s a Qanon believer on a previous article. Nazi sympathizer isn’t a stretch.
Imagine getting upset on behalf of nazis and then complaining someone else is being political. You sir, are the one being political here kek.
Why is it that any time nazis, fascists, or white supremacists mentioned “totally not nazi” folks pop up with “what about the communists/antifa???”
It’s remarkable how you all don’t speak up about “making things political” by popping up in Breitbart and comments about BLM with “yeah but what about Atomwaffen?”
If Brian was investigating a hack of a site and noted that a bunch of leftists had suddenly started discussing it a few months ago, would you be in here asking why he isn’t focusing on Nazis?
I guess we’ll never know because Brian only mentions right wingers as antagonists in his articles. You sympathizers always step up to the plate for him like an army of bots. The old saw is true. Birds of a feather stick together. Me? I’m just here to remind you not everyone is as naïve as you are. Have a nice day…
Must be hard to type with one hand while the other is either doing a Nazi salute, or giving your dear leader a reach around.
Zee boots are very tight!
Nazi involvement is relevant because back in WWII they murdered six million Jews and the CEO of Ashley Madison was Jewish. Correlation does not equal causation but the fact the politics have lined up in opposition before is part of the conversation.
What other “crooked companies” did Impact Team exact vengeance on for their “broken privacy promises?” My public email addresses was used by ALM to create a fake account; I never received any restitution from Impact Team.
“researchers found 84 percent of the profiles were male.” That low?
LOL – I was thinking the same thing – only 84% were males! “….fewer than one percent of the female profiles on Ashley Madison had been used on a regular basis, and the rest were used just once — on the day they were created..” Sounds like this ALM company was taking the proverbial piss out of men’s desires for sex to make alot of money. Cannot say my heart goes out to any of them.
Well….
It is a bit perplexing as to the identity of the Impact Team, when some many other groups have been tipped off and/or their members have been identified.
Somebody had a grudge, and in the end that could have been anyone from any particular nation. And there is no reason not to also consider this was a nation-state actor pulling this off as well. (Russian, Ukrainian, China, Iran, Israel, or the Five Eyes).
There was no financial gain, other than putting someone else of having a financial gain. And who knows what else? Ashley Madison for all we know was also into espionage and blackmail, besides the adultery overtones.
“.. nation state actor…” 🙂 If interested whodunit, just check this (Brian’s) blog. Optionally, see comments on: ‘site:schneier.com squid found on sandbar’
> a bunch of Nazis upset about a successful Jewish CEO promoting adultery. Poor successful CEO targeted by those mean Nazis! That sleazeball deserves no sympathy. Imagine making money off breaking people’s marriages. Who would come up with such an idea?
Corporate America would with glee. Have you ever read “Bold Capital” by T. J. Dunning? Here is the pertinent excerpt (discussing profit): “…; 100 per cent. will make it ready to trample on all human laws; 300 per cent., and there is not a crime at which it will scruple, nor a risk it will not run, even to the chance of its owner being hanged. If turbulence and strife will bring a profit, it will freely encourage both. Smuggling and the slave-trade have amply proved all that is here stated.”
” Imagine making money off breaking people’s marriages. Who would come up with such an idea?”
Imagine you having an opinion without understanding marriage, divorce, court, litigation, any of it? What you think they work for free? Are you from a communist country or just unburdened by reality?
So you could have left out the “mean Nazis” part and I may have agreed with you. But when you preface it that way it kinda feels like you might be pro-Nazi. SMH
No need to virtue signal here, Dave. This isn’t reddit.
Ah, the good old days. It’s been a while since I thought of Ashley or Seeking Arrangement. The moral of this story is always beware that engineer whom you shafted that also has your passwords, LOL…
Why does everyone hate the Jews?
Why are you perpetuating that everyone does as if it’s true?
I still wonder whether the Ashley Madison and OPM hacks were related. Imagine a list of adulterers with security clearances. Even if they’re not related, whoever has the OPM data could match it with the leaked Ashley Madison data.
Maybe in this case, not justifying a Hack, the results might be good ones. I mean : lessons learned guys, all those female profiles are mutually fake and you are surrounded by a group of men. I‘m really wondering about the amount of puppets / fake profiles around Twitter…
A bit on a tangent… but when companies/websites give you the option to delete/remove history, etc. – I’ve always wondered just how complete these “deletions” really are. Like when I “delete” my Google search/web/etc. history — is the info truly removed from all Google data centers – or just hidden from my view??
Any sentence that starts with “l’m not pro-N*zi” is right up there with “Some of my best friends are Jews”.
Maybe people criticizing a genocidal fascist hellscape are the “real” bigots? Maybe they just liked trains that run on time, leather boots and funny walks? Thought experiment, maybe Hitler was just really, really ironic yet inarticulate? I mean, were any of us there? Let’s try to keep an open mind about fascism. Everyone’s so quick to jump to “Earth is round” conclusions about things… jeez.
ohh mealy.. your so witty!! xoXO
Ha! So funny and original, mealy.
“Trusted Security Award.” “SSL Secure Site.” “100% Discreet Service.” LOL
I can’t believe Vanessa was a fembot.
Brian’s retrospective was great and prompted me to see if Ashley Madison is still around.
Apparently it is alive, although they go to great pains to say that they’ve dealt with the bot problem. Their explanation is carefully worded, especially since they created the bots / dummy accounts in the first place.
Digging deeper, it seems that their business model is largely based on monetizing internal message traffic between members. Effectively you pay to have a conversation with someone, whether it leads anywhere or not. In some ways, it’s in the provider’s best interest that someone does not consummate the deal (so to speak), and continues messaging members for an extended period.
I make no moral judgements about these users, but on these kind of sites, there really is leap of faith that the provider has very good security protections in place. This isn’t Equifax, so why someone would sign up or continue to give them their business is beyond me.
Well, if they were reputable then they will have backups of course (going way back), and if they were really reputable then they would not use them for nefarious purposes. The question is: given Google’s past, would you trust them?
BTW, Google is not the only search engine on the planet (I use DuckDuckGo, as do my colleagues; no, we have no connection with them apart from a common interest in privacy).
DuckDuckGo was criticized in May 2022 when researchers discovered that some Microsoft tracking scripts were found while using DuckDuckGo’s browsers. The presence of Microsoft trackers seems to fly in the face of the search engine’s privacy promise, and DuckDuckGo’s founder and CEO clarified on Reddit that the company is “currently contractually restricted by Microsoft” from stopping Microsoft scripts from completely loading because the company uses Microsoft’s Bing to power its search results.
Don’t trust Google? You trust Microsoft? And their affiliates? Internet Search Engines are free for users… which means we are the product they sell to others.
That’s night and day different : DDG isn’t selling the data. MS and Goog do so. DDG isn’t profiting from it. DDG doesn’t remove all internet tracking possible but it’s still better for it, and coupled with adblocking addons you can strip any residual trackers out. Equivocating MS and Google with DDG is not realistic.
Agreed. They aren’t equivalent. DDG is still far better than Bing, Google and others. And yes, people should absolutely overlap privacy protections with browser addons from other reputable sources. The EFF recommends a few. Just didn’t want people thinking just using DDG is an easy solution to all privacy concerns.
Of course I don’t trust M$ any more than I trust Google (there are many alternatives to both); my favourite OS is ABW i.e. “Anything But Windoze” (I’m currently using MacOS, FreeBSD, and Linux). Wasn’t aware of the DDG issue, but see previous statement. I also run adblockers which are quite effective, and whenever I encounter a site that insists I disable them then I go elsewhere or forget about it. I also watch ad-free (and free-to-air) TV.
Yes, I suppose you could call me an anti-commerce hippie…
That makes two of us Dave.
So let’s see: of the AM userbase, there were some ~84% male profiles, 15% fake female profiles, and maybe 1% or less real female profiles. So the “men” who signed up for affairs were really just joining a virtual sausage fest?
I have no sympathy for the cheaters who signed up for this site and had their personal information leaked to the web.
I never thought I could get scammed of my Bitcoin , I never new these investments were fake . I never knew I was getting lured into loosing my money , I was depressed and in anger but all thanks to Adam Wilson for the help and professional service offered to me in my time of need . Thanks to Kate for sending me this contact. Adamwilson. trading at consultant dot com helped me recover my lost funds from Bitcoin investment . I couldn’t believe it .
why u have js from gstatic.com? (bots?)
finally, its romance scam at its best for best agers.
Comments are closed.

Find anything you save across the site in your account
The National-Security Case for Fixing Social Media
On Wednesday, July 15th, shortly after 3 P.M. , the Twitter accounts of Barack Obama, Joe Biden, Jeff Bezos, Bill Gates, Elon Musk, Warren Buffett, Michael Bloomberg, Kanye West, and other politicians and celebrities began behaving strangely. More or less simultaneously, they advised their followers—around two hundred and fifty million people, in total—to send Bitcoin contributions to mysterious addresses. Twitter’s engineers were surprised and baffled; there was no indication that the company’s network had been breached, and yet the tweets were clearly unauthorized. They had no choice but to switch off around a hundred and fifty thousand verified accounts, held by notable people and institutions, until the problem could be identified and fixed. Many government agencies have come to rely on Twitter for public-service messages; among the disabled accounts was the National Weather Service, which found that it couldn’t send tweets to warn of a tornado in central Illinois. A few days later, a seventeen-year-old hacker from Florida, who enjoyed breaking into social-media accounts for fun and occasional profit, was arrested as the mastermind of the hack. The F.B.I. is currently investigating his sixteen-year-old sidekick.
In its narrowest sense, this immense security breach, orchestrated by teen-agers, underscores the vulnerability of Twitter and other social-media platforms. More broadly, it’s a telling sign of the times. We’ve entered a world in which our national well-being depends not just on the government but also on the private companies through which we lead our digital lives. It’s easy to imagine what big-time criminals, foreign adversaries, or power-grabbing politicians could have done with the access the teen-agers secured. In 2013, the stock market briefly plunged after a tweet sent from the hacked account of the Associated Press reported that President Barack Obama had been injured in an explosion at the White House; earlier this year, hundreds of armed, self-proclaimed militiamen converged on Gettysburg, Pennsylvania, after a single Facebook page promoted the fake story that Antifa protesters planned to burn American flags there.
A group called the Syrian Electronic Army claimed responsibility for the A.P. hack; the Gettysburg hoax was perpetrated by a left-wing prankster. A more determined and capable adversary could think bigger. In the run-up to this year’s Presidential election, e-mails and videos that most analysts attributed to the Iranian government were sent to voters in Arizona, Florida, and Alaska, purporting to be from the Proud Boys , a neo-Fascist, pro-Trump organization: “Vote for Trump,” they warned, “or we will come after you.” Calls to voters in swing states warned them against voting and text messages pushed a fake video about Joe Biden supporting sex changes for second graders. But a truly ambitious disinformation attack would be cleverly timed and coördinated across multiple platforms. If what appeared to be a governor’s Twitter account reported that thousands of ballots had gone missing on Election Day , and the same message were echoed by multiple Facebook posts—some written by fake users or media outlets, others by real users who had been deceived—many people might assume the story to be true and forward it on. The goal of false information need not be an actual change in events; chaos is often the goal, and sowing doubt about election results is a perfect way to achieve it.
When we think of national security, we imagine concrete threats—Iranian gunboats, say, or North Korean missiles. We spend a lot of money preparing to meet those kinds of dangers. And yet it’s online disinformation that, right now, poses an ongoing threat to our country; it’s already damaging our political system and undermining our public health. For the most part, we stand defenseless. We worry that regulating the flow of online information might violate the principle of free speech. Because foreign disinformation played a role in the election of our current President, it has become a partisan issue, and so our politicians are paralyzed. We enjoy the products made by the tech companies, and so are reluctant to regulate their industry; we’re also uncertain whether there’s anything we can do about the problem—maybe the price of being online is fake news. The result is a peculiar mixture of apprehension and inaction. We live with the constant threat of disinformation and foreign meddling. In the uneasy days after a divisive Presidential election, we feel electricity in the air and wait for lightning to strike.
In recent years, we’ve learned a lot about what makes a disinformation campaign effective. Disinformation works best when it’s consistent with an audience’s preconceptions; a fake story that’s dismissed as incredible by one person can appear quite plausible to another who’s predisposed to believe in it. It’s for this reason that, while foreign governments may be capable of more concerted campaigns, American disinformers are especially dangerous: they have their fingers on the pulse of our social and political divisions. At the moment, disinformation seems to be finding a more receptive audience on the political right. Perhaps, as some researchers have suggested, an outlook rooted in aggrievement and a distrust of institutions makes it easier to believe in wrongdoing by élites. Breitbart columnists and some Fox News commentators are also happy to corroborate and amplify fringe ideas. In any event, during this year’s Presidential election, our social-media platforms have been awash in corrosive disinformation, much of it generated by Americans, ranging from lurid conspiracy-mongering—Antifa protesters starting wildfires in Oregon; Democrats arranging child-sex rings—to the faux-legalistic questioning of voting procedures.
For the most part, this disinformation has been scattershot. What would a more organized effort look like? The cyber-disinformation campaign conducted by Russia in 2016, largely on Facebook, gave us a glimpse of what’s possible. The five-volume bipartisan Senate report on Russia’s efforts, produced by the Select Committee on Intelligence, reveals an effort of startling scale. Russia conducts disinformation operations at home, in bordering countries, and across the world. It works through several arms at once: the sophisticated, Kremlin-directed S.V.R. (the equivalent of the C.I.A.); the clumsier, military-run G.R.U.; and the savvier Internet Research Agency in St. Petersburg. In general, Russia seeks to push disinformation in a comprehensive, integrated way, so as to give its content an aura of authenticity. Using so-called sockpuppets—inauthentic personas on Facebook and elsewhere—its campaigns inflame existing political tensions with calls to action, online petitions, forged evidence, and false news. This specious material is then cited by seemingly legitimate news sites established by Russia for the purpose of spreading and corroborating disinformation. Facebook and Twitter have built automated systems that look for inauthentic accounts with manufactured followings. But Russian cyber actors have become increasingly sophisticated, using an integrated array of what spy agencies call T.T.P.s—tactics, techniques, and procedures—to avoid detection.
Like a musical toured in smaller markets before it hits Broadway, Russian T.T.P.s are tested first in border states—Lithuania, Estonia, Ukraine, Poland—before being deployed against America. In the past year, Russian trolls working in those countries have adopted a new strategy: impersonating actual organizations or people, or claiming to be affiliated with them—a muddying of the waters that makes detection harder. According to experts , they’ve also begun corrupting legitimate Eastern European news sites: hackers manipulate real content, sometimes laying the groundwork for future disinformation, at others, inserting fake articles for immediate dissemination.
China , meanwhile, already adept at intellectual-property cyber theft, has begun shifting toward active disinformation of the Russian sort. Most of its efforts are focussed on propaganda portraying China as a peace-loving nation with a superior form of government. But earlier this year, a pro-China operation, nicknamed Spamouflage Dragon by cybersecurity firms, deployed an array of Facebook, YouTube, and Twitter accounts with profile pictures generated by artificial intelligence to attack President Trump and spread falsehoods about the George Floyd killing, the Black Lives Matter movement, and Hong Kong’s pro-democracy protests. Compared to Russia, China’s disinformation efforts are less immediately alarming, because its government is more concerned about how it’s perceived around the world. But it seems possible that, in the longer term, the country will pose a more significant threat. If China harnessed the vast intelligence resources of its Ministry of State Security and its People’s Liberation Army to mount a coördinated disinformation campaign against the United States, its reach could be significant. Foreign powers could get better at pushing our buttons; domestic disinformers could get better-organized. In either case, we could face a more acute version of the disinformation crisis we’re struggling with now.
There’s a sense in which it doesn’t matter who our disinformers are, since they all use the same social-media technology, which has transformed our societies quickly and pervasively, outpacing our ability to anticipate its risks. We’ve taken a relatively minimal and reactive approach to regulating our new digital world. The result is that we lag behind in security: the malicious use of new platforms begins before security experts, in industry or government, can weigh in. Because new vulnerabilities are revealed individually, we tend to perceive them as one-offs—a hack here, a hack there.
As cyber wrongdoing has piled up, however, it has shifted the balance of responsibility between government and the private sector. The federal government used to be solely responsible for what the Constitution calls our “common defense.” Yet as private companies amass more data about us, and serve increasingly as the main forum for civic and business life, their weaknesses become more consequential. Even in the heyday of General Motors, a mishap at that company was unlikely to affect our national well-being. Today, a hack at Google, Facebook, Microsoft, Visa, or any of a number of tech companies could derail everyday life, or even compromise public safety, in fundamental ways.
Because of the very structure of the Internet, no Western nation has yet found a way to stop, or even deter, malicious foreign cyber activity. It’s almost always impossible to know quickly and with certainty if a foreign government is behind a disinformation campaign, ransomware implant, or data theft; with attribution uncertain, the government’s hands are tied. China and other authoritarian governments have solved this problem by monitoring every online user and blocking content they dislike; that approach is unthinkable here. In fact, any regulation meant to thwart online disinformation risks seeming like a step down the road to authoritarianism or a threat to freedom of speech. For good reason, we don’t like the idea of anyone in the private sector controlling what we read, see, and hear. But allowing companies to profit from manipulating what we view online, without regard for its truthfulness or the consequences of its viral dissemination, is also problematic. It seems as though we are hemmed in on all sides, by our enemies, our technologies, our principles, and the law—that we have no choice but to learn to live with disinformation, and with the slow erosion of our public life.
We might have more maneuvering room than we think. The very fact that the disinformation crisis has so many elements—legal, technological, and social—means that we have multiple tools with which to address it. We can tackle the problem in parts, and make progress. An improvement here, an improvement there. We can’t cure this chronic disease, but we can manage it.
On the legal side, there are common-sense steps we could take without impinging on our freedom of speech. Congress could pass laws to curtail disinformation in political campaigns, not necessarily by outlawing false statements—which would run afoul of the First Amendment —but by requiring more disclosure, and by making certain knowing falsehoods illegal, including wrongful information about polling places. Today, political ads that appear online aren’t subject to the same disclosure and approval rules that apply to ads on radio and television; that anachronism could be corrected. Lawmakers could explore prohibiting online political ads that micro-target voters based on race, age, political affiliation, or other demographic categories; that sort of targeting allows divisive ads and disinformation to be aimed straight at amenable audiences, and to skirt broader public scrutiny. Criminal laws could also be tightened to outlaw, at least to some extent, the intentional and knowing spread of misinformation about elections and political candidates.
Online, the regulation of speech is governed by Section 230 of the Communications Decency Act—a law, enacted in 1996, that was designed to allow the nascent Internet to flourish without legal entanglements. The statute gives every Internet provider or user a shield against liability for the posting or transmission of user-generated wrongful content. As Anna Wiener wrote earlier this year, Section 230 was well-intentioned at the time of its adoption, when all Internet companies were underdogs. But today that is no longer true, and analysts and politicians on both the right and the left are beginning to think, for different reasons, that the law could be usefully amended. Republicans tend to believe that the statute allows liberal social media companies to squelch conservative voices with impunity; Democrats argue that freewheeling social media platforms, which make money off virality, are doing too little to curtail online hate speech. Amending Section 230 to impose some liability on social-media platforms, in a manner that neither cripples them nor allows them to remain unaccountable, is a necessary step in curbing disinformation. It seems plausible that the next Congress will amend the statute.
Other legal steps might flow from the recognition that the very ubiquity of social-media companies has created vulnerabilities for the millions of Americans who rely on them. Antitrust arguments to break up platforms and companies are one way to address this aspect of the problem. The Senate has asked the C.E.O.s of Facebook and Twitter to appear at a hearing on November 17th, intended to examine the platforms’ “handling of the 2020 election.” Last month, a House hearing on the same topic degenerated into an argument between Republicans, who claimed that social media was censoring the President, and Democrats, who argued that the hearing was a campaign gimmick. It remains to be seen whether Congress can separate politics from substance and seriously consider reform proposals, like the one put forth recently by the New York State Department of Financial Services, which would designate social-media platforms as “systemically important” and subject to oversight. It will be difficult to regulate such complicated and dynamic technology. Still, the broader trend is inescapable: the private sector must bear an ever-increasing legal responsibility for our digital lives.
Technological progress is possible, too, and there are signs that, after years of resistance, social-media platforms are finally taking meaningful action. In recent months, Facebook, Twitter, and other platforms have become more aggressive about removing accounts that appear inauthentic, or that promote violence or lawbreaking; they have also moved faster to block accounts that spread disinformation about the coronavirus or voting, or that advance abhorrent political views, such as Holocaust denial. The next logical step is to decrease the power of virality. In 2019, after a series of lynchings in India was organized through the chat program WhatsApp, Facebook limited the mass forwarding of texts on that platform; a couple of months ago, it implemented similar changes in the Messenger app embedded in Facebook itself. As false reports of ballot fraud became increasingly elaborate in the days before and after Election Day, the major social media platforms did what would have been unthinkable a year ago, labelling as misleading messages from the President of the United States. Twitter made it slightly more difficult to forward tweets containing disinformation; an alert now warns the user about retweeting content that’s been flagged as untruthful. Additional changes of this kind, combined with more transparency about the algorithms they use to curate content, could make a meaningful difference in how disinformation spreads online. Congress is considering requiring such transparency.
Finally, there are steps we could take that have nothing to do with regulation or technology. Many national-security experts have argued for an international agreement that outlaws disinformation, and for coördinated moves by Western democracies to bring cybercriminals to justice. The President could choose to make combating foreign disinformation a national-security priority, by asking the intelligence community to focus on it in a cohesive way. (We have an integrated national counterterrorism center, but not one focused on disinformation.) Our national-security agencies could share more with the public about the T.T.P.s used by foreign disinformation campaigns. And the teaching of digital literacy—perhaps furthered by legislation that promotes civic education—could make it harder for disinformation, foreign or domestic, to take hold.
We will soon no longer have a President who himself creates a storm of falsehoods. But the electricity will remain in the air, regardless of who occupies the Oval Office. Perhaps because the disinformation crisis has descended upon us so suddenly, and because it reinforces our increasing political polarization, we’ve tended to regard it as inevitable and unavoidable—a fact of digital life. But we do have options, and if we come together to exercise them, we could make a meaningful difference. In this case, it might be possible to change the weather.
A previous version of this piece misstated the state where the Gettysburg rally took place.

Proofpoint closes acquisition of Tessian. Read More ->
- Why Tessian

- By Initiative
- Email Defense in Depth -->
- Stop Sensitive Data Loss -->
- By Platform
- Microsoft 365 -->
- By Threat Type
- Business Email Compromise -->
- Vendor Email Compromise -->
- Account Takeover -->
- Image and QR Code Attack -->
- Credential Theft -->
- Financial Fraud -->
- Misdirected Email -->
- Data Exfiltration -->
- Customer Stories -->
- Reviews -->
- By Industry
- Finance -->
- Healthcare -->
- Technology -->

- Webinars -->
- Product Updates -->
- Research & Reports -->
- Product Datasheets -->
- Case Studies -->

- About --> Learn more about Tessian's mission, values, and team
- Careers --> Learn more about Tessian's career opportunities
- Get a Platform Overview
- Email Defense in Depth
- Stop Sensitive Data Loss
- Microsoft 365
- Business Email Compromise
- Vendor Email Compromise
- Account Takeover
- Image and QR Code Attack
- Credential Theft
- Financial Fraud
- Misdirected Email
- Data Exfiltration
- Customer Stories
- Product Updates
- Research & Reports
- Product Datasheets
- Case Studies
15 Examples of Real Social Engineering Attacks

Register today for our free, virtual summit, Fwd: Thinking – Preparing for the next wave of email attacks.
Social engineering attacks are one of the main ways bad actors can scam companies. Here’s 15 of the biggest attacks, and how they happened.
Social engineering attacks are a type of cybercrime wherein the attacker fools the target through impersonation. They might pretend to be your boss, your supplier, someone from our IT team, or your delivery company. Regardless of who they’re impersonating, their motivation is always the same — extracting money or data.
1. $100 Million Google and Facebook Spear Phishing Scam
The biggest social engineering attack of all time (as far as we know) was perpetrated by Lithuanian national, Evaldas Rimasauskas, against two of the world’s biggest companies: Google and Facebook. Rimasauskas and his team set up a fake company, pretending to be a computer manufacturer that worked with Google and Facebook. Rimsauskas also set up bank accounts in the company’s name.
The scammers then sent phishing emails to specific Google and Facebook employees, invoicing them for goods and services that the manufacturer had genuinely provided — but directing them to deposit money into their fraudulent accounts. Between 2013 and 2015, Rimasauskas and his associates cheated the two tech giants out of over $100 million.
2. Persuasive email phishing attack imitates US Department of Labor
In January 2022, Bleeping Computer described a sophisticated phishing attack designed to steal Office 365 credentials in which the attackers imitated the US Department of Labor (DoL). The scam is a noteworthy example of how convincing phishing attempts are becoming.
The attack used two methods to impersonate the DoL’s email address—spoofing the actual DoL email domain (reply@dol[.]gov) and buying up look-a-like domains, including “dol-gov[.]com” and “dol-gov[.]us”. Using these domains, the phishing emails sailed through the target organizations’ security gateways.
The emails used official DoL branding and were professionally written and invited recipients to bid on a government project. The supposed bidding instructions were included in a three-page PDF with a “Bid Now” button embedded.
On clicking the link, targets were redirected to a phishing site that looked identical to the actual DoL site, hosted at a URL such as bid-dolgov[.]us. The fake bidding site instructed users to enter their Office 365 credentials. The site even displayed an “error” message after the first input, ensuring the target would enter their credentials twice and thus reducing the possibility of mistyped credentials.
It’s easy to see how even a relatively scrupulous employee could fall for an attack like this—but the problem would not have arisen if the target organization had better email security measures in place.
3. Russian hacking group targets Ukraine with spear phishing
As world leaders debate the best response to the increasingly tense situation between Russia and Ukraine, Microsoft warned in February 2022 of a new spear phishing campaign by a Russian hacking group targeting Ukrainian government agencies and NGOs.
The group—known as Gamaredon and tracked by Microsoft as ACTINIUM—has allegedly been targeting “organizations critical to emergency response and ensuring the security of Ukrainian territory” since 2021.
The initial phase of Gamaredon’s attack relies on spear phishing emails containing malware. The emails also contain a tracking pixel that informs the cybercriminals whether it has been opened.
The case is an important reminder of how cybersecurity plays an increasingly central role in international conflicts—and how all organizations should be taking steps to improve their security posture and protect against social engineering attacks.

4. Deepfake Attack on UK Energy Company
In March 2019, the CEO of a UK energy provider received a phone call from someone who sounded exactly like his boss. The call was so convincing that the CEO ended up transferring $243,000 to a “Hungarian supplier” — a bank account that actually belonged to a scammer.
This “cyber-assisted” attack might sound like something from a sci-fi movie, but, according to Nina Schick, Author of “ Deep Fakes and the Infocalypse: What You Urgently Need to Know ”, “This is not an emerging threat. This threat is here. Now.”
To learn more about how hackers use AI to mimic speech patterns, watch Nina’s discussion about deepfakes with Elvis Chan, Supervisory Special Agent at the FBI.

5. $60 Million CEO Fraud Lands CEO In Court
Chinese plane parts manufacturer FACC lost nearly $60 million in a so-called “ CEO fraud scam ” where scammers impersonated high-level executives and tricked employees into transferring funds. After the incident, FACC then spent more money trying to sue its CEO and finance chief, alleging that they had failed to implement adequate internal security controls.
While the case failed, it’s an important reminder: cybersecurity is business-critical and everyone’s responsibility. In fact, Gartner predicts that by 2024, CEOs could be personally liable for breaches.
6. Microsoft 365 phishing scam steals user credentials
In April 2021, security researchers discovered a Business Email Compromise ( BEC ) scam that tricks the recipient into installing malicious code on their device. Here’s how the attack works, and it’s actually pretty clever.
The target receives a blank email with a subject line about a “price revision.” The email contains an attachment that looks like an Excel spreadsheet file (.xlsx). However, the “spreadsheet” is actually a .html file in disguise.
Upon opening the (disguised) .html file, the target is directed to a website containing malicious code. The code triggers a pop-up notification, telling the user they’ve been logged out of Microsoft 365, and inviting them to re-enter their login credentials.
You can guess what happens next—the fraudulent web form sends the user’s credentials off to the cybercriminals running the scam.
This type of phishing—which relies on human error combined with weak defenses—has thrived during the pandemic. Phishing rates doubled in 2020, according to the latest FBI data.
7. Singapore bank phishing saga like ‘fighting a war’
Customers of the Oversea-Chinese Banking Corporation (OCBC) were hit by a string of phishing attacks and malicious transactions in 2021, leading to around $8.5 million of losses across approximately 470 customers.
The bank’s CEO Helen Wong described her company’s battle against the phishing attacks and subsequent fraudulent transfers as like “fighting a war.”
OCBC customers were duped into giving up their account details after receiving phishing emails in December 2021. The situation escalated quickly despite the bank shutting down fraudulent domains and alerting customers of the scam.
Wong described how, once the phishing campaign had taken hold, the fraudsters had set up “mule” accounts to receive stolen funds. No matter how quickly the bank’s security team managed to shut down a mule account, the scammers would soon find another to take its place.
The CEO described her dilemma after getting the phishing campaign under control: reimbursing customers felt like the right thing to do, but Wong feared it could incentivize further attacks. So far over 200 customers have been compensated.
8. Ransomware gang hijacks victim’s email account
In April 2021, several employees of U.K. rail operator Merseyrail received an unusual email from their boss’s email account with the subject line “Lockbit Ransomware Attack and Data Theft.” Journalists from several newspapers and tech sites were also copied in.
The email—sent by a fraudster impersonating Merseyrail’s director—revealed that the company had been hacked and had tried to downplay the incident. The email also included an image of a Merseyrail employee’s personal data.
It’s not clear how Merseyrail’s email system got compromised (although security experts suspect a spear phishing attack)—but the “double extortion” involved makes this attack particularly brutal.
The “Lockbit” gang not only exfiltrated Merseyrail’s personal data and demanded a ransom to release it—the scammers used their access to the company’s systems to launch an embarrassing publicity campaign on behalf of its director.

9. Phishing scam uses HTML tables to evade traditional email security
Criminals are always looking for new ways to evade email security software. One BEC attack, discovered in April 2021, involves a particularly devious way of sneaking through traditional email security software like Secure Email Gateways (SEGs) and rule-based Data Loss Prevention (DLP).
BEC attacks often rely on impersonating official emails from respected companies. This means embedding the company’s logos and branding into the email as image files.
Some “rule-based” email security software automatically treats image files as suspicious. If a phishing email contains a .png file of the Microsoft Windows logo, the email is more likely to be detected—but without that distinctive branding, the email won’t look like it came from Microsoft.
But once again, cyber criminals have found a way to exploit the rule-based security approach.
To imitate Microsoft’s branding, this attack uses a table instead of an image file—simply a four-square grid, colored to look like the Windows logo. The average employee is unlikely to closely inspect the logo and will automatically trust the contents of the email.
This isn’t the first time fraudsters have used tables to evade rule-based DLP software. For example, some email security filters are set up to detect certain words, like “bitcoin.” One way around this is to create a borderless table and split the word across the columns: “bi | tc | oin.”
10. Sacramento phishing attack exposes health information
Five employees at Sacramento County revealed their login credentials to cybercriminals after receiving phishing emails on June 22, 2021.
The attack was discovered five months later , after an internal audit of workers’ email inboxes.
The breach occurred after employees received phishing emails containing a link to a malicious website. The targets entered their usernames and passwords into a fake login page which were then harvested by cybercriminals.
The attack resulted in a data breach exposing 2,096 records of health information and 816 records of “personal identification information.” The county notified the victims by email and offered free credit monitoring and identity theft services.
It remains to be seen whether this proposed resolution by the county will be enough. Protection of health information is particularly tightly regulated in the US, under the Health Insurance Portability and Accountability Act (HIPAA), and data breaches involving health data have led to some hefty lawsuits in the past.

11. Google Drive collaboration scam
In late 2020, a novel but simple social engineering scam emerged that exploited Google Drive’s notification system.
The fraud begins with the creation of a document containing malicious links to a phishing site . The scammer then tags their target in a comment on the document, asking the person to collaborate.
Once tagged, the target receives a legitimate email notification from Google containing the comment’s text and a link to the relevant document.
If the scam works, the victim will view the document, read the comments, and feel flattered at they’re being asked to collaborate. Then, the victim will click one of the malicious links , visit the phishing site, and enter their login credentials or other personal data.
This scam is particularly clever because it exploits Google’s email notification system for added legitimacy. Such notifications come straight from Google and are unlikely to trigger a spam filter.
But like all social engineering attacks, the Google Drive collaboration scam plays on the victim’s emotions : in this case, the pride and generosity we might feel when called upon for help.
Want to see a screenshot of a similar attack? We breakdown a spear phishing attack in which the attacker impersonates Microsoft Teams. Check it out here .
12. Sharepoint phishing fraud targets home workers
April 2021 saw yet another phishing attack emerge that appears specifically designed to target remote workers using cloud-based software.
The attack begins when the target receives an email—written in the urgent tone favored by phishing scammers—requesting their signature on a document hosted in Microsoft Sharepoint.
The email looks legitimate. It includes the Sharepoint logo and branding familiar to many office workers. But the link leads to a phishing site designed to siphon off users’ credentials.
Phishing attacks increasingly aim to exploit remote collaboration software— Microsoft research suggests nearly half of IT professionals cited the need for new collaboration tools as a major security vulnerability during the shift to working from home.

13. $75 Million Belgian Bank Whaling Attack
Perhaps the most successful social engineering attack of all time was conducted against Belgian bank, Crelan . While Crelan discovered its CEO had been “whaled” after conducting a routine internal audit, the perpetrators got away with $75 million and have never been brought to justice.
Crelan fell victim to “ whaling ” — a type of spear-phishing where the scammers target high-level executives. Cybercriminals frequently try to harpoon these big targets because they have easy access to funds.
14. High-Profile Twitters Users’ Accounts Compromised After Vishing Scam
In July 2020, Twitter lost control of 130 Twitter accounts , including those of some of the world’s most famous people — Barack Obama, Joe Biden, and Kanye West.
The hackers downloaded some users’ Twitter data, accessed DMs, and made Tweets requesting donations to a Bitcoin wallet. Within minutes — before Twitter could remove the tweets — the perpetrator had earned around $110,000 in Bitcoin across more than 320 transactions.
Twitter has described the incident as a “phone spear phishing” attack (also known as a “ vishing ” attack). The calls’ details remain unclear, but somehow Twitter employees were tricked into revealing account credentials that allowed access to the compromised accounts.
Following the hack, the FBI launched an investigation into Twitter’s security procedures. The scandal saw Twitter’s share price plummet by 7% in pre-market trading the following day.
15. Texas Attorney-General Warns of Delivery Company Smishing Scam
Nearly everyone gets the occasional text message that looks like it could be a potential scam. But in September 2020, one smishing (SMS phishing) attack became so widespread that the Texas Attorney-General put out a press release warning residents about it.
Victims of this scam received a fraudulent text message purporting to be from a delivery company such as DHL, UPS, or FedEx. The SMS invited the target to click a link and “claim ownership” of an undelivered package. After following the link, the target was asked to provide personal information and credit card details.
The Texas Attorney-General warned all Texans not to follow the link. He stated that delivery companies do not communicate with customers in this way, and urged anyone receiving the text message to report it to the Office of the Attorney General or the Federal Trade Commission.
Top tip: Never to respond to any suspicious message, click links within SMS messages, or reveal personal or company information via SMS.
Prevent social engineering attacks in your organization
There’s one common thread through all of these attacks: they’re really, really hard to spot. That’s where Tessian comes in. Tessian is i ntelligent cloud email security that stops threats and builds smart security cultures in the modern enterprise.
Powered by machine learning , Tessian analyzes and learns from an organization’s current and historical email data and protects employees against inbound email security threats, including whaling, CEO Fraud, BEC, spear phishing, and other targeted social engineering attacks.
To learn more about how Tessian can protect your people and data against social engineering attacks on email, book a demo today . Or, if you’d rather just stay up-to-date with the latest social engineering attacks, subscribe to our weekly blog digest. You’ll get news, threat intel, and insights from security leaders for security leaders straight to your inbox.
Related Posts

Attackers are Using Microsoft Forms to Exfiltrate Data

Why Financial Services Firms are Most Likely to Fall for Phishing Attacks

Phishing 101: What is Phishing?

Hacker’s Advice: 7 Tips for Avoiding Phishing Scams
- Social Integrity
- Submit Content
- Social Media Account Request
- Sprout Social
- x (twitter)

- © 2024 The Regents of the University of Michigan
U-M Social Media
- X (Twitter)
Hacked: A Case Study

There’s no denying it: we got hacked. Here’s what we learned and what you can learn, too.
On Wednesday, August 12, at approximately 3:30am, a barrage of malicious postings found their way to three of the University of Michigan’s most popular Facebook pages: Michigan Football, Michigan Basketball, and Michigan Athletics. Our Department of Information Technology Services (ITS) was first alerted to the inappropriate content by our user community. Community members across many of our other social properties also reached out with comments and direct messages. By 5am ITS in turn had notified the University Director of Social Media, the Office of Public Affairs and Internal Communications, and the Department of Public Safety and Security. Likewise, members of Michigan Athletics’ external communications staff awoke to a multitude of notifications, voicemails, and text messages. By 6am the story of our hacking and a full array of screenshots were being discussed across the airwaves and on online news outlets.

After quickly establishing that this was not the work of a disgruntled employee, and confirming that we had lost all administrative access to the accounts, we began furiously flagging content, pages, and any Facebook organizational contacts we could find. As the owners of the sixth-largest higher-ed Facebook audience in the nation and the largest pages in collegiate athletics for football and basketball, one might think we have Facebook on speed-dial; however, that was not the case. Further complicating the situation was the fact that many of the contacts we did have were in a variety of time zones, and many were still sleeping. In the end, it was actually Facebook’s London (UK) team that came to our rescue, thanks to a connection made through a former agency peer who then reached out to a Facebook client partner at one of Michigan’s robust auto industry social teams.

Simultaneously, the University of Michigan social leadership team was alerted by UMSocial to implement password changes on all official accounts and immediately assess any and all third-party applications that had been granted access to publish on the pages behalf. This team comprises one representative from each primary unit across the U-M’s three campuses. Each individual is tasked with regular communication with UMSocial, as well as with communicating best practices, strategy, and other pertinent information to all administrators of subsidiary social media accounts within their areas. Michigan Athletics’ associate athletic director for external communications and public relations also initiated a group distribution text message with key stakeholders and leadership throughout the university to keep them apprised of the developing situation.
At 7:42am, in collaboration with Public Affairs and Michigan Athletics, UMSocial issued the first acknowledgment of the hacking situation on the overarching University of Michigan social properties. Ensuring that our vast social communities were aware we were working diligently to rectify the situation in a timely manner was of utmost importance to us, and clear, transparent communications proved to be a valuable tool as the events of the day unfolded. The multi-phased communications approach included internal and external audiences and media relations while utilizing broad-based education about the day’s events and how it impacted various groups.

At 8:38am Facebook took control of and unpublished the three compromised pages. Within 15 minutes, university page administrators had been re-credentialed and the process of cleaning the accounts began. By 10am the pages had gone live once again and we notified our audiences and key stakeholders that the situation had been contained…or so we thought.

Just after the noon hour, a second wave of attacks was triggered on the previously affected pages as a result of our efforts to alter delegated privileges on the remaining page administrators. It was at this point that we were able to determine the actions were linked to a specific employee’s personal account, and we relayed information to ITS and Facebook which allowed us to determine the original source of the security breach. Following an extensive investigation, Facebook determined that the hack was part of a sophisticated phishing scheme found within Facebook Messenger that has affected many other brands.

According to Facebook, the following two scripted messages reflect what the individual may have received:
Dear Nikki Sunstrum,
Data that you have filled do not match your fanpage, precisely the Security Question, and Answer do not match in your records.
Please fill the application again.
[Malicious link was here]
Facebook Support Center
Data that you have filled do not match your fanpage please fill the application again
Upon clicking the links, users are directed to a form that looks like a page to validate Facebook credentials, but in fact is not an authorized Facebook site. Facebook provided the following tips for further future protection, which we have implemented as a standard of best practice and instructed all University of Michigan social properties to adopt as part of our use guidelines.
- Facebook will never send official communication via Messenger.
- Never enter your password anywhere but facebook.com . Scammers often set up fake pages to look like a FB login page so it’s important to always check that you’re really logging into www.facebook.com .
- Watch out for fake pages/apps as well as “official” links using URL shorteners such as the gl links from the phishing messages.
- Try to keep the number of admins to a minimum
- Ensure that Admin and Editor roles have login approvals turned on. This will add an additional layer of security when someone attempts to login from an unrecognized device.
Before the close of business August 12, we had debrief and exploratory third-party application meetings on the books. Normal operations on social accounts were intentionally eased back into and prolonged until individual responses were issued to every single message Michigan Athletics had received. The next day we gathered to discuss what went well, and provided summary information on the status of all accounts to leadership. We also monitored and measured the reach and impact of the conversation repeatedly as it unfolded. Overall, our brand pages saw a nominal increase in followers, while our individual sport pages experienced a very minimal decrease. When compared to other topics surrounding the University of Michigan brand over the last seven days, the hack ranked fifth out of 10.

For us, the moral of the story was clear. Password security isn’t enough – even the most well-trained social media professionals are still subject to human error. The best we can do is take every necessary precaution to incorporate additional levels of security. Collectively, we have initiated the implementation of two-step authentication procedures, and are continuing to evaluate third-party security applications. Lastly, at Facebook’s recommendation, we are also researching Facebook Business Manager.
It is our hope that, by highlighting the steps taken and lessons learned, we might prevent future attacks and educate our peer institutions on how to safeguard themselves as well.
If you have experienced a similar event and are interested in sharing your case study, please feel free to contact us at umsocial@umich.edu . Additionally if you have questions please reach out to me on Twitter @NikkiSunstrum.
#StaySocial, #StayConnected, #StaySafe
Written by @NikkiSunstrum, University of Michigan Director of Social Media

- Contact | Submit Content
Office of the Vice President for Communications

Partner Overview
Join Us for Growth, Innovation and Cybersecurity Excellence.
Become a Channel Partner
Be a Valued Partner and Embark on a Journey of Profitability.
Partner Portal
Unified Security Platform
Latest Content and Resources
Threat Report 2023
NRGi Holding Case Study
The 15 Internet Crime Stories That Make Cybersecurity Measures Essential
Read the best, most fascinating tech stories that cover the risks of the digital landscape and find out how to stay safe
Last updated on February 28, 2024

Internet crime stories are dime a dozen but these examples will show you why online security is essential. From ethical hacking to blackmail and car hijacking, these true stories show how you must act now to secure your well-being in the digital landscape. We carefully curated the best, most fascinating tech stories that cover the risks involved in any digital activity of device, so use the links below to navigate them.
- The mom whose laptop was locked down by a ransomware attack
- Tom was blackmailed because of his hacked Ashley Madison account
- How ethical hackers took over her PC
- They remote hacked his car
- Ransomware deletes 2 years of academic papers
- His WoW account got hacked. Twice
- Your data has been breached
- Catfish isn’t dinner, it’s lies, manipulation, and theft
- Hillary Clinton’s Aides Got Phished And Lost Her The Election
- He fell prey to the same scam twice and lost $1,350
- Who would want to be you? Some can even become You.
- When your workplace, a gaming giant, gets hit
- The casual, public Wi-Fi hack
- Customer support falls prey to a social engineering hack
- Hotel managers and clients had nightmares due to one lock hack posted
Cyber security incidents and getting hacked seem like distant, fascinating things where other people get hurt, but you stay safe. Truth is, getting hacked or scammed can happen to anyone and it might even have happened to you in the past.
The average number of devices used by you and most people have increased exponentially in the recent years. We’re surrounded by IoT devices, wear smart bracelets, have friends who are betting their savings on cryptocurrency, and we sign up to dozens of social media platforms.
This means cyber attacks have a lot of ways to get to you – either by targeting you specifically or by simply compromising your info in large-scale attacks. The best way to learn is through experience, so let’s do just that.
Here are the real stories of people who got hacked and what they learned, plus some actionable tips to enhance your security.
1. The mom whose laptop was locked down by a ransomware attack
Two days before Thanksgiving, Alina’s mother got hit by a ransomware attack. 5,726 files got locked by CryptoWall , an encryption malware so powerful it is almost impossible to recover the information.
Alina’s mom contacted the attacker through the ransomware’s communication feature.
As all ransomware creators, he told her she can either pay to get her files back or lose them forever.
The price to unlock her files was 500$ in the first week and 1000$ in the second one, after which the files would be deleted.
Payment was to be done in Bitcoin, a complicated process which she had to learn on the fly.
Because of a major snowstorm that closed down the banks, Alina’s mom couldn’t pay the ransom in the first week, and ended up having to plead with her attacker to not increase the price to 1,000$.
Surprisingly, he accepted and gave her the key to unlock her files. However, no one should ever pay a ransom, the risks far outweigh the benefits.
T he full story is here: How my mom got hacked & What I’ve learned after my mom got hacked (and her data held for ransom)
Find out what steps to take for your protection: WHAT IS RANSOMWARE AND 9 EASY STEPS TO KEEP YOUR SYSTEM PROTECTED
2. tom was blackmailed because of his hacked ashley madison account.

After the Ashley Madison hack, cyber criminals contacted him and demanded 500$ to remove his name from a publicly searchable registry.
If not, they would also send an email to his family, informing them of Tom’s affair. Tom refused, believing that if he paid them, they would know that he had something to lose and could be blackmailed further.
He was wise, but that didn’t mean he didn’t suffer. In the end, Tom had to live knowing his affairs on AM could be exposed at any time by the hackers.
Moreover, there were also people who took it up upon themselves to impart justice on people in circumstances they couldn’t, or wouldn’t, understand.
The story: In Ashley Madison’s wake, here’s one man’s story of sex, sorrow and extortion
Securing your pc doesn’t have to be expensive: 13 free pc security hacks to build your online protection, 3. how ethical hackers took over her pc.
Sophie is a technology reporter at the Daily Telegraph.
As part of an assignment, she accepted to be part of an ethical hacking experiment. Basically, a group of ethical hackers would try to compromise her system without her knowing how, when and where.

They pretended to be whistleblowers in control of sensitive government information and sent her an email with some of the files attached.
The malware infection occurred the moment she opened the file, and the attackers got access to everything, including email address and web cam. And it wasn’t even that difficult to do.
The story: How hackers took over my computer
This is how you can protect your email address: the complete guide to email security, 4. they remote hacked his car.
Andy Greenberg, a senior writer at Wired, once took part in a groundbreaking experiment which tested how car hacking could be done.

Next, the transmission was cut and finally, they remotely activated the breaks. And they did all of these things with Andy behind the wheel.
The experiment uncovered a massive flaw in Jeep’s cars which was later fixed. Today, this is even easier to achieve, due to the rise of electric cars and the huge push towards autonomous vehicles like trucks, taxis and more.
The story: Hackers Remotely Kill a Jeep on the Highway—With Me in It
Learn more about how software can expose you, something that works the same way whether we’re talking about computers or self-driving cars: 8 vulnerable software apps exposing your computer to cyber attacks, 5. ransomware deletes 2 years of academic papers.
What’s the first thing people do when they get hit by a malware attack? They panic and ask for help in a dedicated forum: “My PC is infected.
Please, can anyone help me? ”
For this user however, it was too little, too late. For 2 years he worked on his academic papers, and then they got encrypted by ransomware.
The timing was awful as well: it happened right before they were due. Antivirus didn’t help and he had no backup.
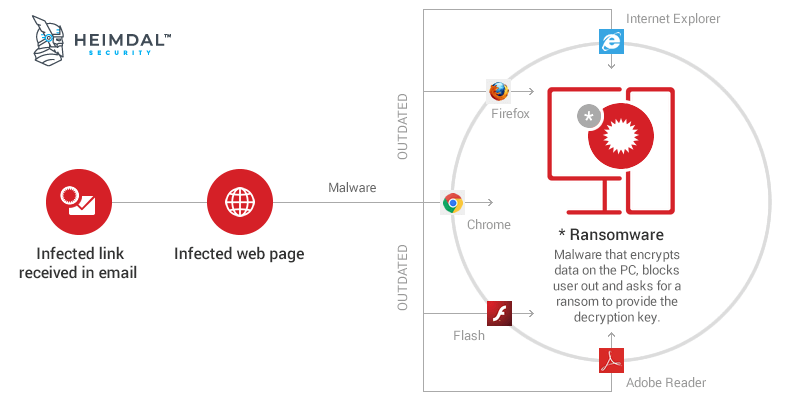
We hope he didn’t pay.
What we do know is that ransomware attacks are much more frequent that you can imagine and they target individuals and businesses alike.
The story: My PC got hacked by troldesh ransomware. please is there anyone who can help.
Find out how to backup your data so ransomware does not affect you: how to backup your computer – the best advice in one place, 6. his wow account got hacked. twice.
Gamers are favorite targets for cyber criminals, since they don’t want to lose the time and money invested in a character and are willing to pay the ransom.
As a result of a potential phishing attempt, this guy had his WoW account hacked and all his progress lost. And it happened to him not once, but twice!

The same type of attack happens in most popular online games.
League of Legends phishing volumes are truly legendary, so we talked to their security team to find out how to avoid getting your account stolen.
The story: So my WoW account got hacked… twice.
Learn more about security and gaming: gamers, time to take your cyber security to the next level, 7. your data has been breached.
The Office of Personnel Management, OPM for short, can be considered the US Government’s HR Department.
Among other things, it keeps records of employee personal information, such as height, weight, hair and eye color.
In 2014, the OPM got hacked, and the information of 22 million government employees leaked, most likely in the hands of a foreign government.

143 million US consumers had their sensitive personal information exposed. That’s 44% of the population and today we’re still seeing reports of more Equifax leaks.
Odds are, if you’re a US citizen, your info is floating around on the dark web , at the mercy of cyber criminals. What do you think the US government did to deal with the Equifax hack?
After less than one month since the incident, the IRS awarded Equifax a contract for fraud detection. Clearly, it’s up to you and you alone to protect your identity.
The story: OPM got hacked and all I got was this stupid e-mail
Learn how to stay as safe as possible from identity theft: how to prevent identity theft in 20 essential steps, 8. catfish isn’t dinner, it’s lies, manipulation and theft.
Some people hack you not with malware or suspicious links, but by gaining your trust and love.
This journalist’s mother started using the online dating site Match.com, and eventually formed a connection with a soldier on active duty in Afghanistan.
After a while, the soldier asked for a 30,000$ loan to help him clear a sizeable inheritance of gold and jewelry from US customs.
By now, the journalist and her brother intervened, suspecting the soldier was catfishing their mother.

In the Match.com case, the victims confronted the man with their suspicions and other evidence they had accumulated over time.
The supposed soldier revealed he was a man from Ghana trying to support his sisters, and scamming people online was the best way he knew how to do that.
The story: My mom fell for a scam artist on Match.com—and lived to tell the tale
Learn about the top online scams and how to avoid them: top 11 scams used by online criminals to trick you, 9. hillary clinton’s aides got phished and lost her the election.
Unless you’ve been living under a rock, you definitely know why Hillary Clinton lost the US Election to Donald Trump.

When forwarding the phishing email to a computer technician, he wrote “This is a legitimate email” instead of “illegitimate”. This gave hackers from Russia access to about 60,000 emails from Podesta’s private Gmail account.
They stole all that data, gave it to Wikileaks, and the rest is actual history.
“The FBI’s laid-back approach meant that Russian hackers were able to roam inside the DNC’s computer systems for almost seven months before Democratic officials finally realised the gravity of the attack and brought in external cybersecurity experts.”
But it was too late, as the election results have shown.
The story: Top Democrat’s emails hacked by Russia after aide made typo, investigation finds
Learn why phishing is so effective and how you can avoid it: 15 steps to maximize your financial data protection, 10. he fell prey to the same scam twice and lost $1,350.
In 2007, Justin was at a difficult point in his life.
Unemployed, with a weak skill set and verging on alcoholism, Justin decided to turn his life around by moving to Italy.
Determined to find a cheap flight, Justin searched for sellers of frequent flyer miles.
He found two sellers and talked to them over the phone. One of them even sent him a photo of his driver’s license. In a twisted sequence of events, both of them scammed him for a total sum of 1350$.
Sounds unlikely?
Think again. Justin tried to find a cheap shortcut and get that ‘too good to be true’ deal and became blind to any potential scammers.
Plus, the phone conversations and photos helped dispel any suspicions he might have. This is how most scamming attempts succeed, by preying on people who give in to the fear of missing out.
The story: How I Lost $1,350 by Falling for the Same Internet Scam Twice in One Week
Learn more about how social scams work and how to avoid them: social scams – the full breakdown and protection plan, 11. who would want to be you some can even become you..
One day, Laura received a call from her credit card company, saying someone else had tried to obtain a credit card using her name, address and social security number.

Eventually, she guessed the answers and saw the extent of the damage.
The impersonator had created more than 50 accounts in Laura’s name, and got credit for utilities such as heat, cable, electricity and even a newspaper subscription.
What’s more, the companies went after Laura in order to get their money back.
After notifying the police and tracking down the impersonator, Laura got a court order and managed to fix a lot of the damage, but only after a lot of sweat and stress.
While her case was a fortunate one, few people share her luck and this story should act as a reminder to always safeguard your personal information.
Another stolen identity case created a buzz on Reddit . This user had an argument with an old roommate, who then decided to take revenge.
He created social media accounts using the victim’s name, photoshopping the person with an ISIS flag and posting questionable content The story: ‘Someone had taken over my life’
While a scary and multifaceted attack, it is possible to protect yourself against these types of threats. Here are 20 SECURITY STEPS YOU SHOULD TAKE TO PREVENT IDENTITY THEFT.
12. when your workplace, a gaming giant, gets hit.
In late 2014, one of the biggest and most expensive hacks ever recorded took place at Sony and one employee reveals the inside situation.

Half of the companies 6800 computers and servers were rendered dead and had ALL of their information stolen and deleted.
As a result, employees had to rewrite every single deleted file by hand. Paper became the main form of communication, used in written memos and to-do-lists, even their salaries were paid using hand-written checks.
The damage didn’t stop there.
The hackers got a hold of employee personal information. The source of the article had to change all her credit card passwords, Facebook, Amazon and eBay accounts, almost 30 accounts in total.
The story: I work at Sony Pictures. This is what it was like after we got hacked.
Because of their size and income, companies are frequent targets for hackers. here is a list of 10 critical corporate cybersecurity risks, 13. the casual, public wi-fi hack.
Maurits Martijn, a Dutch journalist at De Correspondent, entered a busy Amsterdam café with Wouter Slotboom, an ethical hacker.
Within a few minutes, Slotboom had set up his gear, consisting of a laptop and a small black device and connected to the coffeehouses Wi-Fi.

All you needed was around $80-90 worth of software and equipment, an average intelligence and that was it, a few minutes was all it took to get a hold of a few dozen users personal information.
Slotboom’s small, black device could fool a phone into connecting to his own Wi-Fi network, giving him control over the entire traffic coming and going from a device.
If Slotboom wanted to, he could wait until one user wrote in his email address and password and then take it over.
With it, he could control most of the services registered on that email.
While you don’t need to be paranoid every time you connect to a public Wi-Fi, it’s best if you know the risks of doing so.
The story: Don’t use public Wi-Fi when reading this article.
There are ways in which you can stay safe on public hotspots: 11 security steps to stay safe on public wi-fi networks, 14. customer support falls prey to a social engineering hack.
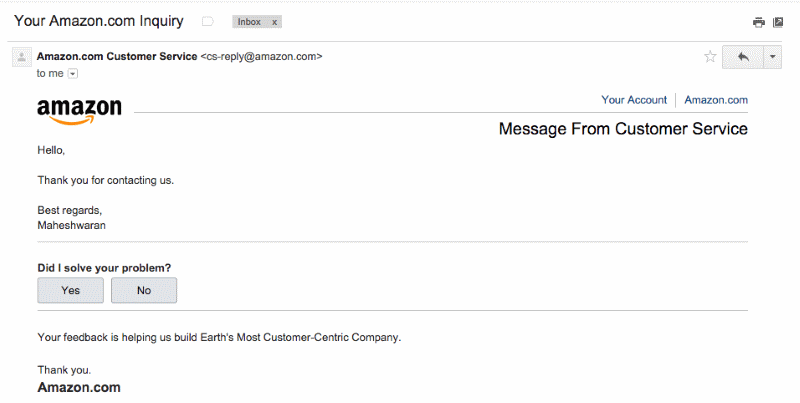
The impersonator then used Eric’s fake information in a conversation with an Amazon customer support representative and found out his real address and phone number.
Using Eric’s real information, the impersonator got in touch with various services and even managed to issue a new credit card in Eric’s name.
Eric got wind of his impersonator’s efforts by reading the customer support transcripts, and also found out his real purpose: to get the last 4 digits of his credit card.
Amazon didn’t do anything to protect Eric’s account, even though he repeatedly signaled the problem, so he finally decides to switch from Amazon to Google.
As a parting note, he gets an email from Amazon implying they have provided the impersonator with the last 4 digits of his credit card.
This story about this guy’s tumultuous experience with Amazon will make you think twice about storing confidential information in your online accounts.
The fact that Amazon failed to protect his account and look into the matter shows how a lack of cyber security education can endanger users
The story: Amazon’s customer service backdoor
Here is a guide on how to protect yourself against social engineering attacks, 15. hotel managers and clients had nightmares due to one lock hack.
In this Forbes story , reporters chronicles the chaos experienced by hotel managers and the panic felt by their customers after a burglar used online hacking tools to bypass the electronic locks on the doors.

He then used that Onity-lock hack to do a series of break-ins. How did this cautionary tale end?
On a bittersweet note.
The original burglar is serving a prison sentence, but the electronic locks in question can still be easily hacked.
A Wired reporter tried it himself, almost 6 years after the original Onity hack, and it still worked. He managed to break into a hotel room.
His story is amazing and it follows the birth of the original hacking method, how the burglar got to it and what came out of the entire publicized event.
The story: The Hotel Room Hacker
If you rely on electronic locks and other IoT devices to secure your belongings, this guide will be very useful: IOT SECURITY – All You Need To Know And Apply
16. the moderna conundrum.
According to Reuters and other major publications , Moderna Inc, one of the three biotech companies developing an efficient COVID-19 vaccine, has come under attack in late July. US’s Justice Department and the FBI have accused two Chinese nationals in this case.
They have been charged with spying on the American biotech company and three other targets in a bid to slow down or effectively stop the development of the COVID-19 vaccine.
Source from inside the FBI has revealed that the two arrested Chinese citizens are part of a hacking group funded by the Chinese government.
The company has emerged unscathed from the incident. No data has left Moderna’s databanks and the network remains intact.
The story: China-backed hackers ‘targeted COVID-19 vaccine firm Moderna’
These stories may help you realize that not protecting your information and relying on other Internet users to be nice and play fair is not a viable strategy.
Cyber criminals don’t care about the consequences of their attacks.
They only want to reach their purpose, and sometimes that purpose may have nothing to do with you.
You could just be a collateral victim, but the aftermath would be all too real for you.
Ana Dascalescu
Cyber Security Enthusiast
The Atlantic wrote about cyberflâneur and I think that's the best way to describe myself. Or maybe a digital jack-of-all-trades with a long background in blogging, video production and streaming. I spend my waking hours snooping through online communities of all types, from Reddit to security forums, from gaming blogs to banal social media platforms like Instagram. Sometimes I even contribute to those communities.
Related Articles
CHECK OUR SUITE OF 11 CYBERSECURITY SOLUTIONS
- Cyber Resources And Beginners
- Cyber Security Glossary
- The Daily Security Tip
- Cyber Security For Small Business Owners
- Cybersecurity Webinars
- About Heimdal®
- Press Center
- Partner with us
- Affiliate Program
© 2024 Heimdal ®
Vat No. 35802495, Vester Farimagsgade 1, 2 Sal, 1606 København V

- Internet Ethics Cases
- Markkula Center for Applied Ethics
- Focus Areas
- Internet Ethics
Find ethics case studies on topics in Internet ethics including privacy, hacking, social media, the right to be forgotten, and hashtag activism. (For permission to reprint articles, submit requests to [email protected] .)
A fitness tracker aimed at children raises issues of design ethics, incentives, and more.
AI-generated text, voices, and images used for entertainment productions and impersonation raise ethical questions.
Ethical questions arise in interactions among students, instructors, administrators, and providers of AI tools.
What can we learn from the Tay experience, about AI and social media ethics more broadly?
Who should be consulted before using emotion-recognition AI to report on constituents’ sentiments?
When 'algorithm alchemy' wrongly accuses people of fraud, who is accountable?
Which stakeholders might benefit from a new age of VR “travel”? Which stakeholders might be harmed?
Ethical questions about data collection, data-sharing, access, use, and privacy.
As PunkSpider is pending re-release, ethical issues are considered about a tool that is able to spot and share vulnerabilities on the web, opening those results to the public.
With URVR recipients can capture and share 360 3D moments and live them out together.
- More pages:
How Hackers Attack Social Media Accounts – And How to Defend Against Them

Hey everyone, and welcome to the world of Social Media 📲.
In this article, we will explore the famous (or infamous) sphere of social media, why it is critical to both you and hackers, and how you can avoid having your social media accounts attacked.
Disclaimer: Hacking is a tool with the potential for both good and bad. Under no circumstances should the knowledge in this article be used for any harmful or illegal purposes. Doing so could lead to a long time in a jail cell 💀.
And with that, let’s jump in 🙃.
What We’ll Cover
Overview of social media platforms.
- Attack Techniques
- Defense Tips

Meta (formerly Facebook) remains one of the biggest companies on the planet.
Starting off in 2004, it redefined the way we interact with, share, and engage with the world around us. With roughly 2.98 billion monthly active users , Facebook has become an integral part of modern society, bridging gaps and fostering virtual communities.
The platform was among the pioneers of the social media craze which introduced the world to more apps such Instagram, Snapchat, Reddit, WhatsApp, YouTube, TikTok, Telegram and most notoriously, Twitter 🐦. Each and every single one of these apps have a different feel and taste to them with one underlying purpose: Connections.
Connections to people, places and products have been the centre of it all. These platforms allow you to interact with friends, as well as strangers. They also help you see the world around you in ways no one thought was possible many years ago. And if you’re a business person or content creator like I am, it allows you to show people what you have to offer.
If an attacker compromises your credentials, they have access to your connections. They could use your data to impersonate you, post illegal and harmful things, damage your reputation, spread malware, and social engineer your friends and followers on the platform in order to steal money and compromise their accounts.
According to Gitnux , there are about 1.4 billion attacks on social media platforms monthly – quite a lot isn’t it?
Many companies take the cybersecurity of their infrastructure quite seriously (most times anyway 😶). But as a consumer, you are your own last line of defense or your own greatest vulnerability.
In this article, we will take a look at some ways attackers can convert your ‘connections’ into profit and how you can defend against them. Now let’s find out how hackers can compromise your account.
Social Media Account Attack Techniques

Physical Access
This may seem obvious, but people still make this mistake a lot. An attacker could install scripts or software that would let them get the passwords of your social media accounts if they have your phone or laptop in their hand.
Software like those from Passrevelator make it easy to get passwords and other credentials from devices on different platforms.
Here's a screenshot from one of them, Pass Wi-Fi, below. This one gets all SSIDs and passwords the device has ever connected to.
Phishing links, emails, and sites
Phishing is a cyberattack in which the attacker tricks the victim into giving sensitive or critical information through fraudulent websites, forms, links or other means.
It’s pretty easy for anyone to make a Facebook clone with React Native. Tools like Zphisher and PyPhisher make it even easier for an attacker by setting up a phishing page and creating links to it, too.
As you can see, PyPhisher comes with a wide array of options for some major mayhem.
More seasoned criminals can send links in spoofed emails to make them look like they are from official organisations and can register lookalike domains to trick users.
Password Spraying and Bruteforcing
Passwords are a big security concern, and for good reason. They are often repetitive and easy to guess. Spraying is the process of trying out common passwords while Bruteforcing is the process of trying out all possible combinations to gain access.
Attackers can get the passwords they use in password spraying from common wordlists . Wordlists are a list of passwords usually gotten from data breaches. The larger the wordlist, the higher the chances of compromising any account.
Below is a screenshot of the infamous rockyou.txt wordlist from the RockYou hack of 2009.
Bruteforcing, on the other hand, involves the attacker generating a custom wordlist alongside usernames or emails on different platforms. This is more effective if the attacker has a specified target.
As you can see, attackers can use a tool known as crunch to generate a wordlist, and it has a lot of options.
If an attacker uses these techniques on a login page, this has great potential to be an entry point, especially if the site has poor security.
A Keylogger is a piece of riskware that keeps track of what a person types on their device. Think of it like your keyboard having a memory card and sending what it stores to an attacker.
Note that keyloggers aren’t inherently bad, as they can also be used for organisational monitoring and parental control. But an attacker does not have authorization to monitor your keystrokes, which makes its use illegitimate.
An attacker could install a keylogger and monitor the victim's keystrokes. All they have to do is wait and read the logs for a peculiar sequence, usually one with an email, followed by a string of characters before the ‘return’ keystroke.
It would usually look something like this:

Usually, the entire log will be monochrome but for this example I made a few modifications. The red highlight indicates an email account, which is what an attacker would be looking for. Close behind is the password in blue.
Network Sniffing
Also known as packet sniffing, this is the practice of intercepting and analysing network packets in order to find out what kind of information is shared within the network.
If connections are not properly encrypted, an attacker could easily obtain sensitive information about the sites visited and the messages and passwords that are sent and inputted in them, respectively. WireShark is one of the most common tools for this kind of attack.
Data Breaches
Data breaches are unintentional leaks of sensitive or confidential information. These are usually more devastating to users than organisations and could have far-reaching consequences.
Passwords and login credentials from data leaks can be sold and purchased on the dark web. They are then used to gain unauthorised access to the account and the rest is history.
How to Defend Against Social Media Attacks

As you can see, there are many ways to obtain Social Media account credentials. Below are some ways to ensure you are not a victim.
Check the URL
Always double check any links sent to you via messaging platforms or email. This is a simple but very effective measure against phishing links and sites, as the likelihood of clicking on the wrong link is much lower.
For example, www.facebook.com and www.facebok.com are not the same. As you can observe in the screenshots below, the former is legitimate while an antivirus warns me that the later is a phishing site.
Use strong passwords/passphrases
Make sure you use strong passwords and don’t use similar passwords for different accounts (not even variants 👀). You can also use passphrases rather than passwords as they are easier to remember but harder to guess or bruteforce.
An example of a password is 'dictionary'. An example of a passphrase is 'mydictionaryisthelargest'. The password is weak and could be guessed or found easily in a wordlist. The passphrase isn't the strongest but it is quite lengthy and would be almost impossible to find in a wordlist or to be guessed.
Use Antivirus Software and Firewalls
An Antivirus is a software solution that protects systems against both internal and external threats based on the vendor. A Firewall, on the other hand, protects systems against external threats based on your preferences and settings.
The use of one or both of these products can go a long way in protecting both individuals and organisations from information stealing malware.
A Virtual Private Network is a secure network connection that connects you to the internet privately and anonymously. This is done by encrypting the connection and routing it through remote servers.
VPNs are a great option to avoid packet sniffers because packets analysed are encrypted. This means it’s going to be quite difficult for an attacker to get passwords from technical gibberish.
Tracking Breaches
Tracking breaches can be done at an individual or enterprise level. It’s effectiveness, however, usually depends on how much you are willing to pay for it.
Individuals can use sites like haveibeenpwned.com to check if their data has been compromised in any breaches and Enterprises can setup security units with the role of constantly monitoring the Internet for breaches related to them.

Getting credentials is pretty easy with some determination and a touch of mischievousness. But companies have gotten better at defense in recent years and attackers have had to get more creative.
As an individual, you are your last and dare I say best line of defense. Ensure your shields are always up in the online jungle. Stay safe and Happy Hacking 🙃.
Acknowledgements
Thanks to Anuoluwapo Victor , Chinaza Nwukwa , Holumidey Mercy , Favour Ojo , Georgina Awani , and my family for the inspiration, support and knowledge used to put this together. You’re the best.
- Social Media Attack Statistics
- GUI tools for physical access hacking
Just another guy fascinated by the world of Hacking, Cybersecurity and the Internet
If you read this far, thank the author to show them you care. Say Thanks
Learn to code for free. freeCodeCamp's open source curriculum has helped more than 40,000 people get jobs as developers. Get started
- Artificial Intelligence
- Generative AI
- Business Operations
- IT Leadership
- Application Security
- Business Continuity
- Cloud Security
- Critical Infrastructure
- Identity and Access Management
- Network Security
- Physical Security
- Risk Management
- Security Infrastructure
- Vulnerabilities
- Software Development
- Enterprise Buyer’s Guides
- United States
- Deutschland (Germany)
- United Kingdom
- Newsletters
- Foundry Careers
- Terms of Service
- Privacy Policy
- Cookie Policy
- Member Preferences
- About AdChoices
- E-commerce Links
- Your California Privacy Rights
Our Network
- Computerworld
- Network World


The 18 biggest data breaches of the 21st century
Data breaches affecting millions of users are far too common. here are some of the biggest, baddest breaches in recent memory..

In today’s data-driven world, data breaches can affect hundreds of millions or even billions of people at a time. Digital transformation has increased the supply of data moving, and data breaches have scaled up with it as attackers exploit the data-dependencies of daily life. How large cyberattacks of the future might become remains speculation, but as this list of the biggest data breaches of the 21 st Century indicates, they have already reached enormous magnitudes.
For transparency, this list has been calculated by the number of users impacted, records exposed, or accounts affected. We have also made a distinction between incidents where data was actively stolen or reposted maliciously and those where an organization has inadvertently left data unprotected and exposed, but there has been no significant evidence of misuse. The latter have purposefully not been included in the list.
So, here it is – an up-to-date list of the 15 biggest data breaches in recent history, including details of those affected, who was responsible, and how the companies responded (as of July 2021).
Date: August 2013 Impact: 3 billion accounts
Securing the number one spot – almost seven years after the initial breach and four since the true number of records exposed was revealed – is the attack on Yahoo. The company first publicly announced the incident – which it said took place in 2013 – in December 2016. At the time, it was in the process of being acquired by Verizon and estimated that account information of more than a billion of its customers had been accessed by a hacking group. Less than a year later, Yahoo announced that the actual figure of user accounts exposed was 3 billion. Yahoo stated that the revised estimate did not represent a new “security issue” and that it was sending emails to all the “additional affected user accounts.”
Despite the attack, the deal with Verizon was completed, albeit at a reduced price. Verizon’s CISO Chandra McMahon said at the time: “Verizon is committed to the highest standards of accountability and transparency, and we proactively work to ensure the safety and security of our users and networks in an evolving landscape of online threats. Our investment in Yahoo is allowing that team to continue to take significant steps to enhance their security, as well as benefit from Verizon’s experience and resources.” After investigation, it was discovered that, while the attackers accessed account information such as security questions and answers, plaintext passwords, payment card and bank data were not stolen.
2. Aadhaar [tie with Alibaba]
Date: January 2018 Impact: 1.1 billion Indian citizens’ identity/biometric information exposed
In early 2018, news broke that malicious actors has infiltrated the world’s largest ID database, Aadhaar , exposing information on more than 1.1 billion Indian citizens including names, addresses, photos, phone numbers, and emails, as well as biometric data like fingerprints and iris scans. What’s more, since the database – established by the Unique Identification Authority of India (UIDAI) in 2009 – also held information about bank accounts connected with unique 12-digit numbers, it became a credit breach too. This was despite the UIDAI initially denying that the database held such data
The actors infiltrated the Aadhaar database through the website of Indane, a state-owned utility company connected to the government database through an application programming interface that allowed applications to retrieve data stored by other applications or software. Unfortunately, Indane’s API had no access controls, thus rendering its data vulnerable. Hackers sold access to the data for as little as $7 via a WhatsApp group. Despite warnings from security researchers and tech groups, it took Indian authorities until March 23, 2018, to take the vulnerable access point offline.
2. Alibaba [tie with Aadhaar]
Date: November 2019 Impact: 1.1 billion pieces of user data
Over an eight-month period, a developer working for an affiliate marketer scraped customer data, including usernames and mobile numbers, from the Alibaba Chinese shopping website, Taobao, using crawler software that he created. It appears the developer and his employer were collecting the information for their own use and did not sell it on the black market, although both were sentenced to three years in prison.
A Taobao spokesperson said in a statement : “Taobao devotes substantial resources to combat unauthorized scraping on our platform, as data privacy and security is of utmost importance. We have proactively discovered and addressed this unauthorized scraping. We will continue to work with law enforcement to defend and protect the interests of our users and partners.”
4. LinkedIn
Date: June 2021 Impact: 700 million users
Professional networking giant LinkedIn saw data associated with 700 million of its users posted on a dark web forum in June 2021, impacting more than 90% of its user base. A hacker going by the moniker of “God User” used data scraping techniques by exploiting the site’s (and others’) API before dumping a first information data set of around 500 million customers. They then followed up with a boast that they were selling the full 700 million customer database. While LinkedIn argued that as no sensitive, private personal data was exposed, the incident was a violation of its terms of service rather than a data breach, a scraped data sample posted by God User contained information including email addresses, phone numbers, geolocation records, genders and other social media details, which would give malicious actors plenty of data to craft convincing, follow-on social engineering attacks in the wake of the leak, as warned by the UK’s NCSC .
5. Sina Weibo
Date: March 2020 Impact: 538 million accounts
With over 600 million users, Sina Weibo is one of China’s largest social media platforms. In March 2020, the company announced that an attacker obtained part of its database, impacting 538 million Weibo users and their personal details including real names, site usernames, gender, location, and phone numbers. The attacker is reported to have then sold the database on the dark web for $250.
China’s Ministry of Industry and Information Technology (MIIT) ordered Weibo to enhance its data security measures to better protect personal information and to notify users and authorities when data security incidents occur. In a statement , Sina Weibo argued that an attacker had gathered publicly posted information by using a service meant to help users locate the Weibo accounts of friends by inputting their phone numbers and that no passwords were affected. However, it admitted that the exposed data could be used to associate accounts to passwords if passwords are reused on other accounts. The company said it strengthened its security strategy and reported the details to the appropriate authority.
6. Facebook
Date: April 2019 Impact: 533 million users
In April 2019, it was revealed that two datasets from Facebook apps had been exposed to the public internet. The information related to more than 530 million Facebook users and included phone numbers, account names, and Facebook IDs. However, two years later (April 2021) the data was posted for free, indicating new and real criminal intent surrounding the data. In fact, given the sheer number of phone numbers impacted and readily available on the dark web as a result of the incident, security researcher Troy Hunt added functionality to his HaveIBeenPwned (HIBP) breached credential checking site that would allow users to verify if their phone numbers had been included in the exposed dataset.
“I’d never planned to make phone numbers searchable,” Hunt wrote in blog post . “My position on this was that it didn’t make sense for a bunch of reasons. The Facebook data changed all that. There’s over 500 million phone numbers but only a few million email addresses so >99% of people were getting a miss when they should have gotten a hit.”
7. Marriott International (Starwood)
Date: September 2018 Impact: 500 million customers
Hotel Marriot International announced the exposure of sensitive details belonging to half a million Starwood guests following an attack on its systems in September 2018. In a statement published in November the same year, the hotel giant said: “On September 8, 2018, Marriott received an alert from an internal security tool regarding an attempt to access the Starwood guest reservation database. Marriott quickly engaged leading security experts to help determine what occurred.”
Marriott learned during the investigation that there had been unauthorized access to the Starwood network since 2014. “Marriott recently discovered that an unauthorized party had copied and encrypted information and took steps towards removing it. On November 19, 2018, Marriott was able to decrypt the information and determined that the contents were from the Starwood guest reservation database,” the statement added.
The data copied included guests’ names, mailing addresses, phone numbers, email addresses, passport numbers, Starwood Preferred Guest account information, dates of birth, gender, arrival and departure information, reservation dates, and communication preferences. For some, the information also included payment card numbers and expiration dates, though these were apparently encrypted.
Marriot carried out an investigation assisted by security experts following the breach and announced plans to phase out Starwood systems and accelerate security enhancements to its network. The company was eventually fined £18.4 million (reduced from £99 million) by UK data governing body the Information Commissioner’s Office (ICO) in 2020 for failing to keep customers’ personal data secure. An article by New York Times attributed the attack to a Chinese intelligence group seeking to gather data on US citizens.
Date: 2014 Impact: 500 million accounts
Making its second appearance in this list is Yahoo, which suffered an attack in 2014 separate to the one in 2013 cited above. On this occasion, state-sponsored actors stole data from 500 million accounts including names, email addresses, phone numbers, hashed passwords, and dates of birth. The company took initial remedial steps back in 2014, but it wasn’t until 2016 that Yahoo went public with the details after a stolen database went on sale on the black market.
9. Adult Friend Finder
Date: October 2016 Impact: 412.2 million accounts
The adult-oriented social networking service The FriendFinder Network had 20 years’ worth of user data across six databases stolen by cyber-thieves in October 2016. Given the sensitive nature of the services offered by the company – which include casual hookup and adult content websites like Adult Friend Finder, Penthouse.com, and Stripshow.com – the breach of data from more than 414 million accounts including names, email addresses, and passwords had the potential to be particularly damning for victims. What’s more, the vast majority of the exposed passwords were hashed via the notoriously weak algorithm SHA-1, with an estimated 99% of them cracked by the time LeakedSource.com published its analysis of the data set on November 14, 2016.
10. MySpace
Date: 2013 Impact: 360 million user accounts
Though it had long stopped being the powerhouse that it once was, social media site MySpace hit the headlines in 2016 after 360 million user accounts were leaked onto both LeakedSource.com and put up for sale on dark web market The Real Deal with an asking price of 6 bitcoin (around $3,000 at the time).
According to the company , lost data included email addresses, passwords and usernames for “a portion of accounts that were created prior to June 11, 2013, on the old Myspace platform. In order to protect our users, we have invalidated all user passwords for the affected accounts created prior to June 11, 2013, on the old Myspace platform. These users returning to Myspace will be prompted to authenticate their account and to reset their password by following instructions.”
It’s believed that the passwords were stored as SHA-1 hashes of the first 10 characters of the password converted to lowercase.
11. NetEase
Date: October 2015 Impact: 235 million user accounts
NetEase, a provider of mailbox services through the likes of 163.com and 126.com, reportedly suffered a breach in October 2015 when email addresses and plaintext passwords relating to 235 million accounts were being sold by dark web marketplace vendor DoubleFlag. NetEase has maintained that no data breach occurred and to this day HIBP states : “Whilst there is evidence that the data itself is legitimate (multiple HIBP subscribers confirmed a password they use is in the data), due to the difficulty of emphatically verifying the Chinese breach it has been flagged as “unverified.”
12. Court Ventures (Experian)
Date: October 2013 Impact: 200 million personal records
Experian subsidiary Court Ventures fell victim in 2013 when a Vietnamese man tricked it into giving him access to a database containing 200 million personal records by posing as a private investigator from Singapore. The details of Hieu Minh Ngo’s exploits only came to light following his arrest for selling personal information of US residents (including credit card numbers and Social Security numbers) to cybercriminals across the world, something he had been doing since 2007. In March 2014, he pleaded guilty to multiple charges including identity fraud in the US District Court for the District of New Hampshire. The DoJ stated at the time that Ngo had made a total of $2 million from selling personal data.
13. LinkedIn
Date: June 2012 Impact: 165 million users
With its second appearance on this list is LinkedIn, this time in reference to a breach it suffered in 2012 when it announced that 6.5 million unassociated passwords (unsalted SHA-1 hashes) had been stolen by attackers and posted onto a Russian hacker forum. However, it wasn’t until 2016 that the full extent of the incident was revealed. The same hacker selling MySpace’s data was found to be offering the email addresses and passwords of around 165 million LinkedIn users for just 5 bitcoins (around $2,000 at the time). LinkedIn acknowledged that it had been made aware of the breach, and said it had reset the passwords of affected accounts.
14. Dubsmash
Date: December 2018 Impact: 162 million user accounts
In December 2018, New York-based video messaging service Dubsmash had 162 million email addresses, usernames, PBKDF2 password hashes, and other personal data such as dates of birth stolen, all of which was then put up for sale on the Dream Market dark web market the following December. The information was being sold as part of a collected dump also including the likes of MyFitnessPal (more on that below), MyHeritage (92 million), ShareThis, Armor Games, and dating app CoffeeMeetsBagel.
Dubsmash acknowledged the breach and sale of information had occurred and provided advice around password changing. However, it failed to state how the attackers got in or confirm how many users were affected.
Date: October 2013 Impact: 153 million user records
In early October 2013, Adobe reported that hackers had stolen almost three million encrypted customer credit card records and login data for an undetermined number of user accounts. Days later, Adobe increased that estimate to include IDs and encrypted passwords for 38 million “active users.” Security blogger Brian Krebs then reported that a file posted just days earlier “appears to include more than 150 million username and hashed password pairs taken from Adobe.” Weeks of research showed that the hack had also exposed customer names, password, and debit and credit card information. An agreement in August 2015 called for Adobe to pay $1.1 million in legal fees and an undisclosed amount to users to settle claims of violating the Customer Records Act and unfair business practices. In November 2016, the amount paid to customers was reported to be $1 million.
16. National Public Data
Date: December 2023 Impact: 270 million people
A breach of background checking firm National Public Data exposed the data of hundreds of millions of people through the disclosure of an estimated 2.9 billion records. As a result of the December 2023 hack, stolen data was up for sale of on the dark web by hacking group USDoD in April 2024. Much of the stolen data was leaked and made freely available in a 4TB dump onto a cybercrime forum July 2024.
The incident, which only became public knowledge after a class action was filed in August 2024, exposed social security numbers, names, mailing addresses, emails, and phone numbers of 270 million people, mostly US citizens. Much of the data, which also includes information pertaining to Canadian and British residents, appears to be outdated or inaccurate but the impact of the exposure of so much personal information is nonetheless severe. An estimated 70 million rows of records cover US criminal records.
The mechanism of the initial breach remains unconfirmed but investigative reporter Brian Krebs reports that up until early August 2024 an NPD property, recordscheck.net, contained the usernames and password for the site’s administrator in a plain text archive.
In a statement , Jericho Pictures (which trades as National Public Data) advised people to closely monitor their financial accounts for unauthorised activity. National Public Data said it was working with law enforcement and governmental investigators adding that it is reviewing potentially affected records to understand the scope of the breach. It will “try to notify” affected parties if there are “further significant developments”.
Experts advise consumers to consider freezing credit with the three major bureaus (Equifax, Experian, and TransUnion) and using identity theft protection services as potential precautions.
17. Equifax
Date: 2017 Impact: 159 million records
Credit reference agency Equifax suffered a data breach in 2017 that affected 147 million US citizens and 15 million Britons. Names, social security numbers, birth dates, addresses as well as driver’s licenses of more than 10 million were exposed after attackers took advantage of a web security vulnerability to break into Equifax’s systems. The breach also exposed the credit card data of a smaller group of 209,000 people.
Attackers broke into Equifax’s systems between May and July 2017 by taking advantage of an unpatched Apache Struts vulnerability to hack into the credit reference agency’s dispute resolution portal. Patches for the exploited vulnerability had been available since March 2017, months before the attack. Struts is a popular framework for creating Java-based web applications.
Cybercriminals moved laterally through their ingress points before stealing credentials that allowed them to query its databases, systematically siphoning off stolen data. US authorities charged four named members of the Chinese military with masterminding the hack. Chinese authorities have denied any involvement in the attack.
Equifax faced numerous lawsuits and government investigations in the wake of the breach. The credit reference agency was left an estimated $1.7 billion out of pocket because of the breach without taking into account the effect on its stock price. Equifax spent an estimated $337 million on improving its technology and data security, legal and computer forensic fees and other direct costs alone.
Date: 2014 Impact: 145 million records
A breach on online marketplace eBay between late February and early March 2014 exposed sensitive personal information of an estimated 145 million user accounts. Cybercriminals gained access to eBay’s systems after compromising a small number of employee login credentials.
The hack allowed miscreants access to sensitive information including encrypted passwords, email addresses, mailing addresses, phone numbers and dates of birth. Financial information, including data on PayPal accounts, was stored on separate system and therefore not affected by the breach. In response to the incident, eBay applied a forced reset to user passwords.
More news-making data breaches:
- Hackers steal data of 200k Lulu customers in an alleged breach
- Evolve data breach impacted upward of 7.64 million consumers
The biggest data breach fines, penalties, and settlements so far
- Dell data breach exposes data of 49 million customers
- Sensitive US government data exposed after Space-Eyes data breach
Related content
Most interesting products to see at rsac 2024, google launches google threat intelligence at rsa conference, accenture, ibm, mandiant join elite cyber defenders program to secure critical infrastructure, from our editors straight to your inbox.

Michael Hill is the UK editor of CSO Online. He has spent the past five-plus years covering various aspects of the cybersecurity industry, with particular interest in the ever-evolving role of the human-related elements of information security. A keen storyteller with a passion for the publishing process, he enjoys working creatively to produce media that has the biggest possible impact on the audience.
More from this author
What is the cost of a data breach, cyber insurance explained: costs, terms, how to know it’s right for your business, notable post-quantum cryptography initiatives paving the way toward q-day, if you don’t already have a generative ai security policy, there’s no time to lose, bigid unveils new data risk remediation guidance feature, generative ai could erode customer trust, half of business leaders say, us launches “shields ready” campaign to secure critical infrastructure.

Dan Swinhoe is UK Editor of CSO Online. Previously he was Senior Staff Writer at IDG Connect.
EU’s DORA regulation explained: New risk management requirements for financial firms
Man-in-the-middle (mitm) attack definition and examples, how decision-making psychology can improve incident response, how stagecoach stops bec attacks with security training, email controls, interim data deal and brexit: what cisos need to know now the uk has left the eu, uk telecommunications security bill aims to improve telco security for 5g rollouts, what is typosquatting a simple but effective attack technique, what cisos need to know about europe’s gaia-x cloud initiative.

John Leyden is a senior writer for CSO Online. He has written about computer networking and cyber-security for more than 20 years. Prior to the advent of the web, he worked as a crime reporter at a local newspaper in Manchester, UK. John holds an honors degree in electronic engineering from City, University of London.
The ransomware negotiation playbook adds new chapters
Low turnover leaves job-seeking cisos with nowhere to go, eu’s nis2 directive for cybersecurity resilience enters full enforcement, security spending signals major role change for cisos and their teams, crowdstrike outage redefines edr market emphasis, cyber insurance price hikes stabilize as insurers expect more from cisos, patch management: a dull it pain that won’t go away, how not to hire a north korean it spy, show me more, cisos have to get on top of ai technologies, warns microsoft.

Sophos to acquire rival Secureworks in $859 million deal

Critical Fortinet vulnerability finds zero-day RCE exploits

CSO Executive Sessions: Guardians of the Games - How to keep the Olympics and other major events cyber safe

CSO Executive Session India with Dr Susil Kumar Meher, Head Health IT, AIIMS (New Delhi)

CSO Executive Session India with Charanjit Bhatia, Head of Cybersecurity, COE, Bata Brands

CSO Executive Sessions: Standard Chartered’s Alvaro Garrido on cybersecurity in the financial services industry

CSO Executive Sessions: New World Development’s Dicky Wong on securing critical infrastructure

CSO Executive Sessions: DocDoc’s Rubaiyyaat Aakbar on security technology

Sponsored Links
- Get Cisco UCS X-Series Chassis and Fabric Interconnects offer.

Ethical Hacking Case Study: Times When Hackers Avoided Setbacks
Home Blog Security Ethical Hacking Case Study: Times When Hackers Avoided Setbacks
Over the years, there has been a huge rise in cybercrime attacks due to the general public's lack of knowledge about hacking and internet-related crimes. Unfortunately, this goes for both common people as well as big companies. People generally think that having an antivirus that offers cyber security is enough for them to stay safe on the internet. The same goes for big corporations that do not use high-quality protection for their data. This is where ethical hackers come into play with some really impressive ethical hacking cases where they saved the day.
Ethical Hacking - An Overview
Bypassing or breaking through the security mechanisms of a system to search for vulnerabilities, data breaches, and other possible threats is an example of ethical hacking. It has to be done ethically to comply with the laws and regulations relevant to the area or the company. Because an individual must go through several procedures to get into a system and record it, this form of infiltration is referred to as "penetration testing" in the industry jargon. This is because an individual must record the system after entering it.
You must be wondering what ethical hackers are? They are people who possess the same knowledge as hackers but use this knowledge to boost internet protection protocols and software. You, too, can learn how to be an ethical hacker using a CEH certification training course. They are the ones who protect us from actual hackers. There are multiple categories of ethical hackers, such as:
- Black hat hackers: They use their knowledge for malicious intent, blackmail, etc.
- White hat hackers: They possess the same knowledge as the black hat hackers but use their knowledge to help companies increase their defenses against the black hat hackers.
How Do White Hat Hackers Work?
With the growing rise in hackers on the internet, companies have begun using ethical hackers to scope out the flaws and vulnerabilities in their software and protection programs. But, how do these ethical hacking cases work? These people use the same techniques as Black hat hackers to penetrate a company's defenses. By doing so, they can understand the safety flaws. This gives them the inside edge to patch the flaws to ensure that hackers cannot get through the protection.
There have been multiple instances where ethical hackers have been able to spot cracks in a company's security and save them from having huge security leaks due to hackers, which would result in huge losses. The following ethical hacking case study is six instances where ethical hackers were able to save a company from dealing with data leaks and suffering huge financial losses.
Case Studies of Ethical Hacking
1. a crack in wordpress leaked user information.
Back in 2019, a new plugin was released for WordPress called Social Network Tabs. As you know, most people use WordPress to make their websites. This plugin got very popular, but none knew about the vulnerability. It basically helped users share their website content on social media.
Baptiste Robert was a French security researcher who was known online by his user handle, Elliot Alderson. He was the one who found the crack in the plugin, which was given the ID CVE-2018-20555 by MITRE. You can find this case and similar ones in a case study on ethical hacking PDF online.
You must be wondering what exactly did this flaw in the plugin do? The flaw in the plugin compromised the user's Twitter account. Since the plugin is connected to the user's social media account, the vulnerability leaked the user's social media details. Robert was the first to spot this leak and was fast to notify Twitter about it, which helped secure the user's accounts that got affected by it.
2. Oracle's vulnerability in their WebLogic servers
In 2019, Oracle released a security update without any prior notice. This took fans by surprise until they learned why this happened. The security patch was a very critical update that fixed a code vulnerability in the WebLogic Server.
The flaw was brought to light by a security firm known as KnownSec404. The vulnerability was labeled as CVE-2019-2729 which received a level of 9.8/10, which is pretty high. The vulnerability left it open to be attacked by hackers targeting two applications that the server left open to the internet.
3. Visa card vulnerability that allowed for a bypass in payment limits
This was one of the most famous ethical hacking cases brought to light on the internet. It took place on July 29th, 2019. Two security researchers from a company called Positive Technologies spotted a security weakness in Visa contactless cards that allowed hackers to bypass the payment limits. This flaw in their security would cost the company a huge loss. This one case boosted the interest in ethical hacking. As a result, multiple students began taking cyber security course certificates online to learn more.
Tim Yunusov, the Head of Banking security, and Leigh-Anne Galloway, the Cyber Security Resilience Lead, were the ones who discovered this. This was made public after five major UK banks were targeted. The contactless verification had a limit of £30 on Visa cards, but due to this weakness, hackers could bypass this limit.
4. Vulnerabilities allow for ransomware in Canon DSLR
In 2019, the DefCon27 was held, which was attended by Eyal Itkin. He was a vulnerability researcher at Check Point Software Technologies. He revealed that the Canon EOS 80D DSLR had a vulnerability that the PTP, which was the Picture Transfer Protocol, had an issue whereby ransomware could be transferred into the DSLR using the WiFi connection.
He went on to highlight that there were six vulnerabilities in the PTP that made it an easy target for hackers. They could easily get into the DSLR using this crack in the firmware. The objective of the hackers was simple. Infiltrate the DSLR and infect it with ransomware that would render the pictures useless to the user. The user would have to pay a ransom to get the pictures back to the hacker.
The team working with Eyal informed Canon about the security breach vulnerability. A few months later, Canon released a notice saying that the vulnerability was never exploited by hackers, which means that it was never discovered. However, they also announced that users should take safety precautions to keep themselves safe.
5. Zoom on the Mac could be hacked and expose the camera
On July 9th, 2019, Jonathan Leitschuh exposed a very critical vulnerability in Appel's Macs. This flaw in the security framework allowed hackers to take control of the user's front camera. As a result, many websites could force a user into a Zoom call without their knowledge or permission. This was something that invaded privacy, and millions of people who would conduct meetings or even use Zoom, in general, were at risk. This is an important ethical hacking case as it was broken on social media to make people aware. The very same day, Apple sent out a fix that was a simple patch that users could download and install to fix the issue. Zoom, too, didn't waste any time by issuing a quick-fix patch to stop the issue.
6. A backdoor could allow hackers to execute root commands on servers
DefCon27 was where many ethical hacking cases came to light. Another one was the case of Özkan Mustafa Akkuş, who was a Turkish security researcher. They exposed a vulnerability in Webmin, a web-based system configuration in Unix-like systems.
The vulnerability was labeled CVE-2019-15107; it was a backdoor entry that allowed hackers to execute commands with root privileges. This left users exposed to hackers that could take control of their systems or hold it for ransom.
This is an important ethical hacking case study as Jamie Cameron, who is the author of Webmin, claimed that the backdoor was set by an employee. This was something that wasn't known to the company. They announced a new patch update to the new software version, which would be released to all the users.
A very important case study to know about that was featured in the case study of ethical hacking PDF was that of Zomato in India.
7. What happened to Zomato?
In 2017 a hacker broke into the security of Zomato, one of the biggest online restaurant guides and food ordering apps. The hacker was after five things.
- Names
- Emails
- Numeric user IDs
- User names
- Passwords
The amount of data lost was in the millions as 17 million users were targets. The hacker was able to put up this information on the darknet for anyone to buy before starting talks with the company. This was one of the most shocking ethical hacking cases in India. This also led people to question the cyber security of the country.
Once this case was exposed to the public, Zomato issued a few blogs where they spoke about the real person behind this breach. It was said that the work was done by an ethical hacker who wanted to bring the issue of national cyber security to light. It worked as the whole country began talking about cyber security.
8. The bug bounty program
This was a reward program started to get talented individuals to use their hacking skills to expose the weaknesses in the company's security programs. Today, multiple companies use this program to find the issues in their security. Companies like Google, Microsoft, and Facebook have invested millions in this program to find the flaws in their system and make them stronger against cyber-attacks.
The individual can get cash awards or even recognize if they can point out and fix the issue. This has brought to light multiple numbers of issues as well as many talented, ethical hacker cases that we have ever seen.
Many people are now interested in taking up ethical hacking as their career. You can get the KnowledgeHut’s CEH certification training to learn more about ethical hacking.
In conclusion, ethical hackers are essential to the cyber security field. They are the ones who can figure out the flaws in any system and the ones who can also provide quick fixes. They are important to know how to keep your data safe in these troubled times. If you wish to know more about ethical hacking, you can get the case study on ethical hacking PDF, which you can find online. These case studies are important as they highlight the weakness in online security firmware. These need to be fixed as they could mean a potential data leak which could result in a huge financial and reputation loss for the companies that suffer it. Employing White Hat hackers is one way of fighting against it.
Frequently Asked Questions (FAQs)
An example of ethical hacking done by White Hat hackers is simulating an attack on a system to see if there are any flaws in the system. They can also use the information found online about the company to find a way to infiltrate the company's security.
The role of an ethical hacker is simple. They possess the same knowledge as Black Hat hackers. But, the only difference is that they use their knowledge to spot the flaws in security systems so that they can fix them. They just want to make the security impenetrable to any attacks.
The five steps are:
- Reconnaissance: This step is about understanding the network and security features.
- Scanning: This is where they scan for the flaws in the system to see if there could be any entry.
- Gain Access: This is where they gain access to the system by any means necessary.
- Maintain Access: This is where they keep their presence inside the security software or firmware without alarming anyone or losing access to the system.
- Cover Tracks: This is where they cover up any tracks they left while getting inside or leaving the system.

Vitesh Sharma
Vitesh Sharma, a distinguished Cyber Security expert with a wealth of experience exceeding 6 years in the Telecom & Networking Industry. Armed with a CCIE and CISA certification, Vitesh possesses expertise in MPLS, Wi-Fi Planning & Designing, High Availability, QoS, IPv6, and IP KPIs. With a robust background in evaluating and optimizing MPLS security for telecom giants, Vitesh has been instrumental in driving large service provider engagements, emphasizing planning, designing, assessment, and optimization. His experience spans prestigious organizations like Barclays, Protiviti, EY, PwC India, Tata Consultancy Services, and more. With a unique blend of technical prowess and management acumen, Vitesh remains at the forefront of ensuring secure and efficient networking solutions, solidifying his position as a notable figure in the cybersecurity landscape.
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Cyber Security Batches & Dates
Rise of social media hacking devastating creative small businesses

Creatives can face massive losses if their social media accounts are hacked, often with little recourse to reinstate their data. Photo: Magnus Mueller, Pexels.
Hacking, scamming, phishing, cyber fraud… These terms were once only vague notions to anyone other than tech workers.
But they are now very familiar parts of our everyday lexicon as our online lives continue to swirl with potential criminal activity.
In the creative sector, arts freelancers and small businesses are especially vulnerable to these threats, as hackers seek to target smaller entities whose security systems lack the robust protocols of their larger corporate counterparts.
According to several Australian creatives whose social media accounts have recently been hacked, it’s all too easy for valuable online content to go up in smoke, with few options to retrieve lost data or reinstate accounts.
The stories of two such arts freelancers reveal there are depressingly few avenues to recoup lost assets after an account has been hacked. Instead, you can feel like a powerless cog within the tech giants’ machines, with little or no support offered from the tech companies’ side to help fix your problems.
Stories from the frontline of social media hacking
Until two months ago, arts journalist Stephen A Russell had been using his personal Facebook page as an important promotional platform to share his articles and expand his readership.
But after noticing what he describes as an “obviously fake” business account newly linked to his personal Facebook account, he became suspicious, and attempted to contact Facebook/Meta to alert the platform of the fraudulent activity. However, it was only after hours spent trawling Facebook’s labyrinthine online help pages and having ‘chats’ with Meta support-bots that Russell finally got through to a human Facebook support worker who offered to call him by phone to help him with his concerns. As Russell tells ArtsHub , “In that phone call I had to repeatedly tell the Facebook representative that, ‘No, I definitely had not set up the business account that was appearing as linked to my real Facebook account, and that my account was almost certainly being hacked’.”
Read: Spike in social media identity theft hits sector (from 2022)
Then, after only a few minutes on the line, Russell says the phone connection suddenly and mysteriously went dead.
“Since then, I have had zero contact from Facebook. No call backs, no emails – nothing,” he says.
“The only action taken by Meta since then has been to wipe my Facebook account completely,” Russell continues.
“That’s years and years worth of personal and professional content and conversations – gone.”
Alarmingly, the hackers also gained access to Russell’s credit card details that the writer says he had used only a few times on Facebook, to make donations to charitable causes that came up on his feed.
“I definitely didn’t have my credit card stored in my Facebook account, but the hackers managed to locate the historical transactions I had made there,” he explains.
“They also managed to change my two-step authentication security email address and phone number on the account, and I received no alert from Facebook that these details had been changed, and so that blocked me from accessing my Facebook page ever again.”
Overall, the writer says the loss of all his Facebook interactions over the years has been devastating, but the realisation that Facebook’s security systems are ill-equipped to keep his account safe from hackers, is probably the rudest shock of all.
“I found the situation terrifying and have found Facebook manifestly and disgracefully negligent in their complete lack of support,” he tells ArtsHub .
“I’m also quite disgusted at how terrible their security evidently is, and I think many people are simply unaware of how dangerous it can be.”
Unknowable costs of hacks to artists
Since losing his Facebook account, Russell has felt dislocated from his social circles and family overseas, and he has also been missing important business connections, too. “Facebook was a big source of my readership, so it’s been a real blow,” he says. “And I’ll never know exactly how much it’s cost me [from a business point of view], because it’s just been totally erased, overnight.”
Like Russell, Brisbane-based dance artist Neridah Waters is also feeling uncertain of the real costs to her creative enterprise since her Facebook accounts were hacked in similar fashion one month ago.
“I expect there are clients trying to contact me through my hacked account, but I can no longer access it, so I will never know,” Waters tells ArtsHub.
The dancer and choreographer, who has been running her dance workshops and events business for the past 15 years, had her personal Facebook page wiped by Meta a month ago, after it was compromised by a hacker.
“The hackers got in through my email address that was linked to my personal Facebook account,” she explains.
“That was bad enough, but the more serious result is that because my personal Facebook account is the administrator of my business’ Facebook account, I have lost access to both.
“My business Facebook account and page actually still exists online,” she continues. “But I can’t access it because my administrator access is gone. Which is weird – because I have a page that’s still live, but I can’t access or update it.”
Read: 3 social media scams every artist needs to know about
In addition to the potential reputational damage of having outdated content posted online, Waters says the hack also resulted in untold hours of logistical work for her to ensure one of her biggest events of the year could still happen.
“The hack occurred three weeks before a major dance event that I produced for the Brisbane Festival, with 300 performers involved,” she says.
“I was managing all the communications for that event through Facebook Groups, so I had to somehow re-establish connections with all those groups and performers.
“In the end I used my Instagram account for most of that, but it was really stressful.”
Waters adds that, like Russell, she has found Facebook/Meta to be of little help throughout the ordeal.
“I haven’t been able to contact a human at Facebook at all,” she says. “The best that’s been offered are links to Facebook’s ‘Frequently Asked Questions’ support page, and other help links that just take me in circles.”
Tips to protect your data
As Russell and Waters have been made all too aware, doing business on social media can be one of the easiest things in the world, until the system breaks down and you are left vulnerable and subject to unforeseen costs.
That said, there are a few simple ways to help protect yourself from worst case outcomes (though there are still no guarantees):
Some top tips:
1. Vary passwords across your online accounts (never use the same password for more than one account).
2. Use complex passwords (over 12 characters).
3. Enable two-factor-authentication security protocols on account logins.
4. Ensure multiple account administrators where relevant (if one admin account is compromised, there will still be an admin who can access the account).
5. Monitor account logins regularly (most account dashboards can show you the last time an account was accessed, and by which device, in which location).
6. Report suspicious account activity immediately (but, as above, if you are using a free account, don’t expect to receive effective customer support).
7. Be mindful of the risk of hacking and make a plan for worse case scenarios. Ask yourself, how will I operate a business if I suddenly lose my social media account/s? How can I back up my most important content/contacts etc?
Share this:
ArtsHub's Arts Feature Writer Jo Pickup is based in Perth. An arts writer and manager, she has worked as a journalist and broadcaster for media such as the ABC, RTRFM and The West Australian newspaper, contributing media content and commentary on art, culture and design. She has also worked for arts organisations such as Fremantle Arts Centre, STRUT dance, and the Aboriginal Arts Centre Hub of WA, as well as being a sessional arts lecturer at The Western Australian Academy of Performing Arts (WAAPA).
Related News

This week's arts news and trending topics
We report it – you read it. This week's top arts news stories.
Gina Fairley

Opportunities and awards
International residency opportunity in New York, winners of Melbourne Fringe, Chief Minister's NT Book Awards and more!

Are you cynical about cultural tourism, but crave it?
ArtsHub takes a closer look at how tourism trends for 2025 are intersecting with museum offerings, and authentic specialist-led tours.

On the move: latest arts sector appointments
Our weekly round-up of Australian arts sector comings and goings, including a changing of CEOs at SALA and a new…
Richard Watts

Queensland election: The Greens’ vision for the arts in the state
Publicly-owned spaces for creative activity, a living wage for artists and addressing the cost of living crisis are key platforms…
Amy MacMahon
Want more content.
Get free newsletters full of the best in Australian arts news, jobs and more delivered to your inbox!
Numbers, Facts and Trends Shaping Your World
Read our research on:
Full Topic List
Regions & Countries
- Publications
- Our Methods
- Short Reads
- Tools & Resources
Read Our Research On:
Harris, Trump Voters Differ Over Election Security, Vote Counts and Hacking Concerns
Just 20% of voters are highly confident the supreme court would be politically neutral if it rules on legal issues in 2024 election, table of contents.
- Other findings: Voters’ plans for casting ballots, confidence in Supreme Court to be politically neutral if it must resolve 2024 election challenges
- Confidence in poll workers, state election officials
- Are the parties committed to fair and accurate elections?
- GOP confidence in absentee ballot counts remains low
- 2. Confidence in voting access and integrity; expectations for whether and when the election results will be clear
- How easy will it be to vote this year?
- Acknowledgments
- The American Trends Panel survey methodology

Pew Research Center conducted this study to understand Americans’ views of voting and their expectations around the 2024 presidential election.
For this analysis, we surveyed 5,110 U.S. adults – including 4,025 registered voters – from Sept. 30 to Oct. 6, 2024. Everyone who took part in this survey is a member of the Center’s American Trends Panel (ATP), a group of people recruited through national, random sampling of residential addresses who have agreed to take surveys regularly. This kind of recruitment gives nearly all U.S. adults a chance of selection. Surveys were conducted either online or by telephone with a live interviewer. The survey is weighted to be representative of the U.S. adult population by gender, race, ethnicity, partisan affiliation, education and other factors. Read more about the ATP’s methodology .
Here are the questions used for this report , the topline and the survey methodology .
With voting underway in the 2024 presidential race, majorities of American voters are at least somewhat confident that the election will be run smoothly, that votes will be counted accurately and that ineligible voters will be prevented from casting ballots.
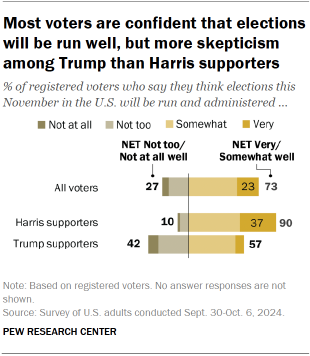
But supporters of Kamala Harris and Donald Trump have sharply different expectations for how this year’s election may unfold. In many cases, these differences are as wide as they were in the lead-up to the 2020 election .
Harris supporters are more optimistic about the way the election will be run: 90% say they are at least somewhat confident that elections across the United States will be administered well. This compares with 57% of Trump supporters who are confident the election will be run smoothly.
This pattern in views extends to other aspects of the presidential race:
- Harris supporters are more confident than Trump supporters that, after all the votes are counted, it will be clear who won (85% vs. 58%).
- Harris supporters are much more confident that mail-in ballots will be counted as voters intend (85% vs. 38%).
- Harris supporters also are more confident that election systems across the U.S. are secure from hacking and other technological threats (73% vs. 32%).
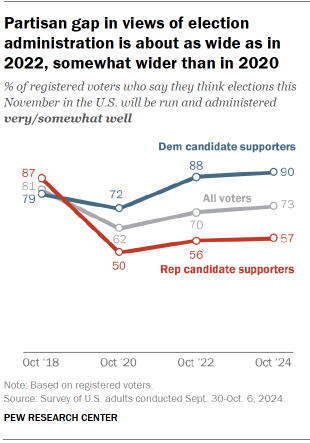
The latest national survey by Pew Research Center, conducted among 5,110 U.S. adults (including 4,025 registered voters) from Sept. 30 to Oct. 6, 2024, finds that voters who support Harris are more confident in the way the 2024 election will unfold than President Joe Biden’s supporters were four years ago.
And those who support Trump are deeply skeptical about the way the election will be conducted – expressing even less confidence on some election issues than his supporters did four years ago.
Wide partisan gaps in election confidence since 2020
In 2018, Republican candidate supporters were 8 percentage points more likely than Democratic candidate supporters to say that year’s midterm election would be run well. By 2020, Biden’s supporters were 22 points more likely than Trump’s to expect the election to run smoothly. The gap this year is even wider: 33 points between Harris and Trump supporters.
Harris, Trump supporters differ on whether votes will be counted accurately
As was the case four years ago, Trump supporters are particularly skeptical that absentee and mail-in ballots will be counted as voters intend.
Harris supporters are more than twice as likely as Trump supporters to say they are very or somewhat confident that absentee and mail-in ballots will be counted accurately (85% vs. 38%).
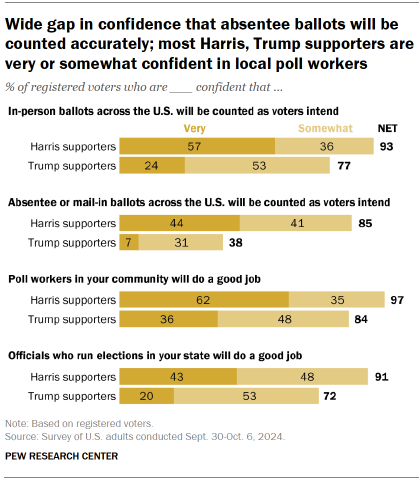
By contrast, sizable majorities of both coalitions (93% of Harris supporters, 77% of Trump supporters) are at least somewhat confident that in-person votes will be counted accurately.
However, far more Harris (57%) than Trump (24%) supporters are very confident this will happen.
There is broad confidence among voters overall that local poll workers and state election officials will do a good job during the upcoming election.
Yet Harris supporters are more likely than Trump supporters to express a high degree of confidence in these administrators.
Read more on views of election administration and vote counting in Chapter 1
Related: Key facts about U.S. poll workers
Voters’ views of illegal voting, access to voting
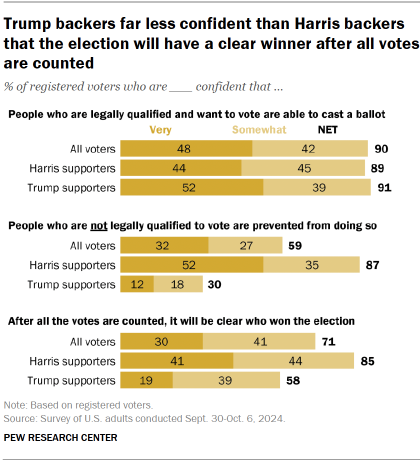
Roughly nine-in-ten among both Trump and Harris supporters are confident that eligible voters will be able to cast a ballot if they want to.
But there are bigger divisions on whether people who are ineligible to vote will be prevented from doing so.
Today, 87% of Harris voters are at least somewhat confident that ineligible voters will be prevented from casting ballots. Just 30% of Trump supporters say this.
Most voters are at least somewhat confident that it will be clear which candidate won the election after all the votes are counted. But here again, Harris backers (85%) are much more likely than Trump supporters (58%) to express confidence that the winner will be clear.
Do voters think election systems in the U.S. are safe from hacking?
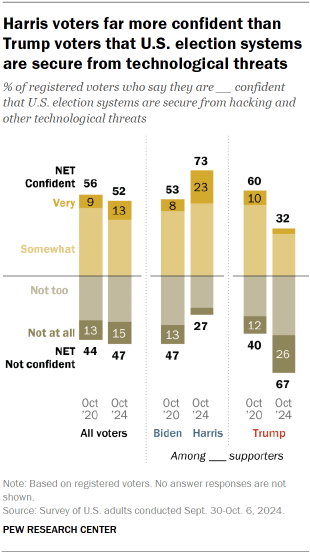
Overall, 52% of voters are at least somewhat confident that U.S. election systems are secure from hacking and other technological threats. Nearly as many voters (47%) are not confident about this.
- 73% of Harris supporters say they are confident that election systems are secure. This is higher than the share of Biden supporters who said this in the weeks before the 2020 election (53%).
- The pattern is reversed among Trump supporters: 32% now say election systems are secure from hacking and other technological threats, down from 60% four years ago.
A smaller share of voters plan to cast ballots by mail compared with 2020. Four years ago, during the COVID-19 pandemic, a record share of voters cast ballots by mail in the presidential election . Today, a much smaller share of voters plan to vote by mail (39% then, 28% today). But as in 2020 amid the Biden-Trump matchup , Harris supporters are about twice as likely as Trump supporters to say they plan to cast a ballot via mail.
Read more on voters’ expectations around voting in Chapter 3
Trump backers who plan to vote by mail are more confident that mail-in ballots will be counted accurately. Though most Trump supporters plan to cast a ballot in person, 17% say they plan to vote absentee or by mail. These voters express far more confidence in the accuracy of mail-in ballots than do those who plan to vote in person (67% vs. 31%).
Most voters are not confident the Supreme Court would be politically neutral if it had to resolve legal challenges related to the 2024 election. Overall, just 20% of voters are extremely or very confident the court would remain politically neutral if it had to resolve any legal challenges that stemmed from the 2024 election. But Trump voters express more confidence than Harris voters do (34% vs. 6%).
Sign up for our weekly newsletter
Fresh data delivery Saturday mornings
Sign up for The Briefing
Weekly updates on the world of news & information
- Election 2024
- Election System & Voting Process
- Supreme Court
- U.S. Democracy
Most Voters Say Harris Will Concede – and Trump Won’t – If Defeated in the Election
How voters expect harris’ and trump’s policies to affect different groups in society, in tight u.s. presidential race, latino voters’ preferences mirror 2020, americans in both parties are concerned over the impact of ai on the 2024 presidential campaign, americans view walz more positively than vance, but many aren’t familiar with either vp nominee, most popular, report materials.
- Questionnaire
901 E St. NW, Suite 300 Washington, DC 20004 USA (+1) 202-419-4300 | Main (+1) 202-857-8562 | Fax (+1) 202-419-4372 | Media Inquiries
Research Topics
- Email Newsletters
ABOUT PEW RESEARCH CENTER Pew Research Center is a nonpartisan, nonadvocacy fact tank that informs the public about the issues, attitudes and trends shaping the world. It does not take policy positions. The Center conducts public opinion polling, demographic research, computational social science research and other data-driven research. Pew Research Center is a subsidiary of The Pew Charitable Trusts , its primary funder.
© 2024 Pew Research Center

IMAGES
VIDEO
COMMENTS
Here are Computer Weekly's top 10 cyber crime stories of 2021: 1. Colonial Pipeline ransomware attack has grave consequences. Though it did not trouble the fuel supply at petrol stations in the ...
The social media company said it found and fixed the issue in August 2019 and its confident the same route can no longer be used to scrape that data. "We don't currently have plans to notify users ...
Everything We Know About Facebook's Massive Security Breach. Up to 50 million Facebook users were affected—and possibly 40 million more—when hackers compromised the social network's systems ...
"Social-media manipulation is one of their favourite tools. "So this hack shows just how vulnerable social-media platforms are and how vulnerable Americans are to disinformation.
Hacking, social engineering, spear phishing, cybersecurity, risk management, teaching case . Cover Page Footnote . The authors appreciate the productive feedback provided by the reviewers and journal editors, as well as family members. This article is available in Journal of Cybersecurity Education, Research and Practice:
Dmitri Alperovitch, who co-founded cyber-security company CrowdStrike, told Reuters news agency: "This appears to be the worst hack of a major social media platform yet."
The Impact Team said it decided to publish the information because ALM "profits on the pain of others," and in response to a paid "full delete" service Ashley Madison parent firm Avid Life ...
Big Number. 323,972. That is the total number of complaints of social engineering attacks received by the FBI in 2021—almost three times higher than what it was in 2019—according to the agency ...
A few days later, a seventeen-year-old hacker from Florida, who enjoyed breaking into social-media accounts for fun and occasional profit, was arrested as the mastermind of the hack. The F.B.I. is ...
In theory, most of the data being compiled could be found by simply picking through individual social media profile pages one-by-one. Although of course it would take multiple lifetimes to gather ...
1. $100 Million Google and Facebook Spear Phishing Scam. The biggest social engineering attack of all time (as far as we know) was perpetrated by Lithuanian national, Evaldas Rimasauskas, against two of the world's biggest companies: Google and Facebook.
U-M Social Media. Hacked: A Case Study. There's no denying it: we got hacked. Here's what we learned and what you can learn, too. On Wednesday, August 12, at approximately 3:30am, a barrage of malicious postings found their way to three of the University of Michigan's most popular Facebook pages: Michigan Football, Michigan Basketball ...
The casual, public Wi-Fi hack; Customer support falls prey to a social engineering hack; Hotel managers and clients had nightmares due to one lock hack posted; Cyber security incidents and getting hacked seem like distant, fascinating things where other people get hurt, but you stay safe. Truth is, getting hacked or scammed can happen to anyone ...
Internet Ethics Cases. Find ethics case studies on topics in Internet ethics including privacy, hacking, social media, the right to be forgotten, and hashtag activism. (For permission to reprint articles, submit requests to [email protected].) A fitness tracker aimed at children raises issues of design ethics, incentives, and more.
Attackers can get the passwords they use in password spraying from common wordlists. Wordlists are a list of passwords usually gotten from data breaches. The larger the wordlist, the higher the chances of compromising any account. Below is a screenshot of the infamous rockyou.txt wordlist from the RockYou hack of 2009.
The latter have purposefully not been included in the list. So, here it is - an up-to-date list of the 15 biggest data breaches in recent history, including details of those affected, who was ...
2014.2 Yet despite its media and technology expertise, the global corporation had earned a reputation within the hacking community for poor information security. Denizens of online message boards even coined a term coined at the companys expense: Sownage, which loosely translates to an act of defeat - getting
The following ethical hacking case study is six instances where ethical hackers were able to save a company from dealing with data leaks and suffering huge financial losses. Case Studies of Ethical Hacking 1. A crack in WordPress leaked user information. Back in 2019, a new plugin was released for WordPress called Social Network Tabs.
Rise of social media hacking devastating creative small businesses. A timely warning for all creative professionals: social media account hacking is rising, and your small business may be more vulnerable than you think. Creatives can face massive losses if their social media accounts are hacked, often with little recourse to reinstate their data.
In the digital era dominated by social media, understanding the impact of User-Generated Content (UGC) on brand perception is indispensable for businesses. This study explores the nuanced dynamics of UGC, focusing on its positive impacts such as authenticity, increased brand awareness, and improved brand image. It also addresses challenges, including negative UGC and the need for quality control.
The latest national survey by Pew Research Center, conducted among 5,110 U.S. adults (including 4,025 registered voters) from Sept. 30 to Oct. 6, 2024, finds that voters who support Harris are more confident in the way the 2024 election will unfold than President Joe Biden's supporters were four years ago.